Understanding Cloud Security & Privacy in 2025: Encryption, Data Collection & More
Cloud storage can free up space on your hard drive and protect your files from hardware failures that might happen to your device. However, you need to make sure the cloud service you’re using is secure. Read on for our in-depth guide on cloud security.
One of the main benefits of cloud storage is keeping a copy of your data somewhere other than your computer. Physical devices are prone to failure, and laptops can easily get lost or stolen. Keeping a cloud backup of your files is key to any good data protection strategy, which is why cloud security is extremely important.
Key Takeaways:
- When choosing a cloud storage service, your top priority should be choosing one with good security and privacy.
- Zero-knowledge encryption is the first cloud security feature you should look for in a service. It ensures that only you can access your data.
- Before settling on a cloud storage service, read through its privacy policy, focusing on the personal data it collects.
Below we’ll go into the most important things you need to know about cloud security, but first we’ll address why you need it. The internet is dangerous, and you could easily fall victim to cybercrime. Hackers can target your data and hit you with ransomware, intercept your traffic on public WiFi or steal your credentials. It’s important to have strong security measures in place to prevent that.
The good news is that deflecting crime in the cloud is pretty easy, as long as the cloud service you’re using has all the necessary security features to keep your data safe. Let’s take a closer look at what those features are.
-
01/17/2022 Facts checked
Cloudwards.net rewrote this article to take a fresh look at cloud security.
Cloud Security Basics
Cloud security is one of the most important aspects of a cloud storage service. Keep in mind that security and privacy are not the same thing.
Take Google Drive, for example. It has Google’s billions to back it up, and likely has the most robust security system out there. It’s highly unlikely that your account could get hacked and your files decrypted, unless you happen to lose your password and don’t have 2FA enabled.
Google Drive is probably one of the most secure cloud services, but it’s also one of the least private, since it scans everything you upload and otherwise squeezes as much data out of you as possible.
With that out of the way, let’s look at what cloud security features you should expect from a cloud service.
Cloud Security: Encryption & Protocols
A Cliffs Notes version of encryption would be that it scrambles your files into unrecognizable strings of ones and zeros. To become encrypted, the file needs to go through an encryption protocol. The protocol uses an encryption key, which is just a randomized string of characters (the seed for the randomization is usually your password).
At-Rest and In-Transit Encryption
Most cloud services nowadays encrypt your data. They usually encrypt it twice — at rest and in transit — and each serves a different purpose. At-rest encryption is what we usually refer to when discussing encryption. If your files are encrypted while they’re stored on a cloud company’s servers, that’s at-rest encryption.
In-transit encryption refers to encrypting your data from the moment it leaves your device until it reaches the cloud server. Not all cloud service providers encrypt your data in transit, which can leave your traffic vulnerable if you’re on an unsecured network, like public WiFi.
Encryption Protocols
There are many encryption protocols ranging from the old DES to the newer Twofish and AES. AES is the most secure of the lot (or at least the most commonly used), as you can read in our AES guide. It has several levels of security, depending on the key length, which can be 128, 192 or 256 bits.
While AES-256 is the gold standard of cloud security, other security protocols like Twofish are also acceptable, so long as they’re proven to be secure and have no known vulnerabilities. AES-128 is technically less secure than AES-256, but both are practically uncrackable. These protocols are typically used for data at rest.
During transfer, cloud storage services tend to use the TLS protocol to protect your files from eavesdropping. It establishes a secure connection by performing a handshake between two machines using a cipher, authentication and a key exchange, then encrypts the data using AES.
Zero-Knowledge Encryption
Zero-knowledge encryption is the biggest boon you could get from a secure cloud service. This is more of a privacy feature, although it’s tied to the strictly technical aspect of a service’s security. We also refer to it as client-side encryption, end-to-end encryption or private encryption. You can find recommendations for services with private encryption in our best zero-knowledge cloud services article.
Generally, the cloud service will hold your encryption key to provide faster service. This also means that you lose some privacy, because the service will also be able to decrypt and read your files.
If a cloud service is zero-knowledge, it means that only you have access your encryption keys. All encryption happens on your device, and the service only receives encrypted files. When you want to access them, the files get decrypted using your encryption key.
You also need to keep in mind that zero-knowledge services can’t reset your password. To mitigate the risk of losing your password, consider using a password manager. Regardless, make sure that you create a strong password.
We mentioned that non-zero-knowledge companies hold your encryption key themselves to provide easier service. This is because zero-knowledge can interfere with things as simple as providing file previews. Collaboration is the most hampered by zero-knowledge encryption, and requires genuine innovation to make it work in a zero-knowledge environment (Sync.com does this with its Office integration).
This is one reason why zero-knowledge isn’t universally adopted. Another reason is that large companies like Google (the largest personal cloud storage provider by a country mile) actually want to be able to decrypt your files, and possibly even scour them for data or hand them over to authorities, if subpoenaed.
Other Cloud Security Solutions
In addition to strong encryption and protocols, robust cloud security should include other security controls, such as two-factor authentication, server security and ransomware protection to keep sensitive data safe.
Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA)
This should be a necessity for virtually every service you use, and cloud services are no exception.
Two-factor authentication makes it so whenever you attempt to log in to your account, you need to approve the login, either by email, SMS or an authenticator app like Google Authenticator. This stops intruders from getting into your account, even if they get a hold of your login details.
Server Security
Cloud-based security sometimes means physical security. Cloud services secure data in physical servers, which also need to be protected. For instance, businesses may choose to utilize cloud storage for CCTV footage whereby cloud services are used to secure data in physical servers.
You’re a lot less likely to find data on a service’s server security, but if you do, it’s always a plus. For example, Sync.com’s servers are under 24/7 surveillance and are protected against natural disasters. Data centers should be physically protected from break-ins or natural disasters, and cloud services should have disaster recovery plans in place.
Ransomware Protection
Ransomware is no joke. It’s a type of malware that finds your sensitive files and encrypts them so that you can’t access them anymore. If you want to access your files again, you have to pay the hackers a ransom to get the special decryption key from them — that is, if they deliver it at all. It’s better not to fall victim in the first place. That’s where cloud services come into play.
Some online backup solutions include ransomware protection with their software, like Acronis Cyber Protect. In our best online backup with ransomware protection piece, we list six services that perform well against it.
Cloud storage solutions use versioning to fight ransomware. Versioning allows you to keep several past versions of files, which means you’ll always have an uninfected version to fall back on. Many have it, but the implementations differ in the number of versions or days you can roll back. Sync.com is our top cloud storage with versioning (read our Sync.com review).
Cloud Storage Privacy
Data security extends beyond encryption and security measures. Privacy is also a factor. However, assessing how private a cloud service is requires a bit of sleuthing. There are multiple factors to consider, including jurisdiction, privacy policies, terms of service, company history (including data breaches), GDPR compliance and more.
Some of the privacy factors can be nebulous or confusing. We’ll try to explain them as best we can, but you still might run into a brick wall of obtuse legalese when reading a company’s privacy statement.
Jurisdiction
This is one of the simplest aspects of privacy. Where is a service located? Is it in the EU, which has good privacy laws? Or is it, say, in the Netherlands, which is also in the EU, but also has one of the largest wiretapping apparatuses in Europe?
Is it in the U.S., which has a ton of surveillance laws, like the Patriot Act? Is it in China, which is downright autocratic? Or is it in Switzerland, which arguably has the best privacy laws in the world?
Here’s a list that we’ve compiled regarding cloud privacy laws around the world that you can use as a guide.
There’s also the matter of a country’s Five Eyes membership (or Nine Eyes, or 14 Eyes) — the intergovernmental espionage ring that allows members to share intelligence among themselves. However, Five Eyes membership is a bit less concerning than if the country is independent of those entities, yet has draconian surveillance laws — like Saudi Arabia, for example.
However, all in all, a country’s jurisdiction should take a backseat to actual company policy.
Privacy Policies and Terms of Service
Analyzing a cloud service’s privacy policy can be tricky, but it’s easier if you know what to focus on, and that’s the disclaimer on data collection. Essentially, you need to check if it collects any identifying data or just necessities, like billing information.
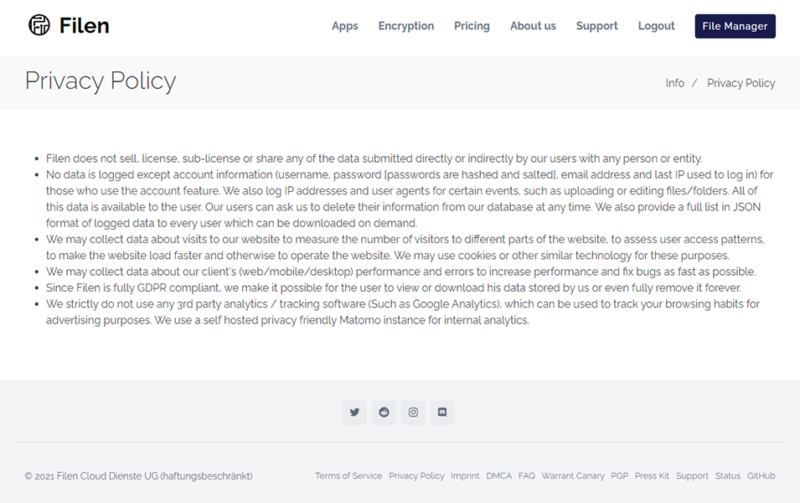
You could have a service like Filen, which doesn’t mince words in its policy. It simply states that it doesn’t want your data and tries its best to stay away from ever looking at it unless absolutely necessary (read our Filen review).
On the other hand, companies like Google, Apple and Microsoft used to have notoriously dense privacy policies, which were inaccessible to people without a background in law and a few hours to spare.
The companies have since improved how they present their privacy policies and terms of use, but the documents are still enormous, mostly owing to the exorbitant amounts of data these companies collect.
Company History: Leaks & Data Breaches
There’s also the matter of an individual company’s past. For example, Google was caught breaking its own promises about privacy when it was discovered that people were allowed to listen to its Google Home recordings in a Belgian case from 2019. Remember, even if a company has a rock-solid privacy policy on the surface, it could mean nothing if it has a dodgy past.
In particular, look for leaks that the company has had, like Dropbox’s many leaks, or iCloud’s celeb photo dump, although cases like Google’s situation above are particularly damning.
Also, always be skeptical of companies that get money from advertising, as they’ll try any way possible to squeeze more data out of you (especially if it’s a large company like Google or Microsoft).
GDPR Compliance
The General Data Protection Regulation (GDPR) is an EU law that protects user data. However, the law has a reach far greater than the EU, and affects any company that wants to do business with European citizens (i.e., most companies in the world). Some companies forgo certain aspects of the GDPR while staying sufficiently compliant, while others go even further.+
We’ll take Filen as an example again. If you ever want to delete your account, you can make sure Filen doesn’t keep a single iota of your data by asking it to delete everything it has on you. It can even give you a full report detailing everything the company knows about you.
It’s best that these features are available easily and obviously, although some companies might make you jump through hoops to realize your GDPR rights.
Some cloud services also comply with other privacy standards like HIPAA, which regulates control of medical data, and it requires very strict security and data management.
However, just because a service is HIPAA-compliant doesn’t mean it’s inherently secure. It merely means it gives you the tools that can allow you to use the service in a HIPAA-compliant manner. Actual compliance measures fall on the user to implement.
Sharing-Content Control
One of the main benefits of cloud services is sharing. Most services take a similar approach by allowing you to generate links to files or folders or invite others to collaborate with you. Where they differ the most is the ability to restrict and control your shared content. Proper content control can include password protected links, expiry dates, folder permissions, key management and more.
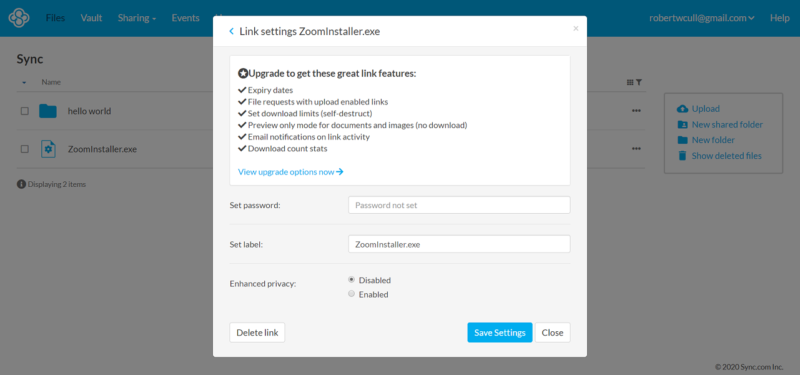
We’ve narrowed our choices down to five services in our best cloud storage for sharing article. It should come as no surprise that Sync.com and pCloud are at the top because they offer strong content control (read our pCloud review). MEGA encrypts all sharing links, and you can decouple the decryption key to send it via a secure channel (read our MEGA review).
Final Thoughts: Cloud Security
Cloud security isn’t a trivial matter, especially if you keep sensitive information in the cloud. We listed the most important security and privacy features cloud services should have to keep your data safe.
If you care about your data’s security, you should always choose a zero-knowledge cloud storage service. If secure collaboration is what you need, you also need a service with adequate sharing features, like password protection and expiry dates for sharing links. Also, try to at least skim through a service’s privacy policy for any suspicious data collection clauses.
What do you think about cloud security? Which secure cloud storage service is your favorite? Do you already use a zero-knowledge cloud service? Please let us know in the comments below. As always, thank you for reading.
FAQ
No, cloud storage isn’t inherently any less secure than traditional storage. If anything, the cloud is more secure because it isn’t susceptible to hardware failure or theft, as long as you’ve chosen a secure cloud service.
You need to look for strong cloud security features, like zero-knowledge encryption and two-factor authentication. You also need to use a strong password and keep it safe.
Cloud security is important because a cloud provider will hold a lot of customer data. There are security risks involved for cloud users with having this valuable data online, but with proper security tools and encryption, these cloud providers can mitigate the dangers of security threats and create a trustworthy cloud environment.


