What Is a VPN? How Virtual Private Networks Work in 2025
If you’ve ever come across an ad for NordVPN, Surfshark or ExpressVPN, chances are you’ve asked yourself, “What is a VPN?” This guide will explain what a VPN is, how they work and what you can (and can’t) use them for.
A VPN (short for “virtual private network”) is a service that protects you when you connect to the internet. A VPN encrypts all your internet traffic so that no one can see what you’re doing online. It also reroutes your internet connection through a VPN server, which can make it seem like you’re connecting from a different place, as it hides your real location and IP address.
Although VPN technology came from the corporate world, nowadays you’ll often find VPNs packaged as easy-to-use consumer software, like the services on our list of the best VPN providers. If you’re still wondering, “What is a VPN?,” keep reading. Answering this question is the focus of this article, and we’ll start with explaining why you might need one.
-
10/13/2023
We rewrote this article and added more detailed explanations and recommendations.
-
03/06/2024 Facts checked
We rewrote the article to simplify the information presented and make it more accessible, and added new information on the different types of VPN connections and protocols.
-
05/21/2024
Updated the article to add custom graphics.
How Does a VPN Work?
A VPN works by establishing an encrypted tunnel between your device and a VPN server. The VPN server takes your signal and sends it to the website you’re trying to visit or the remote server you’re communicating with. It receives a response from the website, encrypts it and sends it back to you.
In essence, VPN servers communicate with the internet on your behalf. This is the basis for how all VPN connections work.
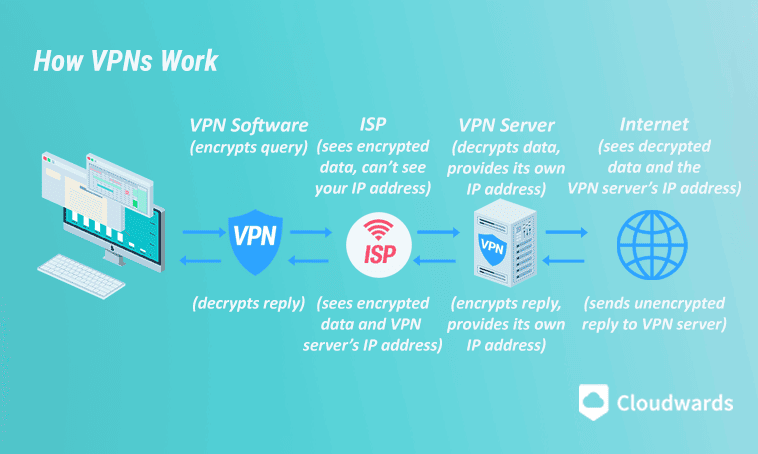
so no one can remotely monitor traffic on your device.
How Does the Encryption Tunnel Work?
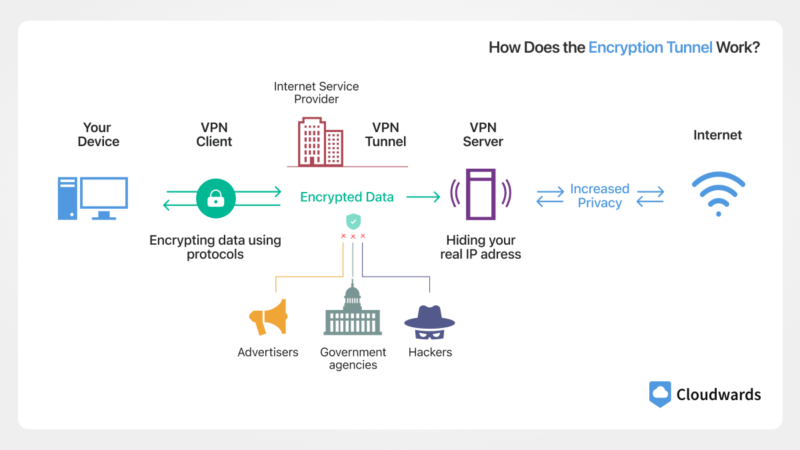
When your VPN is active, all of your internet traffic is encrypted and hidden as it travels through an encrypted tunnel that keeps everyone else out. Because the VPN server reroutes all of your traffic, an outsider can only see the VPN server communicating with the internet.
A VPN even hides your activity from your internet service provider. Your ISP can see that you’re using a VPN, but not which sites you visit or what you do online.
Because outsiders can only see the VPN server’s IP address, using a VPN has the additional effect of hiding your real IP address from the internet. The only entity that knows what you’re up to is the VPN server you’re connected to, which is why it’s crucial to always use a no-logs VPN.
Do VPNs Prevent Malware?
Although it can protect your private data when you’re connected to a public network, a VPN can’t protect you from most malware, phishing attacks or cyberattacks exploiting software vulnerabilities.
However, VPN services can be much more complex than their base purpose suggests. Many VPN providers now include antimalware and antivirus capabilities, as well as tracker and ad blockers that can keep you from clicking on malicious ads.
Why Do I Need a VPN?
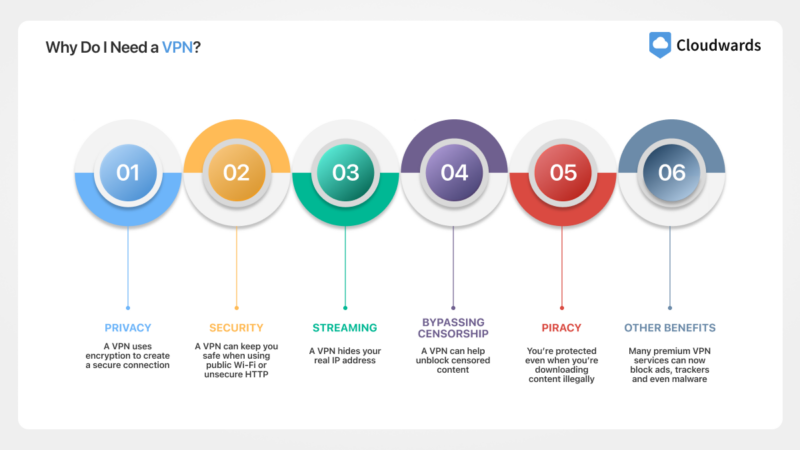
Although a VPN service’s primary job is to keep you safe online, it can fulfill other functions for you as well. Here is a list of the key benefits you’ll get from using a VPN:
- Privacy: VPN providers offer protection from online threats. A VPN uses encryption to create a secure connection. This makes your online activity invisible to others, including hackers, your internet service provider and government agencies.
- Security: A VPN can keep you safe when using public Wi-Fi or unsecure HTTP websites thanks to encryption keeping unwanted parties out of your system.
- Streaming: A VPN hides your real IP address, making it appear as though you’re somewhere else. This can be used to unblock content that is normally unavailable in your region.
- Bypassing censorship: If you’re in a country with a restrictive regime, a VPN can help unblock censored content while keeping your identity a secret.
- Piracy: Thanks to VPNs’ encrypted connections and a nifty feature called a kill switch, you’re protected even when you’re downloading content illegally.
- Other benefits: VPN providers often throw in extra features. Many premium VPN services can now block ads, trackers and even malware, and some offer still more advanced features, like remote access and dark web monitoring.
What Makes a Good VPN?
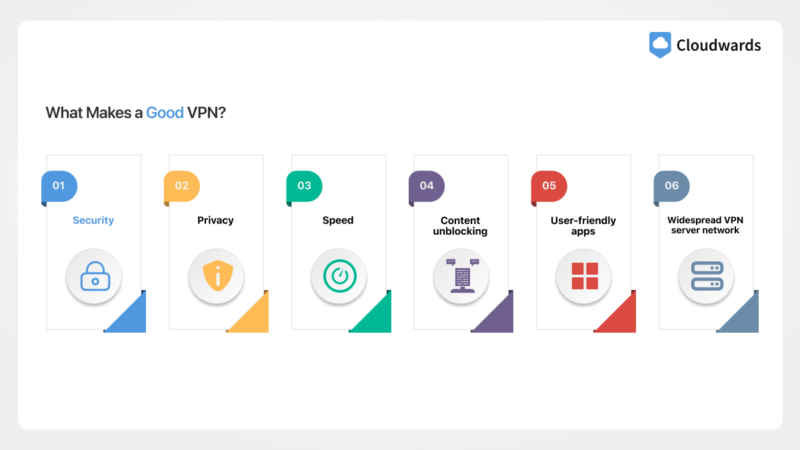
Aside from adhering to VTI Principles, a reliable VPN service needs to offer security, good speeds, user-friendly apps and a no-logs policy, and it needs to be able to unblock major streaming platforms. Here’s a detailed look at what makes a good VPN:
- Security: Any good VPN needs modern VPN connection and encryption protocols. OpenVPN and WireGuard are great VPN protocols, and combined with AES-256 or ChaCha20 encryption, they work to keep your connection safe.
- Privacy: A no-logs policy is a must for any decent VPN, but other privacy features, like anonymous payments, email-free logins and obfuscation, can help bolster your privacy.
- Speed: All VPNs slow your connection down, but at Cloudwards, our opinion is that a fast VPN should result in a loss of no more than 20% of your top upload and download speeds.
- Content unblocking: A VPN needs to be able to unblock every major streaming platform — or, in more practical terms, the ones you’re subscribed to — and be fast enough for streaming in high quality.
- User-friendly apps: VPN software is generally very easy to understand, but some VPNs, like ExpressVPN, simplify the connection process to the press of a button.
- Widespread VPN server network: Having a server close to you will give you better speeds. Servers in other countries will let you unblock content there, so look for one with servers in the countries you need.
Are Free VPNs Good to Use?
A free VPN can be almost as good as a paid one, but safe ones are few and far between. Free VPNs can place limits on speed and data usage or lock paid features. Additionally, they will often provide inadequate protection or have other issues, like slow speeds or the inability to unblock streaming platforms.
However, if a VPN just doesn’t fit in your budget, you can go with one of the choices on our best free VPN list. As one of only two free and reliable VPNs with unlimited data, Proton VPN tops that list and is our go-to recommendation for free users. If you’re interested in learning more about the service, you can check out our Proton VPN review.
Types of VPN Connections
There are three types of VPN connections: remote access VPNs, site-to-site VPNs and VPN apps. All three types route VPN traffic through a secure VPN tunnel, but they differ in scope.
Remote Access VPN
Remote access VPNs connect remote workers to an office network over the internet by setting up a secure connection between the user and the remote network. In this setup, the user’s device encrypts all incoming and outgoing internet traffic, which allows the user to access company files without fear of eavesdropping. Commercial VPN apps evolved from this type of VPN.
Site-to-Site VPN
A site-to-site VPN connects multiple networks (or LANs) to each other. Whereas remote access VPNs connect remote workers to an office, site-to-site VPNs connect a central office to branch offices or other collaborators, partners or customers.
Communication happens between gateways installed on the connected networks’ internet routers. This means that individual users do not need to use separate VPN clients, as all communication between these gateways is encrypted and secure.
VPN Apps
Commercial VPN apps connect an individual user to the VPN provider’s own private networks. The VPN company hosts these private networks on VPN servers around the world, and the VPN client lets you connect to them just like a remote access VPN. As with remote access VPNs, encryption happens on the user’s side.
What Is a Double VPN?
Double VPN is a feature that lets you route your traffic through two VPN servers. Though this slows down your connection and doesn’t necessarily result in twice the protection, it does have the added benefit of giving you some peace of mind. Even if the terminal VPN server is seized, the other one will still keep your online data safe.
Types of VPN Encryption
The kind of encryption your VPN uses largely depends on your choice of VPN protocol. As we’ve established, a VPN creates an encrypted tunnel between the user’s device and the public internet. To create this tunnel, the VPN client uses a tunneling protocol. Different tunneling protocols pair with different types of encryption.
VPN Protocols
Here’s a quick rundown of the most popular VPN protocols.
- OpenVPN: The international standard, OpenVPN is reliable, secure and fast, though it can be a drain on device resources. It pairs with AES-256 encryption.
- WireGuard: WireGuard was developed as a sleek alternative to OpenVPN, boasting excellent security and potentially faster speeds than OpenVPN while using fewer computing resources. It pairs with ChaCha20 encryption.
- IKEv2: This lightweight protocol is very fast and very light on computing power, making it ideal for mobile devices. IKEv2 uses IPSec and AES-256 for encryption by default, but it can work with other encryption types, like ChaCha20 and Camelia.
- L2TP/IPSec: This is a secure protocol with impressive speeds, but the tradeoff is its reliability — thus, it is prone to network drops. It uses IPSec for encryption.
- Service-specific protocols: Some providers develop their own VPN protocols, either from scratch or based on an existing protocol. The type of encryption they use is up to them. Some examples are NordVPN’s NordLynx, ExpressVPN’s Lightway and Hotspot Shield’s Catapult Hydra (Kaspersky VPN and Bitdefender VPN also use this protocol).
How to Use a Virtual Private Network
Using VPN software is pretty straightforward. All VPNs are different, but in general, if you can use one of them, you can use most of them. Here’s a quick beginner’s guide on how to use a VPN:
- Download and Install a VPN
Before you can use a VPN, you’ll of course have to install one. Go to NordVPN’s website and sign up at a 76% discount. A 30-day money-back guarantee is available if you change your mind. Then download the VPN app and install it.
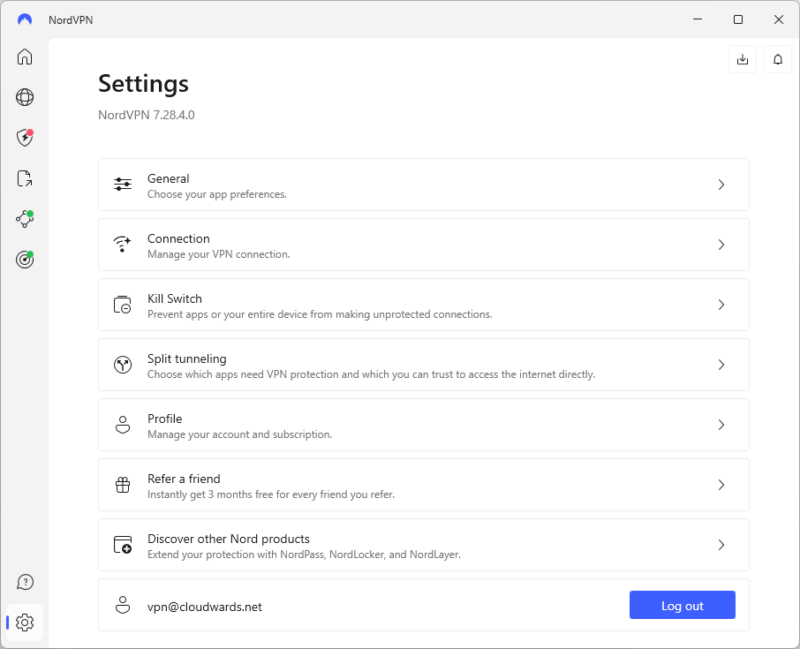
- Log in and Access the VPN Settings
Once you’ve installed the app, log in to your account. Since this is the first time you’re using the app, you might want to play around with the settings. We suggest only activating the kill switch and any extra features like ad blocking. Access the settings menu to start setting up the VPN.
- Set Up Your VPN and Activate the Kill Switch
In the settings menu, find the kill switch and activate it. It will disconnect your internet if your VPN connection drops. This should be all you need to start using the VPN. NordVPN offers an internet kill switch and an app kill switch. You only need to activate the internet kill switch.
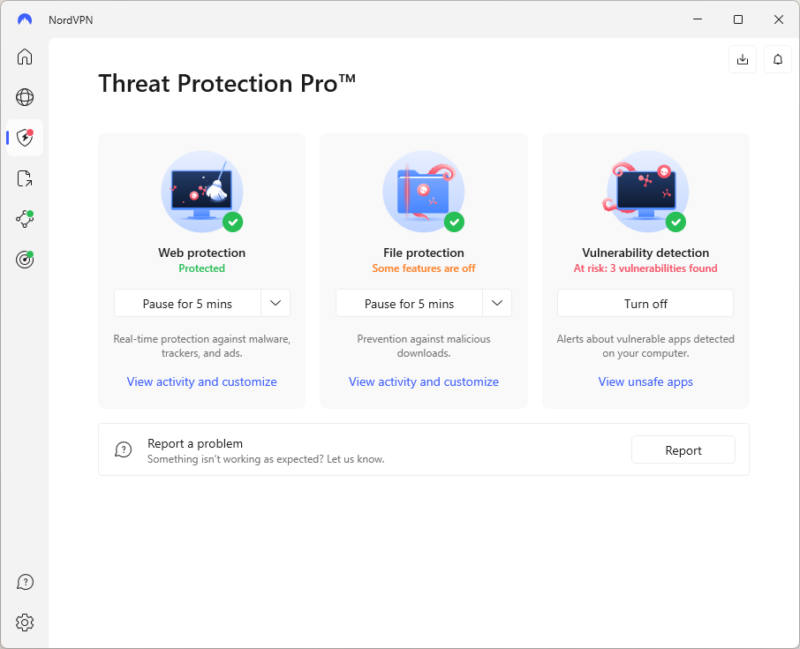
- Set up Advanced Features
If your VPN offers any advanced settings, like malware or ad blockers, you’ll usually find them in a separate tab or menu. In our example, these are in the “Threat Protection” tab. Access this tab and activate any features you want to use.
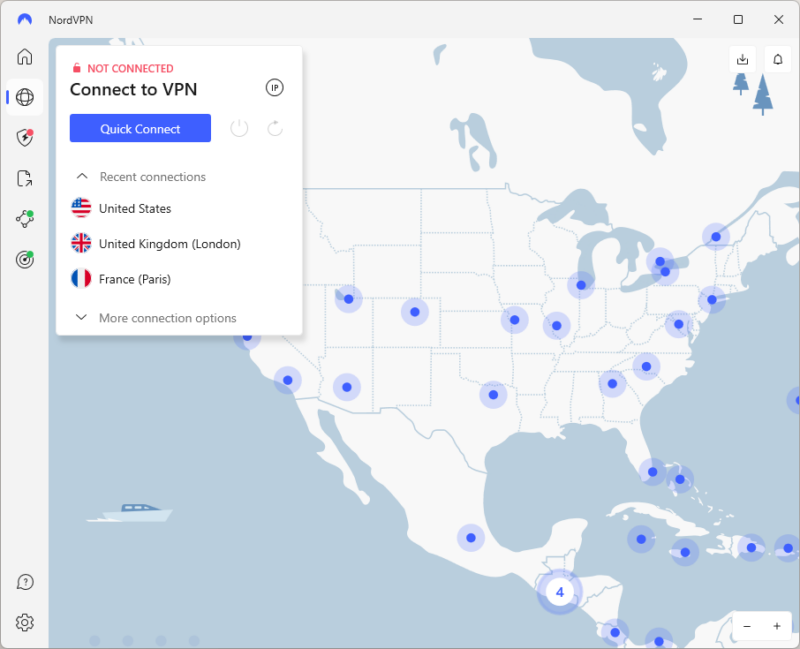
- Choose a VPN Server and Connect
If you want to connect locally, just press the quick connect on the home screen. If you want to connect to another country, use the world map and locate the country or city you need, or use the search bar to find your desired country.
Final Thoughts
A VPN is an invaluable tool to have in your online privacy kit, and they’ve become indispensable in our increasingly online world. Although they might not be able to protect you from every kind of threat, they’ll still go a long way toward safeguarding your online anonymity and help you access content you otherwise wouldn’t be able to.
What are your experiences with VPNs? Have you ever used one? If so, which VPNs have you tried? Please let us know in the comment section below, and as always, thank you for reading.
FAQ: What Is a VPN?
Getting a VPN is as easy as visiting a VPN provider’s website, signing up for an account, and downloading and installing the VPN’s client app.
Free VPNs come with limitations that make them less effective than paid ones, but you can get most of the basic functions. Be careful, though, as most of the thousands of VPNs you’ll find on mobile app stores are ineffective at best and actively malicious at worst.
Unless the VPN goes back on its no-logs policy (or doesn’t have one at all), your web traffic and browsing history cannot be traced back to you.
Even though most websites now use the encrypted HTTPS protocol to communicate with you, VPNs can still keep your data secure when you visit unsecured websites and use public WiFi. Plus, most premium VPNs are now entire online security suites that can take care of much more than just encryption.
Not only does Netflix work with VPNs (good ones, at least) but you can also use a VPN to unblock Netflix in places where it’s banned and access content from different Netflix regions. However, most streaming platforms ban VPN IP addresses, preventing most VPN providers from connecting.
No, it is not illegal to use a VPN in the United States and most other countries. Only a handful of very oppressive regimes around the world ban VPN use wholesale.
Yes, using a VPN is completely safe, as long as you use a trusted and tested one that keeps no logs of user activity.


