Are VPNs Safe, Are They Legal & How to Make Them Safer in 2025
A virtual private network (VPN) is an essential privacy and security tool. However, some VPNs pose a security risk instead. In this article, we answer the question "are VPNs safe?" and explain how a good VPN keeps you safe. You’ll also learn how to get the best protection from your VPN.
Are VPNs safe? If that question is on your mind, we have answers for you in this article. VPNs have been hailed as a vital online security tool. However, it can be tricky to know if those claims are true or merely marketing jargon. This post delves into the security and privacy features of VPN providers to help you understand what makes a VPN safe and how it protects your privacy.
If you’re looking for a quick answer on the safety of VPNs, it’s safe to use a VPN as long as you choose a good VPN service with excellent privacy and security features. However, keep reading for more detailed evaluation: You’ll also learn whether you can be tracked or hacked while using a VPN service, plus how to maximize your VPN’s security and privacy features.
-
02/29/2024 Facts checked
We updated the article with more details and more insight.
How Secure Are VPNs?
Some VPNs provide robust online security, while others leave you exposed to hackers and snoops. To determine whether a VPN is secure, first check the encryption and protocols it offers. We’ll explain why these features are important later in the article, but suffice it to say that they encrypt and anonymize your traffic so no third party can access it.
Most secure VPNs offer a kill switch to prevent data leaks, double VPN servers to encrypt your traffic twice, obfuscation to disguise your VPN traffic as normal traffic and ad and malware blockers to help you browse safely. Safe VPNs also run a strict no-logs policy backed by RAM-only servers and consistent independent audits.
Protect Your Privacy. Get Our Free VPN Guide Now!

- Comprehend the essential role a VPN plays in safeguarding your digital life
- Gain a deep understanding of how VPNs function under the hood
- Develop the ability to distinguish fact from fiction in VPN promotions
What Makes a VPN Safe?
A VPN is safe if it has reliable privacy and security features. Below is a breakdown of the main safety features you should look for in a VPN. Many of the best VPN providers have these features.
- Secure protocols: VPN protocols govern how data moves between your device and the VPN server. The most secure protocols are OpenVPN, WireGuard and IKEv2.
- A kill switch: This disconnects your device from the internet when your VPN connection drops. Some VPNs only offer a system-wide kill switch, while others have an app-level kill switch.
- RAM-only servers: These run on volatile memory, erasing any saved data each time the server restarts.
- Malware-blockers and ad-blockers: These prevent you from landing on malware-filled sites and stop ads from appearing on your screen.
- Double VPN or multi-hop servers: These servers route your traffic through two VPN servers instead of one. This adds an extra layer of protection to your VPN traffic.
- Obfuscation: This feature makes it difficult for anyone to know you’re using a VPN. Obfuscation is necessary if you’re browsing with a VPN in a restrictive country like China or Russia.
- No-logs policy: A safe VPN must not log or share personal user details such as IP addresses or connection timestamps.
- VPN provider location and history: Where a VPN is located can affect how your information is handled. A safe VPN should not have a history of unaddressed breaches or leaks.
How Does a VPN Provider Protect Your Privacy?
A VPN keeps your online information private through a combination of features, including encryption, protocols, perfect forward secrecy and a zero-logs policy. Let’s examine these features in detail.
Encryption
If your data is encrypted, it means that it has been turned into gibberish or an unreadable format to any outside eye. An encrypted VPN scrambles your internet traffic so that even if hackers access it, they’ll only see a string of letters and numbers that make no sense.
There are various ways of encrypting user data. Most of the safest VPNs use AES encryption with the OpenVPN protocol. Short for Advanced Encryption Standard, AES is one of the most popular ciphers. It uses a symmetric-key algorithm for encryption, which means the same encryption key is used for both encrypting and decrypting data.
AES comes in many forms: AES 128, 192 and 256. AES-256 is the strongest version — the larger the encryption bit, the longer it takes to crack. That said, any of the AES encryption bits would take millions of years to break. We won’t get into all the nitty-gritty details here, but if you want to learn more about AES, read our article on AES encryption.
Many secure VPNs also use the ChaCha20 encryption, which is another symmetric key algorithm. ChaCha20 also is 256-bit, which means it’s as secure as AES. However, one difference between the two is that ChaCha20 encrypts user data in streams: one bit at a time. As a result, it’s faster than AES when implemented at a software level — that’s why it works with the quick WireGuard protocol.
| Encryption | Strength |
|---|---|
| AES encryption | Very secure |
| ChaCha20 | Very secure |
VPN Protocols
A VPN protocol is a set of rules guiding how data is transmitted between the VPN server and your device. The choice of VPN protocol will affect the level of security and speed you enjoy. OpenVPN is the gold standard and is the default for some VPN providers. It provides a good combination of speed and security.
Some VPNs (ExpressVPN, for instance) let you switch between OpenVPN TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). Choose TCP if you want a reliable connection, but choose UDP for faster internet speed. If this all sounds like gibberish to you, check out our guide on encryption, which explains it a bit more.
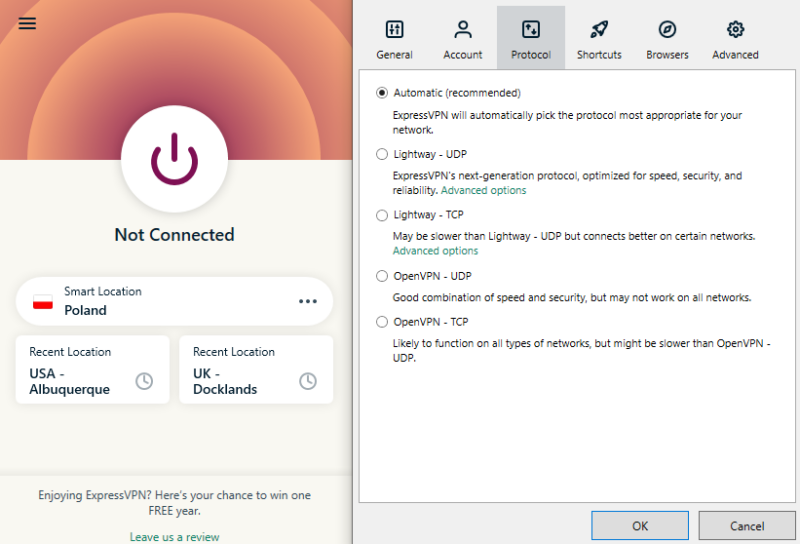
between OpenVPN TCP and UDP.
Many VPNs also offer the IKEv2/IPSec protocol, which is ideal for mobile users because of its reconnection capabilities. When switching between a mobile network and WiFi, your VPN connection can drop momentarily. Using the IKEv2 protocol will prevent such drops and potential data leaks.
Some premium VPNs also offer the WireGuard protocol. WireGuard’s code base is shorter, making it faster without compromising VPN security. It uses the ChaCha20 stream cipher to provide perfect forward secrecy (more on that soon). We recommend switching to the WireGuard protocol to perform data-intensive tasks like streaming or gaming.
We’ve noticed that VPNs with proprietary protocols build them on WireGuard, probably due to its smaller codebase. For example, NordVPN’s NordLynx protocol is WireGuard-based, which helps it offer better speeds than other available protocols.
Here’s a summary of the most popular secure VPN protocols.
| Protocol | Encryption | Available on all major OSes? |
|---|---|---|
| OpenVPN | AES | |
| WireGuard | ChaCha20 | |
| IKEv2 | AES |
Other Protocols
We’re hesitant to recommend any protocol besides the three mentioned above. Most others are either dated or don’t have the requisite security. For instance, some VPNs offer PPTP, which has weak security because it uses the outdated Microsoft Point-to-Point Encryption (MPPE). It also has short encryption keys, which makes it easy to crack.
There’s also L2TP, which is basically a tunneling protocol and doesn’t offer any encryption. SSTP has encryption, but it’s hard to set up on non-Windows devices and suffers from connectivity issues, which can affect streaming and torrenting. You can learn more about protocols in our VPN protocol breakdown.
Perfect Forward Secrecy
Perfect forward secrecy (PFS) allows a VPN to generate different encryption keys for each VPN session. Without PFS, if a hacker discovers one key, much more of your traffic becomes vulnerable.
Let’s explain that using an analogy. Imagine keeping your private diary in a safe box. If thieves get their hands on the box, they might keep it, hoping to find the key to learn your secrets. Now, imagine instead that each diary entry is locked into different safe boxes. Few thieves would want to keep so many boxes in the hopes of finding all those individual keys to make sense of your data.
Perfect forward secrecy on a VPN works much the same way. It generates new encryption keys each time you connect to a VPN server. Even if a hacker gets access to your encrypted data, they can only attempt to decrypt a small portion of your traffic before the key changes again. This means one key is unlikely to unlock anything useful.
ExpressVPN is an example of a VPN that implements perfect forward secrecy well. It changes your encryption keys each time you connect to a server, terminate the encrypted connection or change networks. If you stay connected to a server, ExpressVPN will change your encryption keys every 15 minutes. Read more about the VPN in our ExpressVPN review.
No-Logs Policy: Do VPN Services Share Your Data?
Almost every VPN shares some data with vendors and partners. Some share only anonymized data, while others share information that can be traced to you. To find out which information your VPN shares, examine its privacy policy.
For example, NordVPN and Hotspot Shield both indicate in their policies that they share certain information with service providers and their parent companies. However, unlike Hotspot Shield, NordVPN doesn’t log sensitive information like your internet protocol (IP) address or connection logs.
The only information NordVPN shares is anonymized payment data. Plus, NordVPN runs RAM-only servers, which wipe browsing activity with every reboot — it couldn’t share your sensitive information if it wanted to. Read more about it in our NordVPN review.
To ensure your data is safe, choose VPNs that adhere to a strict no-logs policy. However, don’t take what they say at face value. Rather, read their privacy policy and confirm they don’t log sensitive data. We also recommend checking whether the VPN has been audited recently. An independent audit by a reputable firm can confirm that a VPN sticks to its logging policy.
The best VPNs undergo audits every two years or so. Be wary of VPNs that have never undergone an audit, that were last audited more than three years ago or that have no published audit results. In addition, verify that the auditing firm is trustworthy; we’ve seen some VPNs claim to receive audits from suspicious firms that don’t list the VPNs as clients.
Can You Be Tracked if You Use a VPN Service?
It depends on how trustworthy the VPN is. If you use a secure VPN service, your online traffic and IP address can’t be tracked because it encrypts your data. However, a poor VPN can leak your IP address and web traffic (whether through negligence or on purpose), enabling your internet service provider, governments and hackers to see your online activity.
Your online behavior can also lead to tracking. For instance, advertisers can gather data on you when you accept cookies, log in to some sites or fill out some forms. You could also be tracked if you download malware on your device or willingly give up information on social media.
Interestingly, many VPNs now come with built-in ad and tracker blockers. For example, Private Internet Access offers MACE, which stops trackers from following your internet connection. It also alerts users about sites that have malware. Read more about the VPN in our PIA review.
Can a VPN Be Hacked?
Yes, a VPN can be hacked, but it’s not common among premium VPNs. VPNs vulnerable to hacks usually use weak encryption and outdated protocols such as PPTP or L2TP. They also don’t have perfect forward secrecy.
VPN Server Breaches
Before choosing a VPN, check their server breach history. See what type of vulnerability was exposed in the breach or hack, and how the company responded to fix it and inform users.
Even the best VPNs might have a breach history. For example, in 2018, an intruder accessed NordVPN’s remote server in Finland. The breach happened due to poor configuration in one of NordVPN’s partner data centers. However, no identifiable user credentials were found or compromised during the breach. Plus, NordVPN promptly came out with a statement explaining the events and severed ties with the partner.
their server and the actions they took.
In comparison, one of the biggest VPN breaches occurred in 2023 with SuperVPN, a free VPN service. Cybersecurity researcher Jeremiah Fowler uncovered the data breach, which compromised over 360 million user records. The information revealed included email addresses, geolocation data, records of servers used, and websites visited.
Do your research on the VPN to make sure they take their security seriously, and if they have a breach, that they responded in a quick and effective manner.
How Ownership & Jurisdiction Impact a VPN’s Safety
If you read VPN privacy policies, you’ll notice that most of them share user information with their parent companies. Depending on how that VPN company treats user data, your information could be sold to advertisers or shared with other parties. When choosing a VPN, check the parent company’s privacy policy and history to ensure it’s safe.
A VPN’s location also has a significant impact on your privacy. Some are based in invasive jurisdictions that might ask VPNs to log and share sensitive user data. For example, India has data regulations that require VPNs to collect and store user data for five years. As a result, every reputable VPN provider removed their physical servers from the country.
Choose VPNs that are located in countries with privacy-friendly laws. For example, Proton VPN is based in Switzerland, NordVPN is based in Panama, and ExpressVPN is headquartered in the British Virgin Islands. These are all privacy-friendly countries, as you can see in our article on the countries with the best cloud privacy laws.
Are Free VPN Providers a Privacy Risk?
Yes, most free VPN services can pose a privacy risk if they don’t have a strict no-logs policy. An unfortunate common occurrence with free VPNs is that they collect user data and sell it to advertisers to make money.
Even worse, some free providers can infect your device with malware, which cybercriminals can use to access your traffic. Other free VPNs suffer IP and DNS leaks, meaning your real IP address would be visible to anyone looking for it. There’s more about such VPNs in our worst VPNs list.
However, not all free VPNs pose a security risk. If you read our best free VPNs piece, you’ll discover many free VPNs that don’t log sensitive information or suffer from leaks. Proton VPN tops that list, boasting excellent security and privacy credentials. It also offers unlimited data, which is ideal for streaming and gaming. Read more about it in our Proton VPN review.
How to Use a VPN Safely
Connecting to a VPN doesn’t automatically mean you’re using it safely. Below, you’ll find helpful tips and tricks to help you maximize your VPN’s security.
- Avoid sharing too much personal data with the VPN: Choose a VPN with RAM-based servers, i.e. no way to collect any data.Otherwise, use a temporary email address or with cryptocurrency so you don’t hand over too much data. Mullvad VPN even lets you pay with cash, which you can read more about in our Mullvad review.
- Activate the kill switch: Go to the VPN’s settings and ensure the kill switch button is turned on. This will prevent data leaks if your VPN connection drops.
- Connect to a secure protocol: Switch to OpenVPN or WireGuard to use a VPN safely. Avoid outdated protocols like PPTP.
- Activate obfuscation: Take advantage of obfuscation if you’re in a country that tracks internet activity. Implementing obfuscation differs from VPN to VPN. For NordVPN, you’ll have to connect to obfuscated servers, whereas Surfshark uses NoBorders mode. Other VPNs, like Windscribe and Proton VPN, offer stealth protocols.
- Use your VPN’s auto-connect features: Set your VPN to connect automatically to specific servers before opening websites. Most VPNs also let you decide which WiFi networks to protect. This prevents you from accessing the internet without VPN protection.
Do You Really Need a VPN for Online Privacy?
Yes, a VPN is an important tool for your online privacy. A VPN provides a cover for your online activity, changing your original IP address to make it seem like you’re in another location. Moreover, secure VPNs encrypt your traffic so no one can understand it. This ensures that third parties, such as your internet service provider, hackers and governments, can’t figure out your location and web traffic.
Final Thoughts
Using a VPN is safe as long as you choose a VPN with solid privacy and security features. Before subscribing to or downloading a VPN, check that it has vital features like a kill switch, protocols, perfect forward secrecy, leak protection and a zero-logs policy.
Do you still have questions about the security and privacy that VPNs offer? Which VPN is your favorite? Have you had any challenges using certain VPNs? Share your thoughts and opinions with us in the comments section below. As always, thanks for reading.
FAQ: Are VPNs Safe?
Using a VPN is not dangerous unless you use a poor one that exposes your location or infects your device with malware. Some dangerous VPNs also sell your information to third parties for profit.
It’s not illegal to have or use a VPN in most locations around the world, including Europe and North America. However, some countries, especially those with strict internet rules, have banned or restricted VPNs.
You can have a VPN running all the time without any problems. However, most VPNs have a split tunneling feature that lets you decide which traffic goes through the VPN tunnel and which doesn’t.
You can check a VPN’s safety by determining whether it has functioning key security features such as a kill switch, various protocols and leak protection. In addition, verify that the VPN has a no-logs policy and sticks to it.


