SSL vs TLS: Know Your Protocols for 2024
Google is cracking down on website security. Starting with Chrome version 62, all websites with text input fields will need an SSL certificate or Google will mark the website as not secure with a red caution sign next to the URL.
The change comes at an interesting time, too, considering the recent push for browsers and servers to support TLS. However, if you’re new to the website-building game, all these abbreviations may be enough to make your head spin.
We’re here to clear up the confusion about SSL and TLS and show you how to keep your website in the green zone. We’ll compare what the security protocols aim to accomplish, go over the latest in encrypted connections and take you through purchasing a certificate for your website.
SSL vs TLS
SSL and TLS do the same thing. They’re encrypted protocols for data transfer. They work by establishing a handshake between two machines. The handshake includes the cipher, authentication and key exchange. Once that’s done, a secure connection is opened between the machines.
The data traveling between machines is then encrypted and fragmented to a certain size, depending on the cipher, and sent to the network transport layer. The cipher deals with the encryption, not the handshake. The SSL and TLS protocols are simply used to complete the handshake and agree on an encryption model.
What Are SSL & TLS?
SSL stands for “Secure Sockets Layer.” It was developed by Netscape and first released to the public in 1995. The public release was version two and hackers quickly found ways to break through it. A year later, Netscape released version three, which was considered secure for eight years.
In 2014, the POODLE attack made SSL 3.0 insecure, but no one knew it at the time. TLS (Transport Layer Security), which is a more secure version of SSL, was released in 1999 and came with a fall back mechanism to SSL 3.0 for backwards compatibility.
That compatibility was built in because the POODLE attack, a man-in-the-middle exploit, abused that backwards compatibility (to read more about MitM attacks, check out our article on the dangers of public WiFi).
TLS 1.1 came out in 2006 and 1.2 followed in 2008. TLS 1.2 is the current and most secure protocol, though 1.3 was approved earlier this year. We expect browsers and servers will support it soon.
The protocols are different, but not more so than the different versions of SSL. The same process is happening, a handshake between two machines, but the version of protocol determines how it happens.
The Backwards Compatibility Problem
The confusion around SSL and TLS comes from backwards compatibility. TLS 1.2 has remnants of earlier versions of SSL to make it compatible with outdated browsers. As such, many websites haven’t disabled the features that make a protocol such as TLS 1.2 unsecure.
That’s where TLS 1.3 comes in. It’s built to disable legacy features and speed up performance on a secure connection. Instead of agreeing on an encryption model, the server provides the encryption key with TLS 1.3. That, theoretically, makes the multiple downgrade attacks, which force the server to use an older protocol, obsolete.
The latest update is a push toward the modern internet, abandoning the outdated model established by early versions of SSL. Hopefully, within a few years, attacks like POODLE won’t be as much of a concern as they are today.
Using TLS on Your Website
The TLS protocol used for your website is dependent on the server you’re hosted on. The best web hosting providers use TLS 1.1 and 1.2 exclusively, with 1.0 generally reserved for website builders that do not include e-commerce.
The final version of TLS 1.3 was only published a few weeks ago, so it’ll take time before web hosts support it. Kinsta, for example, has already addressed the release of TLS 1.3 and is taking steps to implement it.
As long as you’re using an SSL certificate, your visitor’s connection will be encrypted. Despite the outdated naming scheme, certificates still work with the latest protocols, even TLS 1.3. The certificate itself doesn’t encrypt anything.
Certificates are simply used as a verification method. Different forms of SSL and TLS certificates show the level of trust a browser has for your domain. We’ll run through those in the next section.
If you have a certificate, whether it’s a free one from Dreamhost or a paid one from HostGator, your site can connect using the latest protocol that your server is using.
There are a couple ways to check that. The first is through your web host’s knowledgebase. GoDaddy, for example, has a small table showing which TLS version your server supports, depending on the hosting plan you’re on.
You can also test your web server using the SSL server test from SSL Labs. It’ll show you what protocol your server is using, as well as the encryption method, and give you an overall rating.
SSL and TLS Certificate Types
Once again, SSL certificates are better defined as “certificates that can use SSL and TLS,” so we’ll call them SSL certificates to avoid confusion for this section. Anywhere you read SSL or TLS without a protocol version, they will be the same thing.
Domain Validated Certificates
The most basic form of SSL certificate is a domain validated certificate, which checks against the domain registry. Essentially, it verifies that the domain a user is trying to access points to the correct DNS server.
It’s the cheapest certificate to get, often included in packages for free. Jimdo includes a Let’s Encrypt DV certificate for free, as do many website builders and web hosts.
DV certificates are high-risk, though, as browsers often can’t validate if the business on the website is legitimate. In Chrome, you’ll usually see the https protocol with a red lock with a slash through it to the left.
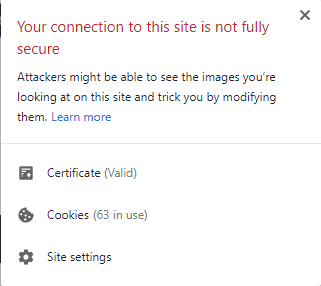
If you’re running a blog or a personal site, a DV certificate is fine, but if you request personal information, especially credit card info, you should be using something stronger.
Organization Validated Certificates
Organization validated certificates check against the business or organization. Agents from the Certificate Authority will check government registry databases to ensure the site is real. All the data inside an OV certificate is legitimate.
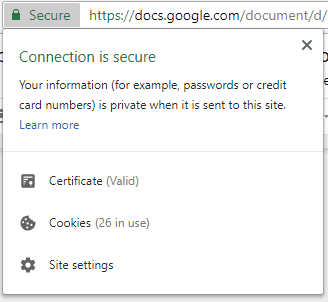
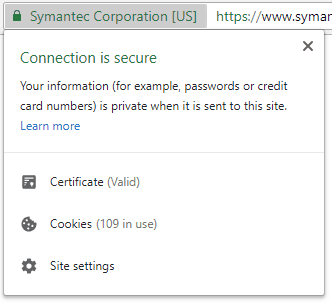
If you’re running a commercial business online, this is the certificate you need to use. Your URL still uses https, but there will be a lock next to the address bar. In Chrome, it’s green with the word “secure” to the right.
Extended Validation Certificate
OV certificates are good, but extended validation certificates are better. OV certificates require a single vetting from the CA, while EV certificates require continual monitoring based on the guidelines for extended validation.
The verification process is much stricter and the price is much higher. For major online outlets, though, an EV certificate can improve consumer trust and increase online sales.
For anything else, the certificate is largely unnecessary. Even major websites that don’t collect user information don’t use EV certificates. If you are using one, the browser will show a green address bar with a lock, along with the name of your company.
Final Thoughts
There is no shortage of confusing acronyms when it comes to cybersecurity and the change from SSL to TLS doesn’t help that. Though the protocols are different, they accomplish the same goal: a secure connection between the server and the user.
As far as certificates go, the terms are interchangeable, so don’t worry about upgrading an SSL certificate to a TLS certificate. They’re the same thing.
Is there anything else you’re curious about with SSL or TLS connections? Let us know in the comments below and, as always, thanks for reading.