Encryption Guide: Meaning, Types, Techniques & Benefits Explained in 2025
It’s important to keep our personal information secure, and encryption is one of the best ways to protect data. This encryption guide explores how data encryption works, top data encryption techniques and the best ways to safeguard sensitive data.
Encryption is one of the best tools for protecting your data. It’s used in many day-to-day applications — texting apps, cryptocurrency, the top VPNs, password managers and email security, to name a few. However, it’s not always clear what encryption really is or how it works. We’ll take an in-depth look at encryption in this guide.
After reading this guide, we hope you’ll have a firm understanding of why encryption is so vital for keeping our data safe. We’ll go over the basics, breaking down the complex nature of algorithms, key management and data encryption solutions, and then give you some advice on best practices to ensure your data remains encrypted.
-
10/24/2024 Facts checked
We’ve rewritten this article to include in-depth explanations of the importance of encryption, different types of encryption and algorithms, and best practices.
Encryption Meaning: What Is It?
Encryption is the process of turning readable (plaintext) data into a coded format (ciphertext), making it indecipherable to anyone who doesn’t have the decryption key. Encryption uses algorithms that scramble information in a variety of ways — some very simple, and others so complex it’s impossible to crack them with brute force.
Encryption can take place when files are in transit (moving between devices or from one storage area to another) or when they are at rest (in the storage area).
What Is Data Encryption?
The term “data encryption” is often used synonymously with “encryption.” Both refer to converting information from easily readable text to a coded ciphertext. Information doesn’t have to be digital, but we’ll assume it is for this article. Digital information includes items such as files, emails, login credentials, database entries or website requests.
How Does Encryption Work?
Encryption works by turning plaintext data into ciphertext using encryption algorithms. Algorithms are complex sets of rules that make data unreadable, transforming it in accordance with mathematical models.
The data only becomes readable again when the appropriate decryption key is used to turn it back into plaintext data. This is one way of ensuring only the intended recipient or user can access the data.
Decryption keys are generated as part of the algorithm, either in pairs for public-key encryption or as a single key for a symmetric encryption algorithm. The browser or security app you’re using will typically share the decryption keys — manual sharing or exchange isn’t required.
Encryption in Transit and at Rest Key
Encryption at rest and in transit refers to two crucial states of data protection — when data is being stored and when it’s being transferred.
Encryption at rest secures data when it’s in storage, such as on your device or on a cloud server. A secure communication channel isn’t required, so data at rest is usually encrypted with a single key and decrypted with the same key.
Data in transit typically uses two different types of keys. A symmetric key is used to encrypt the data itself, and a public-private key pair is used to encrypt the symmetric key. This ensures the data is unreadable to unauthorized parties while remaining decryptable for the recipient.
Popular protocols for securing data in transit include Secure Sockets Layer (SSL) and its updated version, Transport Layer Security (TLS). These protocols establish a handshake between your device and the site to encrypt, secure and authenticate the connection before any data is transferred.
Once the handshake has established the authentication and exchanged the decryption key, a secure connection is opened for data to travel through. You can read more about these protocols in our SSL vs TLS guide.
Importance of Encryption
Encryption protects private and confidential data, both on the device and when it’s moving between devices or cloud storage services. Here are some of the main reasons why encryption is important for both individuals and companies.
Privacy
Data encryption ensures no unauthorized users can read or access data at rest or in transit, such as hackers, your ISP or even government agencies. Only the data owner or the intended recipient can read the information.
Protecting Data as It Moves
Data is vulnerable to interception when it moves between devices, whether that entails sending messages and emails, approving financial transactions, or entering or leaving cloud storage. If data travels unencrypted, hackers can target it through a man-in-the-middle (MitM) attack and secretly monitor or copy it.
Data Integrity
MitM attacks can also alter unencrypted data without the sender’s or recipient’s knowledge. Data encryption maintains integrity by assigning all ciphers a hash value, which describes the specific way the text has been encrypted. If the encryption is altered, the hash value changes and the recipient will know the text has been tampered with.
Compliance Regulations
Many industries, including government agencies, have strict regulations about storing and sending data. More specifically, all data relating to customers must be securely encrypted to maintain user privacy. Examples of laws that require a specific level of data encryption are the GDPR (EU data protection) and HIPAA (U.S. healthcare industry).
Types of Encryption: Basic Methods
There are two basic methods of encryption: symmetric encryption and asymmetric encryption. In symmetric encryption, the encryption key is the same as the decryption key, while in asymmetric encryption, the two keys are different.
Symmetric Encryption
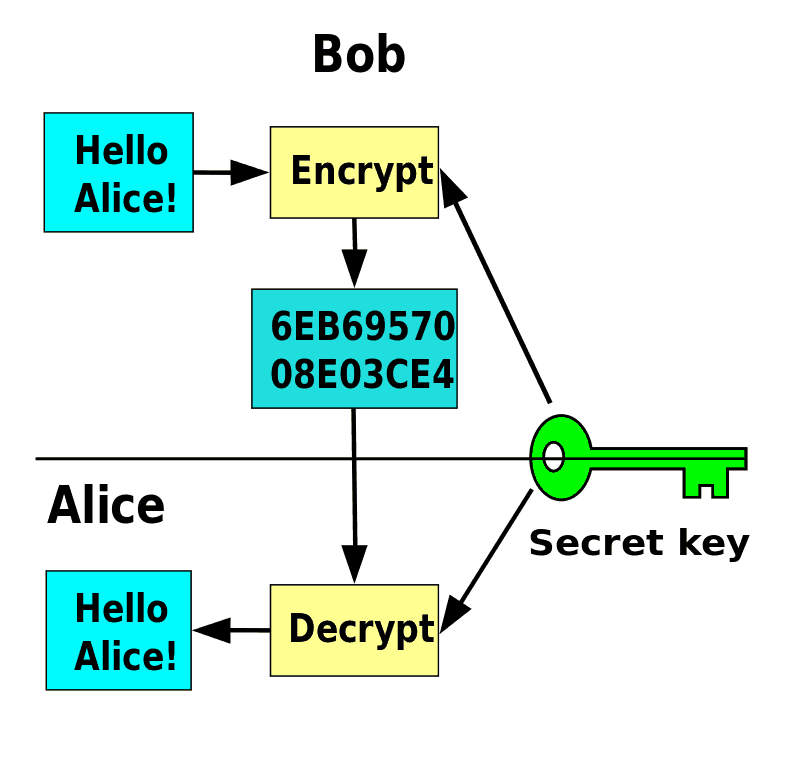
Symmetric encryption is also known as a shared-key or private-key algorithm. The symmetric encryption algorithm involves using the same key for both encryption and decryption. The nature of symmetric-only data encryption algorithms makes them better suited to data at rest than to data in transit.
The symmetric encryption method is less costly and labor-intensive to produce, but it is a slightly riskier option. If an unauthorized party obtains the private key, it’s easy to decrypt the data. In transit, symmetric encryption almost always begins with a secure key exchange using an asymmetric encryption method.
Asymmetric Encryption
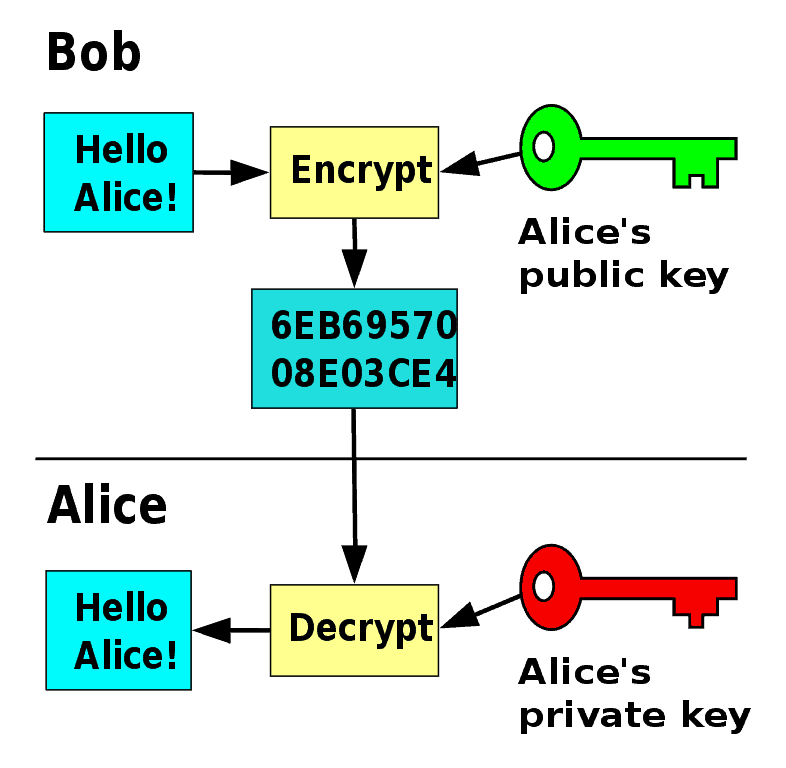
An asymmetric encryption algorithm involves creating a key pair, with one key for encryption and a matched key for decryption. This is also known as public-key cryptography, because the encryption key is a public key that anyone can use.
Only users who have a second, private key paired with the public key are able to decrypt the data. Because it never leaves the destination device, the private key remains much more secure.
This type of data encryption is slower, but it’s a better option for encrypting data in transit. Many algorithms — notably, SSL/TLS — use the more secure asymmetric encryption to exchange a symmetric key, then use that key to more quickly encode the actual data.
Encryption Algorithm Examples
Below, we provide two examples of secure and common symmetric encryption algorithms:
Advanced Encryption Standard (AES)
- Secure communications: AES, which we explore in our “What Is AES?” article, is used to encrypt messages (data at rest) on apps like WhatsApp, Signal and Telegram. Other secure protocols protect data in transit.
- Virtual private networks (VPNs): AES is a popular choice among virtual private networks to encrypt data. The symmetric encryption occurs after the secure VPN connection is established with an asymmetric handshake. A VPN protocol like OpenVPN contains the instructions to accomplish all this.
- Disk and file encryption: Software like FileVault and cloud storage services like Dropbox use AES data encryption.
Twofish
- Password managers: Twofish is a natural fit for password managers, which prioritize high-quality and robust security over speed (Twofish’s complexity makes it a slower encryption algorithm).
- OpenPGP (Pretty Good Privacy): OpenPGP tools use Twofish to electronically encrypt and sign emails and files.
The following examples are two common asymmetric encryption methods:
RSA (Rivest Shamir Adleman)
- Digital signatures: RSA verifies message authenticity and integrity by creating a digital signature with the sender’s private key that can be verified by a public key.
- Website certificates: RSA authenticates websites using certificates signed by trusted authorities to confirm the website’s identity before the browser connects.
- Email messages: RSA is used in secure email systems, encrypting emails so only the intended recipient can read them and certifying message integrity.
Elliptic Curve Cryptography (ECC)
- Cryptocurrency digital signatures: ECC is used to create digital signatures for cryptocurrencies like Ethereum and Bitcoin.
- Mobile device security: With shorter secret-key lengths, ECC is a more efficient and faster algorithm, making it optimal for mobile devices.
Data Encryption Standards
Two important data encryption standards guide how these algorithms are used, particularly in companies and organizations.
NIST Federal Information Processing Standard (FIPS) 140-2
The FIPS standard sets the security requirements necessary for protecting sensitive data with encryption. It’s designed to ensure encryption and algorithms clear a high security bar.
Requirements include keeping keys stored safely and taking measures to prevent cyberattacks. FIPS also outlines different security levels depending on the potential risks and the value of the secured data.
Common Criteria (CC) for Information Technology Security Evaluation
CC isn’t strictly an encryption standard but rather provides a set of guidelines for evaluating IT product security. Encryption wasn’t originally covered, but it’s becoming a larger part of the guidelines as network security increases in importance.
The goal of CC is to ensure the security claims that vendors make hold up when undergoing third-party testing. Products are tested at different levels of rigor and assessed based on CC security standards.
Best Practices for Effective Data Encryption
Best practices for data encryption will vary depending on whether you’re encrypting personal data or encrypting data for a large company that handles sensitive information. However, there are a few key points to consider that apply to data encryption situations in general.
Final Thoughts
For the most part, encryption works quietly behind the scenes to protect our private data. However, knowing more about the how and why behind encryption systems means we can make better choices about who we share our data with and thus avoid nasty data breaches as a result of companies that don’t encrypt data the way they should.
Are you interested in any specific areas of encryption? Which advanced encryption algorithms would you like to know more about? What kinds of software do you think would benefit from better data encryption? Let us know in the comments below. As always, thanks for reading.
FAQ: Encryption Tutorial
The five components of encryption are plaintext, an encryption algorithm, a secret key, ciphertext and a decryption algorithm.
Encryption changes readable (plaintext) data into unreadable (ciphertext) data using a cryptographic mathematical model called an algorithm. The ciphertext can be decoded only with the correct decryption key.
The three different encryption methods are symmetric, asymmetric and hashing. However, hashing isn’t strictly encryption, as it’s a one-way process and mostly used to authenticate data. Encrypted data can generally be decrypted, making it a two-way process.
The four most secure encryption techniques currently available are Advanced Encryption Standard (AES), Twofish, Elliptic Curve Cryptography (EEC) and RSA.


