Tor Browser Review
In 2002, the Tor Project launched a browser designed to browse the web entirely through Tor. The browser contains built-in features for accessing .onion websites and services through the anonymous Tor network. Read on to learn more about accessing the deep and dark web with Tor.
Key Takeaways:
- Created by the Tor Project in 2002, the Tor Browser is designed to access the Tor network directly without any additional software.
- Browsing through Tor will encrypt your web traffic and conceal your IP address from every website you visit.
- Since the Tor network consists of anonymous, volunteer-run nodes, some Tor nodes are operated by cybercriminals, while others are managed by law enforcement agents.
- The exit node is the most likely place for encountering cyber threats and having your privacy compromised.
In the past, users had to rely on external software to access the Tor network. In 2002, the Tor Project unveiled a browser designed specifically for optimal use of the Tor network. While it’s a great privacy browser for Tor users, it’s not intended to be an all-purpose browser for the average user, so there’s a lot of interesting stuff to cover in our updated Tor review.
This browser makes a lot of trade-offs for the sake of privacy, especially when it comes to performance. Internet users unfamiliar with Tor will probably find the Tor Browser a bit jarring to use at first. The good news is that the browser itself should be simple enough for most because it’s based on Firefox, even if the Tor network itself is an esoteric piece of technology.
The browser provides about as much online privacy as you can have while using the internet, except if you use a secure VPN. Despite the high level of privacy it offers, Tor comes with some important security risks that you should know in advance before connecting to the network, which is why we recommend using a VPN in addition to the Tor Browser (see our best VPN for Tor).
With that said, Tor and its browser shouldn’t intimidate you if you’re serious about remaining anonymous online. We’ll get into the fine details of this unique browser below.
-
01/17/2022 Facts checked
Completed a fresh review, plus added performance table and expanded features.
-
07/15/2024 Facts checked
Added information on Tor’s most recent updates, including accessibility features, letterboxing and Connection Assist mode.
Tor Browser Review: Alternatives
Strengths & Weaknesses
Pros:
- Great security & privacy
- Works with Firefox add-ons
Cons:
- Slow & inconsistent speeds
- Security issues with malicious nodes
- Some websites block access to Tor users
Before We Begin: The Tor Network & Tor Project Explained
Tor — short for “The Onion Routing” — is a decentralized network of encrypted access points that are used to disguise the user’s IP address and identity. When browsing the web with Tor, the user’s internet connection is encrypted and traffic is sent through a chain of nodes before it reaches the destination address.
Tor is used to anonymously access.onion websites on the deep web and the dark web, which are two related but distinct concepts. In short, the deep web broadly refers to websites and resources that aren’t indexed by search engines and therefore can’t be discovered as easily as websites on the surface web.
The dark web refers to non-indexed websites that are explicitly used for illicit purposes. While the term “deep web” can refer to innocuous content — such as archives, research material and intranet content — the “dark web” is a subset of the deep web for buying and selling illegal goods, distributing child sexual assault images or even hiring hit men.
However, many users simply enjoy the Tor network for the anonymity it provides while browsing the internet. Anonymity and access to non-indexed internet resources are valid and legal reasons for using the Tor network, but be aware of what you’re getting into.
Downsides of Tor
While Tor has its uses, there are some caveats to keep in mind. For example, the websites you visit may not know your actual IP address, but they may be able to identify the origin of the final node — the exit node — if the connection isn’t encrypted with HTTPS. Many websites block Tor connections, so you might have a difficult time using the internet.
Even if the website can’t compromise your privacy, some threats originate with Tor itself. Every node in the Tor network is run by volunteers and there is no way to know who can see the information you’re sending through the internet.
Tor has acquired an unsavory reputation due to the presence of cybercriminals on the network. These cybercriminals run malicious exit nodes in order to spread malware and steal personal data, which is why some sites block Tor connections.
There’s a lot more detail on this subject than we have time for here, so check out our article on the differences between Tor, VPNs and proxies. Now let’s get to the heart of the review.
Features
The Tor Browser isn’t the fullest browser in terms of features, and its privacy-first design makes some standard browser features unfeasible (e.g., device sync). Fortunately, its basis in Firefox means the Tor Browser is compatible with Firefox’s library of add-ons.
While Firefox’s selection of add-ons isn’t as extensive as Google’s, most users should have more than enough options to choose from.
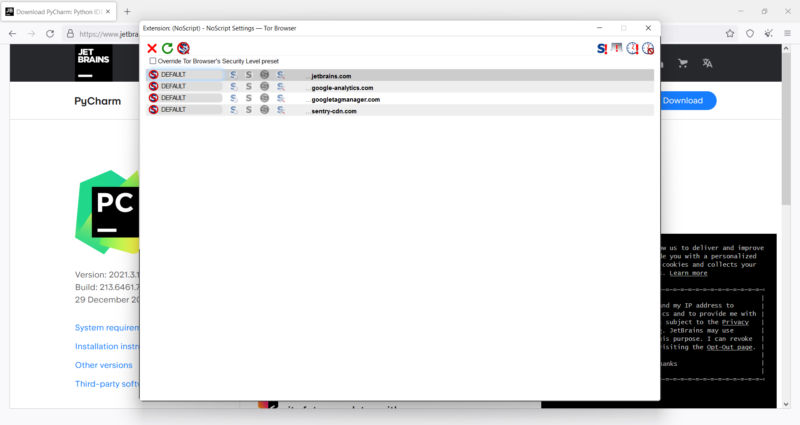
Two add-ons are enabled by default: HTTPS Everywhere and NoScript. The former will force websites to resolve their connection over HTTPS if both HTTPS and HTTP are available. The latter is an extension that automatically blocks all JavaScript code (and other content), except code from websites you trust.
The PDF reader is the same as Firefox’s. It has a simple interface with all of the standard controls for navigation, page layout and interaction with the document. The PDF reader includes a side panel where thumbnails of each individual page are vertically displayed, in addition to controls for viewing individual attachments, layers and the document outline.
Features vs Anonymity
There is no way to sync the browser across devices because it simply doesn’t make sense with Tor. Anonymity is the whole point of this browser, but transferring browser data from one device to another would require the two devices to be able to identify each other.
Saving your history, bookmarks, passwords and other data would likewise compromise the anonymity offered by the browser. In the event your browser suffers an attack, your saved data could be used to identify you and lead to further compromise.
Storing passwords in the browser is especially undesirable for this reason. We suggest using external applications for your bookmarks, passwords and whatever else. Check out our article on the best password managers for more information on secure password storage.
HTTPS-Only mode is a default setting — Tor Browser will not connect to a site that isn’t encrypted, unless you explicitly opt in. Standard Tor windows also have private browsing mode automatically enabled, meaning your history, form data and cookies are not saved. You can turn both of these features off manually in the settings menu.
Search Engine Selection
DuckDuckGo is the browser’s default search engine, and built-in options for eight other search engines are included as well. You can decide whether to use the address bar as a search engine or to add a separate search bar in the browser window. Be sure to read our search engine vs browser guide.
When you type a search query in the address bar, a dropdown menu will appear with a row of icons representing each of the nine search engines available within the browser. Clicking on a search engine after typing your query will instantly take you to the relevant results.
Bridges and Connection Assist
Some of Tor’s relay nodes are not publicly listed on its directory. These relays, called bridges, are kept secret so nationwide censorship regimes (like China’s) can’t block them. The Connection Assist feature, added to Tor Browser in 2022, automatically switches users to the bridge that will best circumvent whatever censorship they’re currently facing.
Ease of Use
Understanding Tor and configuring your connection within the browser will probably take some getting used to. Beyond its novel security design, it’s an otherwise easy browser to use. The Tor Browser is based on Firefox, so most first-time users should find its interface and settings familiar enough to pick up without too much of a learning curve.
Tor Project gains some points with us for constantly working to make its browser more usable. Most recently, it’s added new features for accessibility devices, redesigned the circuit display to be more readable and simplified the error messages on .onion sites, making troubleshooting simpler for non-technical users.
Desktop
The desktop interface is based on Firefox’s Quantum browser engine, so most of the screen is taken up by the web page itself. The interface simply consists of the tab bar and the address bar, plus a few controls for navigation and settings.
The browser favors horizontal tab scrolling instead of minimizing tabs once you’ve opened too many tabs at once. Once your tabs go off the screen, a button appears for a dropdown menu that lists all your open tabs.
Updates in late 2022 added multi-locale support, enabling users to change languages without installing extra software. The same update added font packs to ensure those languages can render.
Mobile
The Tor Browser is one of the best browsers for Android. Although there’s no iOS version, the Tor Browser website recommends a separate browser for iOS users called the Onion Browser. This review will be limited to the Android mobile browser.
The mobile version of the browser features a simple interface with the address bar and tabs at the bottom of the screen rather than the top. For the most part, it works the same as its desktop counterpart. It uses a purple theme and works like a private window by default. HTTPS Everywhere and NoScript are enabled automatically.
Screenshots are prohibited for security purposes unless you manually allow them. The settings menu includes a feature for requesting the desktop versions of websites in case the mobile-optimized site isn’t suited to your purposes.
Performance
Speed is where the Tor Browser suffers the most. Its security configuration is precisely the reason for its inconsistent and slow speeds. Encryption will always slow down your internet connection at least a little bit, as will proxies.
The Tor Browser is configured to send your internet traffic through three nodes before reaching the requested website, so each node along the way drags down the overall speed of the browser.
You’ll get different nodes each time you establish a Tor connection, so the hardware specifications and location of each node will vary and have their own effects on your speed. Some connections will be slower than others, but the browser is very slow overall.
Speed Tests
The first speed test is Speedometer, which gives a good overview of the browser’s overall performance. It runs 480 web applications and records how fast the browser handles each of them. The averaged results indicate how many runs per minute the browser is capable of. It was the second slowest browser in this test, besting only Puffin (read our Puffin review).
| Benchmark Test: | Speedometer |
|---|---|
| Browser | Runs per Minute |
| Microsoft Edge | 131 |
| Chrome | 121 |
| Opera | 116.6 |
| Brave | 102 |
| Chromium | 102 |
| Vivaldi | 97.3 |
| Mozilla Firefox | 95.5 |
| Tor Browser | 67.11 |
| Puffin | 49.5 |
JetStream 2 tests JavaScript and WebAssembly programming techniques and averages the results with a geometric mean. Instead of getting a numerical score, our result was simply “infinity” after a series of runs that ranged from very slow to very fast.
| Benchmark Test: | JetStream 2 |
|---|---|
| Browser | Score |
| Microsoft Edge | 134 |
| Chromium | 129.732 |
| Chrome | 125.917 |
| Opera | 121.802 |
| Brave | 116.936 |
| Vivaldi | 116.540 |
| Puffin | 80.519 |
| Mozilla Firefox | 80.131 |
| Tor Browser | Infinity |
We don’t know what this is supposed to indicate, but it doesn’t sound like an optimistic score. If anyone knows what this means, let us know in the comments.
Finally, we have the third test, Motion Mark, which tests the browser’s graphics-rendering capabilities. Our Tor nodes on this test were much faster than on the others, but we could still see a lot of lagging in the on-screen graphics.
| Benchmark Test: | Motion Mark |
|---|---|
| Browser | Score |
| Microsoft Edge | 517 |
| Chrome | 496.32 |
| Brave | 444.67 |
| Chromium | 432.50 |
| Tor Browser | 430.55 |
| Opera | 373.27 |
| Vivaldi | 285.25 |
| Mozilla Firefox | 145.93 |
| Puffin | 52.93 |
If you want a fast browser, don’t look at Tor to provide that. Tor is made for privacy, not speed.
Security
The browser comes with three levels of security: “standard,” “safer” and “safest.” Each level disables more website features than the previous one in order to mitigate the opportunities for malware to get a foothold into your system. Strict security will affect certain website elements like images, media and scripts, and may cause them to malfunction.
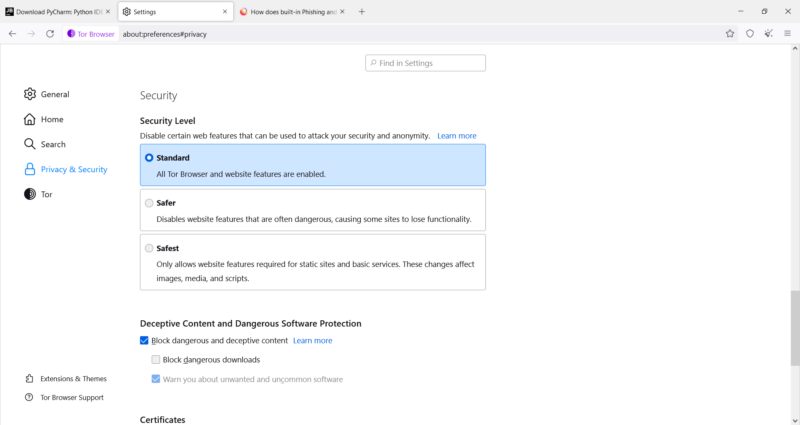
It also inherits Firefox’s malware protection settings under “deceptive content and dangerous software protection.” Beneath this heading are two settings for blocking dangerous downloads and enabling warnings for “unwanted and uncommon software.”
The “deceptive content and dangerous software” feature grants Firefox, Google and other parties access to some of your browser data. It’s disabled by default, presumably because the Tor Browser is intended to be a privacy-oriented browser.
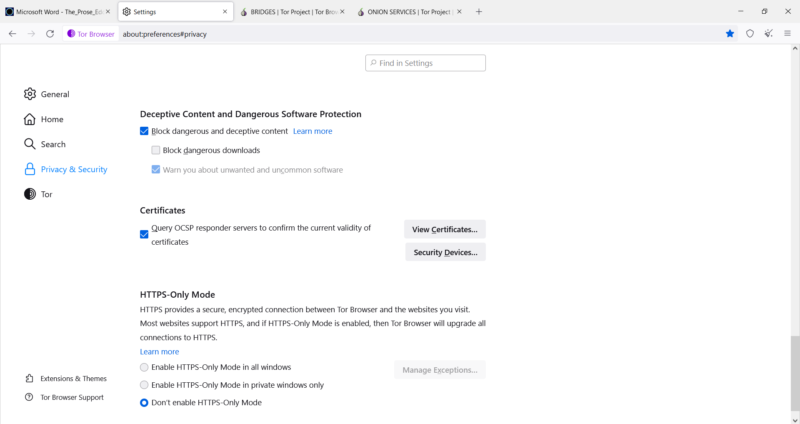
Beside the “deceptive content and dangerous software protection” heading is a link (titled “learn more”) to Firefox’s privacy policy, which explains the two circumstances under which Firefox (and, by extension, the Tor Browser) communicates with other entities.
The browser will communicate some data about your browser and usage when Mozilla updates its lists of known phishing and malware sites. Mozilla claims that it won’t send any of your personal data or data about the sites you visit.
The other occasion is when you visit a reported malicious website. The browser will check the website before blocking it to see if it’s been removed from the list of reported sites since your browser’s last update. It shares only partial information taken from the address, but not the whole address.
For more information on secure web browsers, check out our list of the most secure browsers.
Privacy
Privacy is the main purpose of the Tor Browser. Unlike other browsers, which must rely on external software, this browser features built-in capabilities for accessing .onion sites through the Tor network.
Your connection is encrypted and travels through three nodes before finally reaching the destination web address. On the desktop version, you can click the green padlock in the address bar to see the location of every node in the Tor circuit.
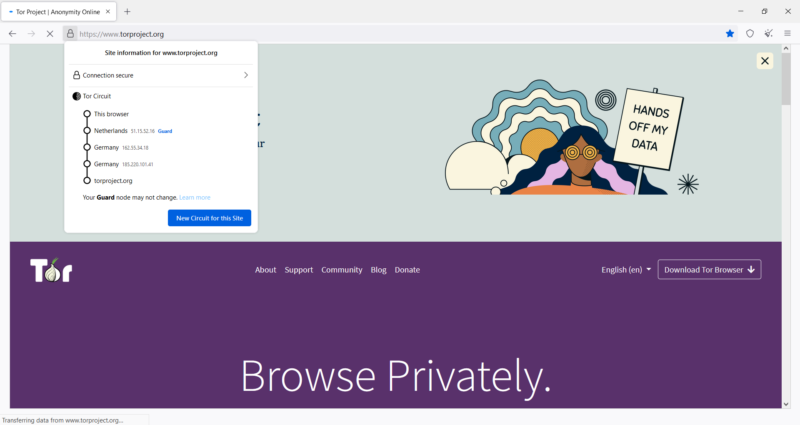
Tor Browser has a few built-in touches that counter various methods used to invade your privacy. For example, letterboxing adds invisible changes to the display size of each website window, so it’s harder to identify your device based on its screen size (a surveillance practice known as device fingerprinting).
The browser comes with buttons for ending and creating new Tor circuits. Under the settings menu, “new identity” will clear all browser data and restart it from scratch so you’ll have three new nodes to work with. This feature comes in handy when your connection is slow, or if the website is refusing your connection.
Nodes Managed by Other Tor Users
The nodes are one of the most risky aspects about using Tor. Tor consists of a network of nodes run by volunteers, so there’s no way to tell who’s operating the machines your connection is running through.
Granted, no individual node can identify where your communications are coming from or where they’re going, but Tor has a negative reputation for the malicious actors running Tor nodes to steal information and spread malware. The trouble is magnified by the exit nodes because your connection between the final node and the destination website isn’t encrypted.
That’s why you should exercise caution when logging in to any of your accounts while using this browser. Your accounts will recognize the exit nodes as an attacker trying to log in from an untrusted device, so you may get locked out of your accounts, or at least set off irritating security alerts.
If you’re unlucky enough to get a malicious exit node, you could inadvertently give an attacker your login credentials as well. Conversely, you may wind up with someone else’s unencrypted data, which may lead to legal trouble.
Law enforcement agencies operate Tor nodes as a method of catching cybercriminals, and you wouldn’t want your browsing to be mistaken for criminal activity.
Unencrypted exit nodes are best dealt with by using a VPN. A virtual private network encrypts your internet traffic and sends it through an intermediary server before it reaches the destination website. If you’re serious about protecting your internet privacy, then we recommend reading our article on the best VPN services to learn more.
The Verdict
The Tor Project created its browser for the singular purpose of having a dedicated interface for browsing the web over the Tor network. As such, it’s a double-edged sword — it’s the best browser for Tor enthusiasts, but it will alienate most other users.
While it excels on the privacy front, it comes at the cost of speed, and it will be challenging for users unfamiliar with Tor to use the browser. While this sounds like a condemnation, it must be remembered that the browser is meant to fulfill a single purpose and is not intended to be everyone’s default browser for everyday use.
Taking that into account, this browser is the best way to use the Tor network. However, first make sure to understand Tor, how it works, and the risks of using this infamous technology.
What do you think of the Tor Browser? Should Tor be avoided at all costs? Is it the best way to browse with Tor, or do you prefer to use separate software to access Tor? Let us know what you think in the comments below, and as always, thank you for reading.
FAQ
Law enforcement agencies are capable of identifying Tor connections. Using Tor or the Tor Browser is not illegal, but some authorities operate Tor nodes in order to catch cybercriminals on the network.
The browser software itself is safe to use; however, we can make no guarantees about the safety of the individual Tor nodes. Cybercriminals are known for using Tor exit nodes to spread malware and steal data, while others are operated by law enforcement agents. That’s why you should use a VPN in addition to Tor for extra safety.



