VPN vs Proxy vs Tor: Remaining Anonymous Online in 2025
If you’ve ever wanted to change your IP address to access content from another place in the world, you’ve probably come across proxy servers, VPNs and Tor. This article will help you decide between a VPN vs proxy vs Tor to protect your online activity.
Remember that old meme about hiding your identity behind seven proxies? As it turns out, no matter how many proxies you go through, your identity is never hidden. Proxies don’t encrypt any data, and exposing you is just a matter of tracking your signal back to its original source. Only a virtual private network (VPN) can truly keep you safe. This comparison will see the age-old VPN vs proxy vs Tor debate finally put to bed.
Basically, the main difference between VPN vs proxy is that a proxy server primarily anonymizes the source of your internet traffic and can assist with traffic distribution and security checks, while a VPN uses encryption to hide both your IP address and data, ensuring they remain unreadable to unauthorized users.
However, proxy servers just aren’t safe enough, and the Tor network is run by volunteers who can access your data. That said, both have their uses. We’ll discuss what those are and how VPNs, proxies and Tor compare. At the end, we’ll give you our recommendation on which tool to use, so read on. Let’s dive into the difference between Tor and VPN, as well as how they both differ from proxy, and vice versa.
-
12/11/2021
Added new information on VPN providers and paid proxies.
-
10/01/2024 Facts checked
We updated information in this article for accuracy and changed some formatting to improve readability.
VPN vs Proxy vs Tor: Explaining the Basics
We’ll start this comparison off by going over what each of these services is and isn’t. To that end, we’ll explain what proxy servers, VPNs and the Tor network do and how they work. Then we’ll talk about how and when you should use them to help you choose the best service for your use case.
connection is the fastest and most secure.
What Is a Proxy Server?
A proxy server is an intermediary connection point which can trick the receiving web server into thinking your IP address and your location are different from what they are.
However, proxy servers have a glaring issue in that your connection isn’t secured with encryption. Basic route tracing, which can easily be done online for free, will reveal your true IP address and location.
If you’re doing anything questionable, then your internet service provider, government or anyone else who can access your stream of data can see it. Even so, proxies have their place. There are different types of servers you can use depending on the traffic you want to hide. Among these server types, captcha proxies are unique as they can handle multiple captcha challenges common on websites, ensuring uninterrupted browsing by easily bypassing captchas.
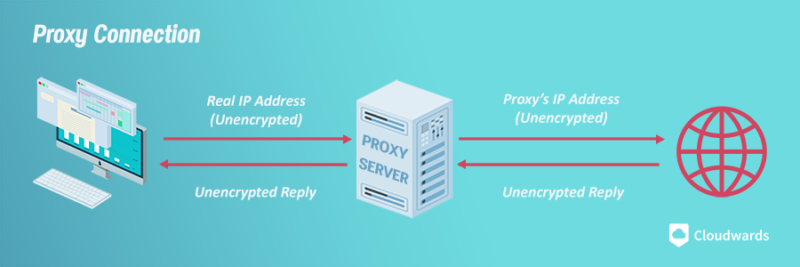
won’t encrypt any of your internet traffic.
HTTP Proxy Servers
HTTP proxies are meant exclusively for internet traffic. You enter the IP address of the proxy you want to connect to in your browser’s settings and traffic will be routed through that server. Other traffic, such as peer-to-peer connections, isn’t suitable for an HTTP proxy.
There isn’t any encryption, either — not even basic SSL/TLS. You can learn the difference between those in our SSL vs TLS guide.
That means you’ll have to make sure that the websites you connect to support TLS, especially if you’re inputting sensitive information. That applies to email, too. You can learn more about enabling encryption for your emails in our guide to email security.
SOCKS Proxy Servers
SOCKS proxies are better than HTTP proxy servers in that they’re traffic agnostic. You can send any traffic through a SOCKS proxy, whether it is basic web traffic, a P2P connection or an FTP connection.
Apart from that, SOCKS proxies have the same issues as HTTP proxies. There’s no encryption outside what you supply and the traffic load and speed are up in the air. Plus, SOCKS proxy servers have more overhead, so they are usually slower than HTTP.
Free Proxy Servers vs Paid Proxies
Free proxies are bad for security, but what about paid ones? You’d think that maybe shelling out a few dollars for a paid proxy might give you better security, but that’s not really the case.
The fact of the matter is that paid proxy servers aren’t meant for individuals. Instead, they help companies scrape data from websites. Most corporations blocklist IP addresses coming from other businesses, so those businesses have to use proxy servers if they want to obtain that data. That’s the true purpose of a paid proxy, and it’s no more secure than a free proxy server.
Proxy Concerns
Cybersecurity novices will often reach for a free proxy online as a way to protect themselves while downloading a few movies or albums. Free proxies come with many drawbacks, including lack of encryption, inconsistent uptime, slow speeds and in some cases exposure to malware. It’s also difficult to pin down who’s running a free proxy server and their integrity as it pertains to cybersecurity.
What Is a VPN (Virtual Private Network)?
A VPN is similar to a proxy server, except this time the connection uses encryption to make route tracing almost impossible. They also usually come with extra security features, like kill switches. You can read our guide on what a VPN is and VPN security guide if you want the nitty-gritty details on how the services work.
What Does a VPN Server Do?
A VPN server handles part of the encryption process and directs your data to its final destination. When your encrypted connection reaches the VPN server, it gets decrypted and sent to its destination. The website responds to your request and sends the reply back to the VPN server, which then encrypts that reply and sends it to you, where it gets decrypted only when it reaches your device. Some VPNs even keep the communication between the VPN servers and website encrypted.
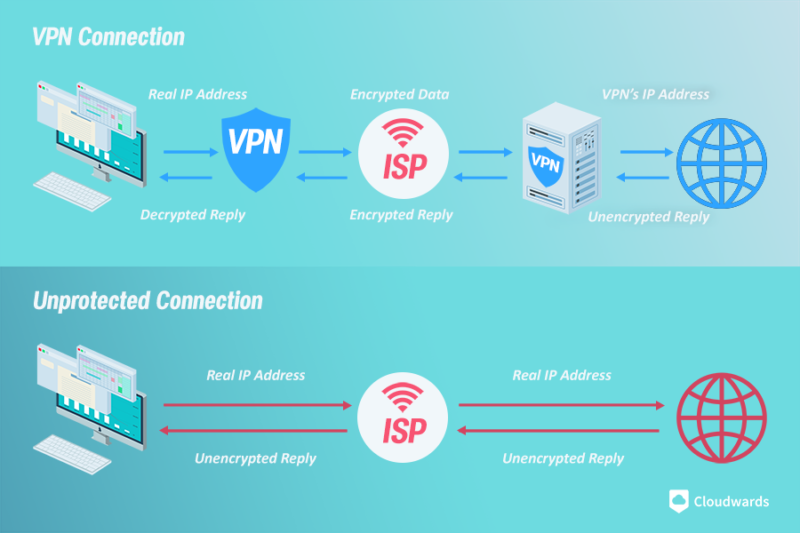
VPN providers are far more secure because they use advanced encryption ciphers like AES-256 and ChaCha20 to encrypt your connection and anonymize your traffic.
As long as you’re using a service that doesn’t leak — read our VyprVPN review for an example — you’ll be incognito online. Route tracing becomes practically impossible and your initial connection disappears into the ether.
VPN Benefits
First let’s address the elephant in the room: VPNs are paid services. We’ll talk about free VPN services in a bit, but for now, suffice it to say that if you need a VPN, you should use a paid one. The extra cost comes with extra security, reliability and features.
For example, VPNs can bypass the harshest geoblocks and let you access restricted content across the globe. The best streaming VPNs will help you unblock Netflix, Hulu, Amazon Prime Video and most other streaming platforms.
VPNs are also the only real solution for secure P2P connections, as you can see in our best VPN for torrenting guide. VPN services provide the best balance of security and speed for P2P connections — something proxy servers and Tor struggle with.
use a fast and secure VPN like NordVPN.
VPN Concerns
VPN services aren’t without their drawbacks, though. While they’re meant to protect your privacy, a VPN provider can see your web traffic and, in some cases, log it. Providers such as IPVanish have been caught red-handed logging user data and handing it to the government. You can read more about that incident in our IPVanish review.
That said, NordVPN and Surfshark are examples of providers with a commitment to security and privacy (read our NordVPN review and Surfshark review). It’s important to do your research and see if the service you want to use has anything shady in its past.
Should You Use a Free VPN?
You probably shouldn’t use a free VPN. The biggest downside is that a good VPN, in almost every case, will cost money. There are free options, but as you can see in our worst free VPNs guide, they come with unintended consequences.
There are rare exceptions to this, like Privado VPN, Windscribe and TunnelBear. In our opinion, Privado VPN is the best free VPN around, as you can read in our Privado VPN review.
However, if you’re on a budget, you can get a VPN for cheap. Providers such as CyberGhost and Private Internet Access offer unlimited plans for multiple devices for only a few dollars per month. You can learn the specifics in our CyberGhost review and PIA review.
What Is Tor? Is Tor a VPN?
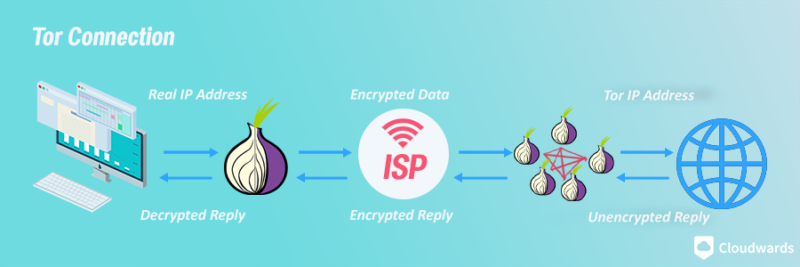
No, Tor is not a VPN. Short for ”The Onion Router”, Tor is a network that routes your internet traffic through a series of volunteer-operated servers, to ensure anonymity.
Tor is a free-to-use network of access points called nodes that work like proxies for your connection. It’s also the name of the browser you use to connect to this network. When you use the Tor browser, your connection gets routed through several of these nodes before arriving at its end destination. Traffic on the network is encrypted as well, so it’s marginally safer than a proxy.
However, like any free service, it comes with drawbacks. Like proxy servers, Tor exit nodes (the last server your connection bounces off of) are recognizable. Because of that, websites can blocklist those IP addresses and your connection.
Additionally, Tor nodes are run by volunteers who can see your traffic and potentially alter it. Many nodes are malicious and add malicious data to the packets you’re sending or receiving. They can also redirect your traffic to a copycat website and steal your login information.
Tor Security
As for privacy, not everything is sound there, either. VPN providers, such as VyprVPN (read our VyprVPN review), have consistently asserted that Tor is a subpar solution for true anonymity, and for good reason. Massachusetts Institute of Technology researchers, for example, have been able to break Tor without cracking the encryption it uses.
The basic premise is that someone who’s snooping on a Tor connection can use traffic fingerprinting to determine what content a user is accessing. The data can be monitored and the packets counted to determine where the connection is coming from and where it’s going.
who might not have your best interest in mind.
Plus, Tor is under constant scrutiny by government agencies because it’s often used for cybercrime. As you can read about in our guide to the deep web, Tor is used by criminals to connect to dark web websites in an attempt to mask their identities. Cybersecurity is made to be broken and the focus on Tor makes it all the more risky to use.
It has other usability concerns, too. Tor doesn’t work for P2P connections and is much slower than a proxy or VPN. You’re still encrypting your initial connection, but also having to bounce that connection off several servers before reaching your destination.
Which Is More Secure: VPN or Proxy or Tor?
The only way to truly protect your web traffic is with a VPN. Proxy servers are convenience- and speed-focused solutions that are suitable for bypassing basic geoblocks, and Tor focuses on brute-forcing anonymity at the cost of massive amounts of speed.
On the other hand, VPN connections provide near-unprotected speeds while keeping your traffic completely secure. Really, the only drawback is that you have to pay for a VPN. There’s really no contest between Tor, a VPN and proxy server — the VPN always wins.
Final Thoughts: Proxy vs VPN vs Tor
For most people, a VPN is the best choice, but that shouldn’t come as much of a surprise. A VPN connection is encrypted, secure and fast. Proxy servers and Tor don’t have that kind of reliability, so your security is left to speculation. That doesn’t mean they don’t have value, though.
Connecting to a VPN through Tor is a slow but effective solution for true anonymity (see our best VPN for Tor) , and proxies are a fast and low-cost solution for basic IP masking. For an all-around solution though, try NordVPN, and experience its power yourself, risk-free, with the assurance that you can get your money back within 30 days if you’re not completely satisfied.
Do you agree that VPNs are the best option, or do you prefer to use something else? Let us know your thoughts in the comments below and, as always, thanks for reading.
FAQ
You certainly don’t need a proxy server if you already have a VPN, because they essentially do the same thing, except proxy servers are worse because they don’t encrypt your traffic.
No, a proxy server will change your IP address, but it doesn’t encrypt your internet traffic like a VPN does. This means that although proxy servers are similar to VPNs, they’re inherently less secure.
A VPN will generally be faster than a proxy server if you’re using a good quality VPN.
A VPN shouldn’t override a proxy. The VPN client would encrypt your data and send it to the VPN server, which would then send it to the proxy server.


