5 Most Secure Cloud Storage Providers: Free & Premium Services Tested
Security and privacy are two of the greatest concerns for cloud storage users, but you don't need to be an expert in encryption to find the most secure cloud storage. We’ve done the heavy lifting for you, so read on.
Cloud storage has become an essential digital utility, but not all services offer the same level of protection for your files. This article will reveal the five most secure cloud storage services and how they work.
A truly secure cloud storage system should employ zero-knowledge encryption, also known as client-side or end-to-end encryption (though these are not fully synonymous terms). Plus, a strong privacy policy and adherence to privacy laws like the GDPR are must-haves.
The services we’ve selected feature on our list of the best cloud storage and fulfill these criteria. Some focus on robust free cloud storage, while others offer a full feature package. Others put all of their eggs in the security basket, with a minimal feature set. No matter what your needs are, we have you covered.
-
05/09/2022 Facts checked
Added Internxt as an honorable mention, included key takeaways.
-
06/25/2022 Facts checked
Updated Sync.com’s plans and pricing information.
-
05/24/2023 Facts checked
Updated information about Icedrive’s future plans and data centers
-
12/08/2023 Facts checked
We updated MEGA’s price offerings.
-
08/31/2024 Facts checked
Added video reviews for cloud storage providers in the list.
-
01/25/2025 Facts checked
Added new video ranking the most secure cloud storage providers.
-
02/11/2025 Facts checked
This article was updated with more details about Sync.com’s security and features, as well as a few details pertaining to pCloud, Icedrive and MEGA’s security.
-
03/11/2025 Facts checked
We updated this article’s information about Internxt’s plans and features.
-
04/04/2025 Facts checked
This article was rewritten following a reassessment of the cloud security capabilities of the services we reviewed.
-
05/01/2025 Facts checked
This article was updated with new information about pCloud and other top providers on the list.
-
05/13/2025 Facts checked
We updated this article’s provider ranking based fresh provider reviews.
-
06/17/2025 Facts checked
Updated with the 2025 version of our Internxt video review.
-
07/03/2025 Facts checked
Updated ranking to reflect the current performance of cloud storage providers.
Determine the Level of Data Protection That Matches Your Privacy Concerns:
200GB$2.65 / month(All Plans)
2TB$4.17 / month(All Plans)
 100GB – 3TB$2.99 / month(All Plans)
100GB – 3TB$2.99 / month(All Plans)100GB – 30TB$1.67 / month(All Plans)
2TB – 5TB$9.99 / month(All Plans)
2TB – 100TB$9.74 / month(All Plans)
1TB – 5TB$1.30 / month(All Plans)
100GB – 6TB$1.67 / month(All Plans)
 30GB – 5TB$6 / month(All Plans)
30GB – 5TB$6 / month(All Plans) Unlimited GB$20.50 / month(All Plans)
Unlimited GB$20.50 / month(All Plans)10GB – 20TB$0.50 / month(All Plans)
50GB – 12TB$0.99 / month(All Plans)
100GB – 10TB$0.83 / month(All Plans)
100GB – 30TB$1.67 / month(All Plans)
 Unlimited GB$4.17 / month(All Plans)
Unlimited GB$4.17 / month(All Plans) 2TB – 3TB$12 / month(All Plans)
2TB – 3TB$12 / month(All Plans)1GB – 100GB$1.50 / month(All Plans)
1TB – 2TB$8.33 / month(All Plans)
 500GB – 2TB$7.08 / month(All Plans)
500GB – 2TB$7.08 / month(All Plans)500GB – 2TB$2.99 / month(All Plans)
 10GB – 1TB$1.67 / month(All Plans)
10GB – 1TB$1.67 / month(All Plans)200GB – 3TB$1 / month(All Plans)
100GB – 500GB$6.90 / month(All Plans)
1TB$8.25 / month(All Plans)
 10GB – 500GB$5.83 / month(All Plans)
10GB – 500GB$5.83 / month(All Plans) 200GB – 3TB$1.38 / month(All Plans)
200GB – 3TB$1.38 / month(All Plans) 2TB$3 / month(All Plans)
2TB$3 / month(All Plans) 1TB – 4TB$8.33 / month(All Plans)
1TB – 4TB$8.33 / month(All Plans)100GB – 5TB$1.67 / month(All Plans)
 150GB – 10TB$1.25 / month(All Plans)
150GB – 10TB$1.25 / month(All Plans) 100GB – 1TB$6.25 / month(All Plans)
100GB – 1TB$6.25 / month(All Plans) 50GB – 1TB$3 / month(All Plans)
50GB – 1TB$3 / month(All Plans)50GB – 1TB$5.83 / month(All Plans)
 500GB – 2TB$5 / month(All Plans)
500GB – 2TB$5 / month(All Plans) 100GB – 10TB$0.93 / month(All Plans)
100GB – 10TB$0.93 / month(All Plans) 250GB – 4TB$30.44 / month(All Plans)
250GB – 4TB$30.44 / month(All Plans)
Not everyone needs the same level of security from their cloud storage, and understanding your threat model is key to making the right choice. While some users require zero-knowledge encryption for highly sensitive data, others may prioritize convenience and collaboration features over maximum security. The ideal balance depends on what type of files you’re storing, how you plan to share them and whether you’re willing to trade some usability for enhanced privacy protection.
10,000+ Trust Our Free Cloud Storage Tips. Join Today!
- Demystify cloud storage terminology and key concepts in plain language
- Discover easy-to-implement techniques to securely backup and sync your data across devices
- Learn money-saving strategies to optimize your cloud storage costs and usage
What Is the Most Secure Cloud Storage? Cloudwards’ Choice: Sync.com
The 5 Most Secure Cloud Storage Services
1. Sync.com — Best Cloud Storage With Zero-Knowledge Encryption
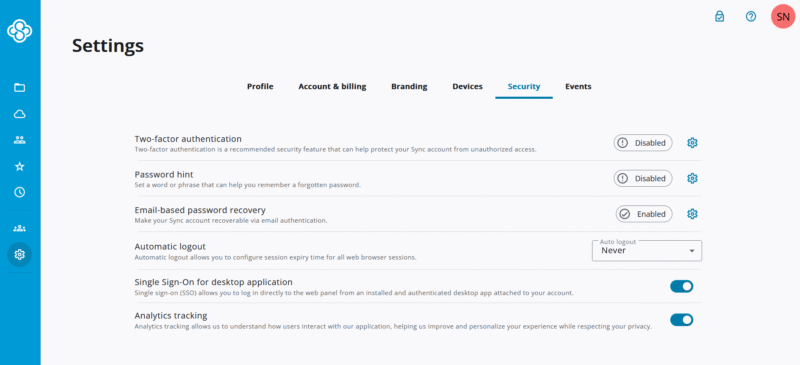
Sync.com is a security powerhouse, offering client-side encryption for all of your storage. Unusual for such a secure service, it integrates with Microsoft Office and provides robust and secure file sharing, letting you easily collaborate within an encrypted environment. Plus, it’s one of the cheapest cloud storage services and even offers unlimited cloud storage.
Sync.com also offers a file versioning system that retains previous versions of files for up to 30 days on free plans and 180 days on paid plans, helping protect against accidental changes or ransomware attacks. Sync.com also offers secure file recovery options that maintain end-to-end encryption throughout the restoration process, ensuring your data remains protected even during recovery operations.
Sync.com’s team accounts come with comprehensive admin controls that allow business owners to manage user permissions, enforce company-wide security policies and monitor account activity. These are essential features for organizations that need to maintain governance over sensitive company data.
Sync.com Hands-On Testing
Overall, we found Sync.com’s apps to be well designed and easy to use. Sync.com installs a sync folder on your device, and everything you copy to it is uploaded to the cloud. You can also designate files as online-only to save hard drive space. Its mobile apps are minimal yet capable, with the only notable feature being automatic uploads for photos.
Sync.com Pricing & Value
Sync.com offers 5GB of free storage space. You can upgrade to a 2TB plan for just $4.80 per month on a yearly subscription, which is affordable compared to most other providers. You can also get unlimited cloud storage with a team account for relatively cheap. Read our full Sync.com review for more details.
- 5GB
- 2TB
More plans
- 6TB
- per user, per month, billed annually
- 1TB
- Monthly price for 1 user (3 users minimum) Yearly price for 3 users
- Unlimited GB
- Minimum 100 users, custom requirements, account manager, training options
2. pCloud — Best Secure Cloud Storage With Online Backup
pCloud is a Swiss-based company that offers one of the most capable and polished cloud storage services, with a wealth of entertainment-focused features such as a fully featured music player and Kodi integration.
In addition, beyond standard versioning, pCloud offers an account rewind feature that lets you restore your entire cloud storage to a previous state, along with trash history extending up to 180 days, providing excellent protection against accidental deletions or ransomware attacks.
pCloud Hands-On Testing
pCloud has some of the best cloud storage apps out there, covering all major operating systems. Its desktop apps sync your files instantly with barely any delay, and its mobile apps sport some of the most user-friendly design we’ve seen in our years of testing. It is also among the fastest cloud services that we’ve tested.
The macOS experience has been streamlined with the introduction of a QR code in the installer that guides users through the setup process, making it easier for new users to get started with the service. It has also improved accessibility on macOS by ensuring that both the “dock” icon and “applications” button open the pCloud Drive interface directly, providing quicker access to your cloud files.
The Android app has also received a visual refresh, with a cleaner, more modern look for files and folders, enhancing the overall user experience while maintaining pCloud’s intuitive interface.
The app now supports drag-and-drop functionality for moving files between pCloud and third-party apps, significantly improving the mobile workflow experience for users who frequently work across multiple applications. When using automatic uploads, you can preserve your local folder structure, making it easier to maintain organization when backing up photos and files from your mobile device.
pCloud Pricing & Value
pCloud offers up to 10GB of free storage, contingent on completing a few tasks and referring friends to the service. Its paid plans are affordable, with the 2TB plan costing $8.33 per month on a yearly commitment.
pCloud’s family plans represent exceptional value by including the Crypto encryption feature at no additional cost, allowing up to five users to benefit from end-to-end encryption under a single subscription. This represents a significant advantage over purchasing individual licenses with the Crypto add-on.
However, the true highlight is its lifetime cloud storage plans, which offer even more value for a one-time payment. Read our full pCloud review for more.
- 10GB
- 500GB
- 2TB
More plans
- 10TB
- + FREE Encryption
- 2TB
- + FREE Encryption
- 10TB
- Price per user (minimum 3)
- 1TB
- Price per user (minimum 3)
- 2TB
- Encryption for pCloud Drive
3. Tresorit — Most Secure Business Cloud Storage
Tresorit is known for its exceptional security features and privacy-focused approach. It positions itself as a premium cloud storage solution for both personal and business users, with a particular emphasis on security-conscious professionals and organizations handling sensitive data.
Tresorit Hands-On Testing
In terms of platform compatibility, Tresorit supports all major operating systems including macOS, Windows, Linux, iOS, and Android. The desktop application offers a minimalist design that makes file management straightforward and less daunting. The mobile apps provide essential functionality, though video playback is limited to mobile devices only.
Tresorit Pricing & Value
Tresorit comes at a premium price compared to competitors, with its 1TB personal plan costing $11.99 per month with annual billing. The Tresorit free plan offers of storage, which is more generous than some competitors but still limited.
The Business and Professional plans offer 1TB and 2TB per user, respectively. The maximum storage available is 4TB for personal users, which may not be sufficient for those working with large file types regularly. All plans come with a 14-day free trial.
- 50GB
- Price per user (billed annually), Storage per user, User count: 3+
- 1TB
- 3+ room managers, 15 contributors, unlimited viewers, unlimited data rooms, 15GB max file size & more.
- 6TB
More plans
- Price per user (billed annually), Storage per user, User count : 1
- 2TB
- 1TB
- 4TB
- 1 room manager, 5 contributors, unlimited viewers, unlimited data rooms, 10GB max file size & more.
- 4TB
- Custom room managers and contributors, unlimited viewers, unlimited data rooms, custom storage, 20GB max file size & more.
- Price per user (billed annually), Storage per user, User count : 50+
4. Internxt — Most Innovative Encrypted Cloud Storage
Internxt offers the most comprehensive security suite of the services on this list. As an overall cloud storage system, it’s pretty sparse, offering little beyond the basics. Like pCloud, it has a cloud backup feature, plus Internxt Send for secure file sharing. It also offers more security features, including a limited VPN and antivirus.
Internxt Hands-On Testing
Internxt’s apps aren’t the most impressive — the desktop app is a bit fiddly and the mobile apps lack automatic photo upload functionality. It uses the standard sync folder model, but there is no option to sync other folders. However, you can set files as online-only to save some space on your hard drive.
achievement given its dearth of features.
Internxt Pricing & Value
Internxt is one of the cheapest cloud storage on this list, with 3TB of storage costing just $2.60 per month on a yearly plan. Like pCloud, it offers lifetime plans that offer even more value. Unfortunately, its free plan comes with only 1GB of storage. Read our Internxt review for more.
- 1GB
- Storage + VPN (FR), Antivirus, Backup & More
- 1TB
- Storage + VPN (FR, DE, PL), Antivirus, Backup & More
- 3TB
More plans
- Storage + VPN (FR, DE, PL, CA, UK), Antivirus, Backup & More
- 5TB
- Storage + VPN (FR, DE, PL), Antivirus, Backup & More
- 1TB
- Storage + VPN (FR, DE, PL, CA, UK), Antivirus, Backup & More
- 2TB
5. Icedrive — Secure Cloud Storage With Lifetime Plans
Icedrive is one of our favorite secure cloud storage providers. It’s affordable, fast and well designed. It offers a more stripped-back experience, but it brings a much higher level of execution and more choices when it comes to syncing your files. It’s also affordable, nabbing a spot on our list of the cheapest cloud storage services.
Icedrive Hands-On Testing
Icedrive gives you the choice of using a standard sync folder, syncing existing folders or installing a virtual drive, similar to with pCloud. All of its apps sport a clean and minimalistic design that makes the service easy to use, even for beginners.
Icedrive Pricing & Value
Icedrive offers 10GB of secure storage for free users. Upgrading to a 3TB plan will cost you $8.99 per month on a two-year plan, and you can get a lifetime plan for better savings. Read our full Icedrive review for more.
- Bandwidth limit: 50GB
- 10GB
- Bandwidth limit: 250GB
- 100GB
- Bandwidth limit: 2TB
- 1TB
More plans
- Bandwidth limit: 8TB
- 3TB
- 512GB
- 2TB
- 10TB
- Additional 128GB storage for users who purchased the Lifetime Plan
- 128GB
- Additional 512GB storage for users who purchased the Lifetime Plan
- 512GB
- Additional 2TB storage for users who purchased the Lifetime Plan
- 2TB
Honorable Mentions
These three services didn’t quite make our top five, but they’re still worth taking a look at.
MEGA
MEGA is known for good security and its large free plan. It’s a reliable service that offers a standard feature set, with the somewhat unusual inclusion of an encrypted chat client. Its paid plans are similarly spacious, with enterprise plan users getting up to 10PB (that’s 10,000TB) of data.
MEGA is incorporated in New Zealand, but it operates servers in the EU, Canada and Japan as well, meaning it has to comply with the laws of all of those countries — including, importantly, the GDPR.
Its end-to-end encryption applies to all files and is extended to free users as well. MEGA offers sophisticated private key management that puts users in complete control of their encryption keys, though this means that if you lose your password, you’ll lose access to your data permanently.
MEGA’s commitment to transparency is demonstrated through its open-source code, allowing independent security researchers to audit the code for potential vulnerabilities or backdoors. This is a critical factor for security-conscious users wanting verification of the service’s privacy claims.
MEGA is more expensive than the other services on this list, especially for its higher-capacity plans. That said, its smaller plans come at reasonable prices, with its 2TB plan costing $9.74 per month with a yearly commitment. Read our full MEGA review for more.
- 20GB
- File transfer: 2TB (Monthly plan) 24TB (yearly plan)
- 2TB
- File transfer: (monthly plan) 96TB (yearly plan)
- 8TB
More plans
- File transfer: 16TB (monthly plan) 192TB (yearly plan)
- 16TB
- Price per user (minimum 3) 3TB Transfer quota
- 100TB
IDrive
IDrive is a service provider that straddles the line between online backup and cloud storage, though it clearly focuses on the backup aspect. It offers what is likely the most comprehensive suite of backup features, though its cloud storage features are basic. The good news is that you can enable client-side encryption for all of your sensitive files.
IDrive also supports external hard drive backup, allowing you to create local backups of your cloud data for additional redundancy and offline access.
IDrive is also very cheap. A 5TB plan costs just $6.22 per month on a two-year plan. As a bonus, your storage is essentially doubled, as you get a separate 5TB of storage for your cloud sync space (this doubling applies to all plans). There’s no free plan, though. Read our full IDrive review for more.
- No credit card required.
- 10GB
- One user.
- 100GB
- One user, multiple computers. Plans starting from 5TB up to 100TB. Big discount for first-time signup.
- 5TB
More plans
- 5 computers, 5 users. Starting at 5TB up to 500TB. Big discount for first-time signup.
- 5TB
- Monthly Plan storage starts at 1.25TB up to 50TB Unlimited users, multiple computers and servers. NAS devices. 250GB storage. Starting at 250GB up to 50TB. Large discount for first-time signup.
- 250GB
- 5TB
Filen
Filen is a relatively young cloud storage service, which is why we’re tentatively giving it an honorable mention. It seems very promising despite its age, though, with a high degree of security bolstered by full-coverage client-side encryption and open-source apps.
Filen comes with 10GB of free storage by default, but you can expand that to 10GB if you sign up via our exclusive deal by clicking on any of the links in the pricing table below. Filen’s paid plans are affordable, with 2TB of storage costing $7.50 per month on a yearly plan. Read our full Filen review for more.
- Storage 10GB
- 10GB
- *prices are in Euro
- 100GB
- *prices are in Euro
- 200GB
More plans
- *prices are in Euro
- 500GB
- *prices are in Euro
- 2TB
- *prices are in Euro
- 10TB
Methodology: How We Tested the Most Secure Cloud Storage Providers
Before putting pen to paper, our team of expert reviewers spends a week or more familiarizing themselves with the services we review. We go over every detail and try to use each feature available to its fullest to get to the nuts and bolts.
- Speed: We run regular speed tests on a virtual machine hosted in Ireland with a connection speed of 100 Mbps for uploads and downloads. We upload and download a 5GB test folder twice and average the results.
- Security and privacy: We examine each service’s implementation of cryptography, including encryption protocols, use of client-side encryption and server security. We also examine the privacy policy and look at the jurisdiction under which the service operates to get a full picture of its privacy.
- Collaboration and productivity: We look for and test collaboration features like advanced file sharing, first-party productivity tools and integrations with external productivity suites like Google Workspace and Microsoft Office.
- Ease of use: We make note of our experience using the service’s apps across multiple platforms, focusing on the elements we like, as well as any bugs or quirks.
- Price and value: We examine a service’s payment plans, including its free offering, and then compare all of the features it offers against the price to determine its ultimate value.
Why You Need Secure Online Storage
Understanding vulnerable access points is crucial when using secure cloud storage — even the most encrypted service can be compromised if you access it from an unsecured device or network.
Many of these secure cloud storage providers now support biometric authentication on mobile devices, adding an extra layer of protection when accessing your files on smartphones and tablets. Most secure providers also offer password protection for shared links, with Sync.com and pCloud providing the most robust options, including expiration dates and download limits.
As mentioned above, we also evaluate data residency options, which allow customers to choose where their data is physically stored. This is an important consideration for compliance with regulations like the GDPR or organizations with specific geographic requirements.
In addition, while cloud storage primarily focuses on file accessibility and synchronization, many services, such as IDrive and pCloud, also offer cloud backup functionality, which creates redundant copies of your data specifically for disaster recovery purposes.
Below are some more key reasons why you might need secure cloud storage:
- Privacy protection: Features like end-to-end encryption and GDPR compliance protect your data from prying eyes, including the cloud storage service itself.
- Data security: Cloud storage services keep your data on secure servers that offer better protection than your personal device, as they are much less likely to succumb to malware or a cyberattack. We also examine each service’s ransomware protection capabilities, as this has become a critical security feature for protecting cloud data from increasingly sophisticated attacks.
- Archiving and disaster recovery: Services that offer cloud backup let you archive files for long-term storage. Files stored in the cloud won’t be affected if your device breaks or falls prey to malware, letting you restore your files in the event of a disaster.
Final Thoughts
Most aspects of cloud storage security — like encryption, regulatory compliance and privacy policies — can be difficult to understand. Hopefully, we’ve helped you grasp them better and assisted you in choosing a secure cloud storage solution.
Sync.com is our top choice — it offers full-coverage zero-knowledge encryption paired with productivity integrations. You can try Sync.com with 5GB free, or try a full-featured premium plan with the assurances of the 30-day money-back guarantee.
What is your favorite secure cloud service? Have you used any of the services on our list? What was your experience with them like? Please let us know in the comments below, and as always, thank you for reading.
FAQ: Secure Cloud Providers
Sync.com is the best secure cloud storage service, offering zero-knowledge encryption; PIPEDA, HIPAA and GDPR compliance; and data duplication for disaster recovery.
The safest place to keep documents online is with a secure cloud storage provider that lets you manage documents. The best cloud document management system is Sync.com. From our research, it’s the only end-to-end encrypted cloud storage solution for private users that also offers Microsoft Office integration.
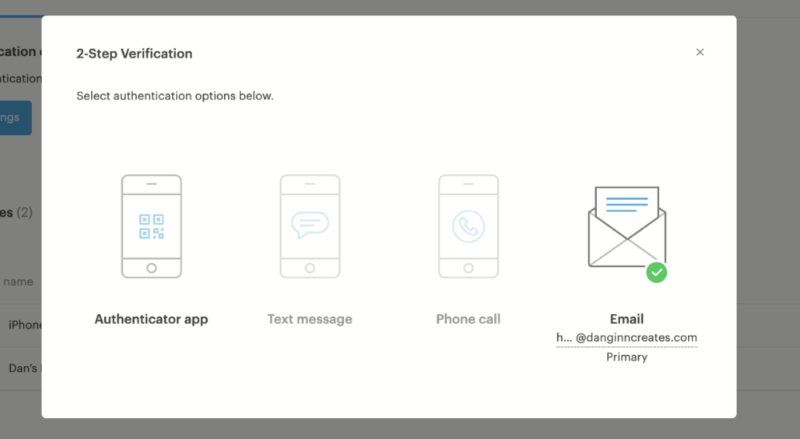
Yes, your cloud storage account can get hacked, just like any other online account. That’s why it’s important to have two-factor authentication to make sure only you can access your files.









![Video thumbnail for the video: Ultimate Icedrive Review [2024 Pros and Cons Revealed]](https://img.youtube.com/vi/iVGsDxYVV-Y/maxresdefault.jpg)