VPN Security Guide: How to Stay Safe Online in 2025
Connecting to a VPN server will encrypt your traffic and hide your location, enabling secure access to the internet. In this article, we go behind the scenes and unpack how VPN security protects your data.
A VPN, which stands for “virtual private network,” can help you browse the internet safely. It encrypts your internet traffic, which can help protect you from many cyber threats and also mask IP addresses by substituting virtual locations. However, not all services offer strong VPN security, which is why you should carefully consider only one of the best VPNs.
In this article, we’ll dig deeper into VPN security and provide a behind-the-scenes glimpse of how VPNs work. We will also coach you on features to look out for when selecting a VPN.
-
05/01/2024 Facts checked
We rewrote this article to better explain how a VPN works in layman’s terms and added technical information for advanced users.
How Does VPN Security Protect Your Data?
A VPN protects your data by encrypting your internet connection to make it unreadable. When you type a URL into your browser while connected to a VPN, the request first goes to the VPN client, which creates an encrypted tunnel. Afterward, the VPN client forwards the data to the VPN server, which decrypts it and sends it to the website you’re trying to access.
Next, the website sends the requested data back to the server, which encrypts and sends it to the VPN client. The VPN client decrypts the data and sends it back to you. These processes happen in the blink of an eye, so thousands of data packets can be scrambled in a second.
1. VPN Encryption
Encryption refers to the process of scrambling your data to make it incomprehensible to a third party. Even if hackers intercept your encrypted traffic, all they’ll see is a jumble of confusing characters.
One of the most-used VPN encryption options is AES encryption. Short for “Advanced Encryption Standard,” AES is a block cipher that divides user data into blocks and applies keys to each block. The keys can be of different sizes: 128, 192 or 256 bits. AES-256 bit is the best because the larger the key, the longer it takes to crack. Our AES encryption breakdown has more information.
2. VPN Protocols
A VPN tunnel is an encrypted connection between your device and the internet that cloaks your online activity. The tunnel works by encrypting your traffic and wrapping it in unencrypted traffic. This encapsulation makes it impossible to read your data packets, but on its own, it also scrambles the data that directs the packet to its destination.
However, encrypted internet traffic can still find its destination using a set of rules known as a VPN protocol. Protocols enable two servers to exchange encrypted information even if they have not been set up to communicate before now. Most VPNs allow you to choose the protocol you prefer from their apps.
If you read our VPN protocol guide, you’ll notice that we recommend OpenVPN for general use since it provides an excellent mix of speed and security. WireGuard is a good alternative if you need fast speeds.
3. The VPN Server
A VPN server receives your encrypted data, decrypts it and sends it to the website you are opening. When your data goes through the VPN server, it changes your IP address to the server’s. For example, if you are physically in Germany but connected to a U.S. server, you will have a U.S. IP address.
Using a VPN to change your IP address lets you use the internet as though you were in that country. This can show you different libraries on streaming sites and give you access to content you couldn’t otherwise see.
When the website responds to your request, the VPN server encrypts it and sends it back through the VPN tunnel to your VPN client. The layer of encryption adds some latency to your traffic, which is why VPNs reduce your internet speeds. However, some VPNs are built well enough that the speed reduction is marginal, like those on our list of the fastest VPNs.
How to Choose a Secure VPN Provider
When choosing a secure VPN service, scrutinize its security and privacy features. Here’s a list of the features to look for:
- Encryption: Ensure your VPN uses AES-256 encryption, ChaCha20 or something similarly strong for a secure connection.
- Protocols: Choose VPNs with trustworthy protocol options, like OpenVPN or WireGuard.
- Kill switch: A secure VPN must have a kill switch to protect against accidental disconnection.
- Obfuscation: This feature hides the fact that you’re using a VPN, and it is important for places that might ban VPN use.
- No-logs policy: Your VPN provider shouldn’t collect or store personal details about you. RAM-only servers are good because any personal data that the VPN has is erased with every server reboot.
Best Practices: Key VPN Internet Security Features
There’s a VPN best practices guide created in what is known as VTI Principles. However, if you want to learn more about the features listed below, read our extensive guide on VPN features.
Are VPNs Safe?
VPNs are safe to use as long as they are secure and privacy-focused. A safe VPN has vital features such as AES-256 encryption, multiple protocol options, a kill switch and a strict no-logs policy.
VPN Security Risks & Issues
If you use a poor VPN, you could be exposing your traffic to malicious actors. Even a reliable VPN must be configured correctly to enjoy the best security. Here’s a summary of VPNs you should avoid.
- VPNs with no encryption: Some VPNs don’t offer any encryption, exposing your data to your internet service provider as though you were browsing without a VPN.
- VPNs with an unsecured protocol: Avoid outdated protocols like PPTP and L2TP. These protocols have weaknesses that hackers can exploit.
- VPNs with security weaknesses: Some VPNs have unaddressed flaws that can be used to infect your device with malware.
- VPNs with a shady background: Don’t use VPNs with a history of data breaches or sharing user information.
It’s worth noting that free VPN services often have the problems listed above. That said, there are some useful free services. If you want to use a free VPN, check our best free VPN list.
How Can You Do a VPN Security Test?
You can use Wireshark to test whether your VPN encrypts your traffic. Below, we’ve outlined some quick steps explaining how to check encryption with Wireshark. If you need more details, we have a full guide that explains how to use Wireshark.
- Connect to a VPN Server
Download and install the VPN you want to test and connect to a VPN server.
- Download and Install Wireshark
Visit Wireshark’s website and download the installation package for your device. Follow the installation prompts to set it up on your device.
- Visit an HTTP Website
Websites that start with HTTPS are encrypted using the Transport Layer Security (TLS) protocol. Open an HTTP website to ensure you’re testing encryption that comes from the VPN and not the website. HTTP Forever is a good option.
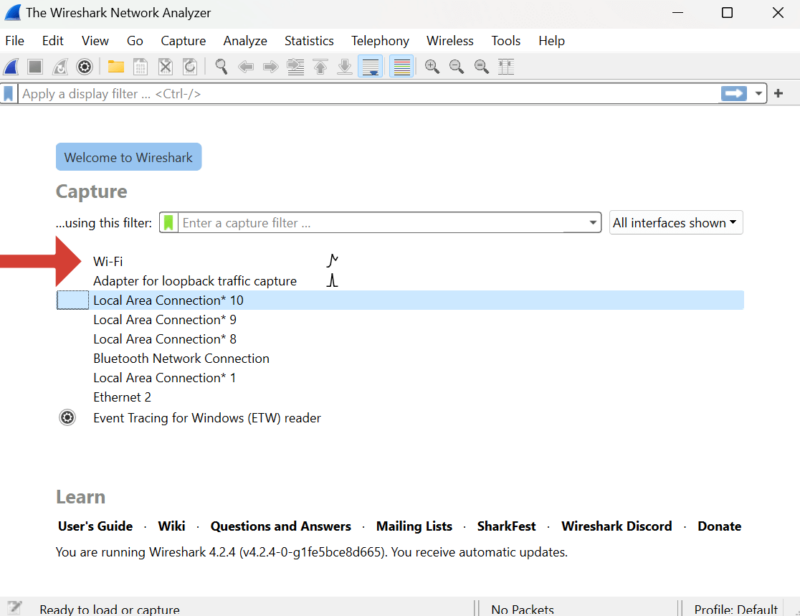
- Open Wireshark and Capture Packets
Launch the Wireshark app and click on your active connection. For instance, if you’re connected to WiFi, click “WiFi.” The packet capture will start automatically. We recommend pausing it after a few seconds; otherwise, you’ll capture more data than you need.
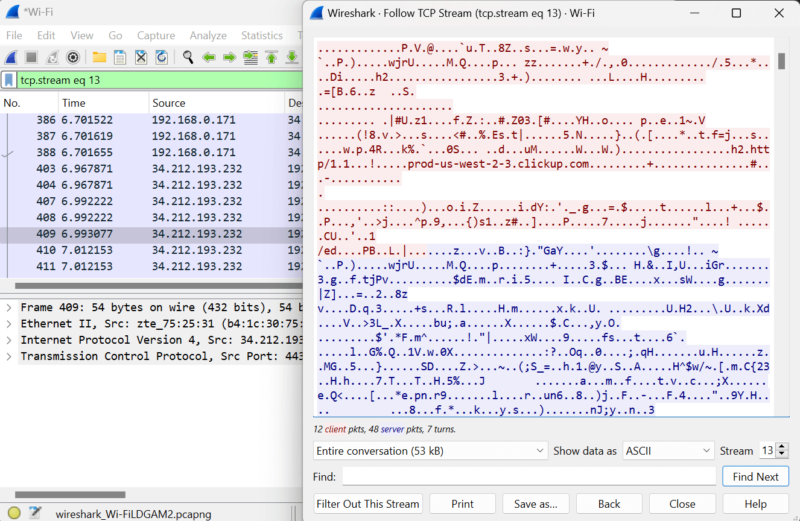
- Inspect the Packets
Pick a packet, right-click on it and click “follow.” Choose the UDP or TCP stream. The stream will open up. If you see any legible words, your VPN hasn’t encrypted your traffic. If you only see random characters, it means the VPN’s encryption works.
Final Thoughts: Virtual Private Network Security
A VPN can protect data from third parties, such as your internet service provider (ISP), hackers and governments. However, not all VPNs have the right security and privacy features to protect your network traffic. Ensure the VPN you choose has basic security features, such as AES encryption, OpenVPN and WireGuard protocols, a kill switch and a zero-logs policy.
Which VPN are you currently using? Does it provide the security and privacy you want? If you’re not using a VPN yet, which VPN would you consider? Did this article answer your questions about VPN security? Do you have any further questions or comments? Share your thoughts with us in the comments section below.
FAQ: Virtual Private Network Security
There are no laws against using a VPN at the workplace in the U.S. However, if your workplace has restrictions or guidelines on using a VPN, abide by them.
Commercial VPNs are most often used to get online safely. However, some businesses use a different sort of VPN in the form of an app that lets you access a secure network without being physically present. The encrypted tunnel is the same; it just has a different destination.
A VPN is worth it if you want to protect your privacy while you browse. It encrypts your internet traffic so no one can view it and hides your location. It can also give you a specific IP address to access geoblocked services like Netflix.
You need a VPN to protect your online privacy, so what you do online stays private, and for your online security, so hackers and third parties can’t potentially gain network access. It can also change your online location so you can stream geo-restricted content and avoid censorship and surveillance.
It depends on the VPN. The best VPNs use AES encryption, which would take millions of years to crack. Plus, a VPN makes you anonymous by replacing your original location with a virtual one.


