A Full VPN Protocols List in 2025: Explained and Compared
VPN protocols are the parts that make virtual private networks tick, but most users know little about them. This guide will explain what the different protocols do, what they’re good at, and when you should use each one.
VPNs have become ubiquitous in home offices around the world. They are responsible for safeguarding internet connections and protecting sensitive data for a vast number of users. VPN protocols are what make a VPN work, establishing the secure connections that let you surf the web without fear.
Not all VPN service providers are created equal, and a large part of their effectiveness depends on the underlying VPN protocol they use. This guide will delve into what VPN protocols are and explore the nuances, strengths and weaknesses of each option.
-
04/27/2024 Facts checked
Rewritten to include more practical information on choosing a protocol for a specific purpose.
-
06/26/2024
Updated the article to add custom graphics.
What Are VPN Protocols?
A VPN protocol is a set of rules and specifications that govern how a virtual private network (VPN) establishes an encrypted tunnel between your device and the VPN server. VPN protocols dictate several essential aspects of a VPN’s functioning, such as encryption protocols, authentication mechanisms and data transmission processes.
The encrypted tunnel that the VPN establishes secures your internet connection, shielding your online activities from prying eyes, such as internet service providers (ISPs), hackers or even government surveillance agencies. This is why it’s important to only use secure protocols, as well as ones that match your use case.
VPN Protocols Comparison
The table below compares some of the key features and supported platforms for the major VPN protocols.
| VPN Protocol | Encryption | Handshake | Mobile Support | Speed | Obfuscation | Open Source |
| OpenVPN | AES-256 | TLS/SSL, ECC | Yes | Good | Yes | Yes |
| WireGuard | ChaCha20 | Curve25519 | Yes, native on Android | Excellent | Limited | Yes |
| IKEv2/IPsec | AES-256, 3DES | IKEv2 | Yes | Very good | Limited | No |
| L2TP/IPsec | AES-256, 3DES | L2TP, IPsec (separate) | Yes | Good | Limited | No |
| SSTP | TLS/SSL | TLS/SSL | No | Poor | Yes | No |
| PPTP | MPPE (RC4) | MS-CHAPv2 | No | Poor | No | No |
The performance and security characteristics of a VPN protocol may vary depending on the VPN provider and its custom configuration.
6 Types of VPN Protocols Explained
There are six major VPN protocols used in VPN applications today:
OpenVPN — Best VPN Protocol for Reliability
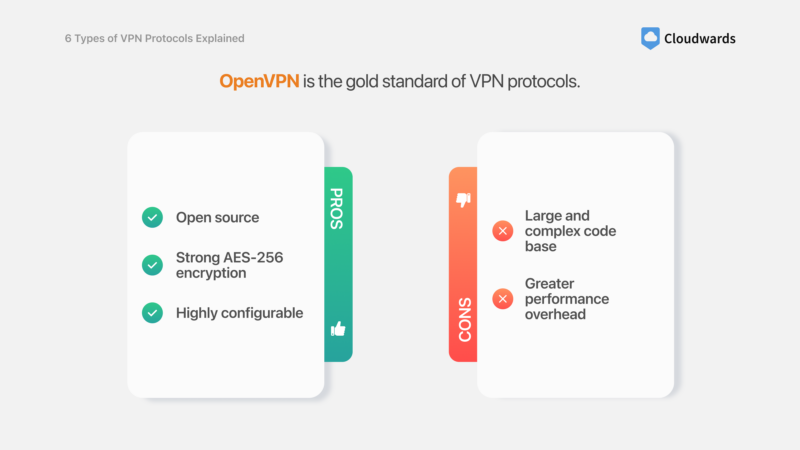
Pros:
- Open source
- Strong AES-256 encryption
- Highly configurable
Cons:
- Large and complex code base
- Greater performance overhead
OpenVPN is widely regarded as one of the most secure and versatile VPN protocols, with robust encryption and authentication methods. Its open-source nature allows for security audits, though its large codebase can hamper auditing and make it more susceptible to attacks if not properly maintained. Its unwieldy code also creates more performance overhead compared to newer protocols.
OpenVPN is also considered the most stable VPN protocol. It’s compatible with various operating systems, including Windows, macOS, Linux and Android, making it a popular choice among VPN providers and users alike.
WireGuard — Best Protocol for Security & Performance
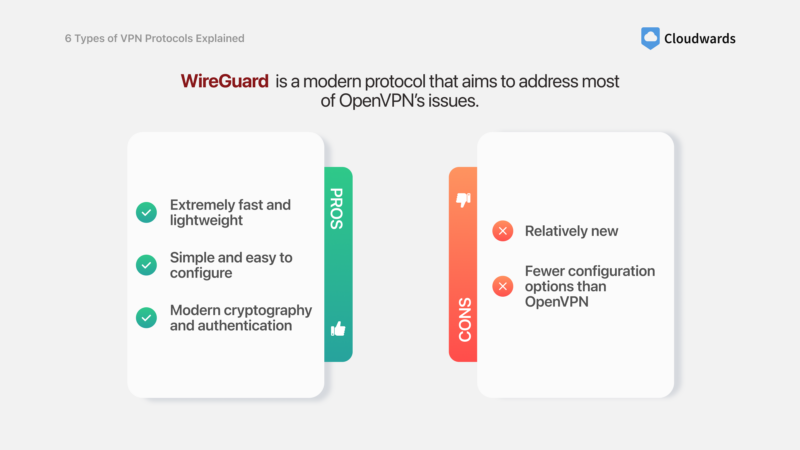
Pros:
- Extremely fast and lightweight
- Simple and easy to configure
- Modern cryptography and authentication
Cons:
- Relatively new
- Fewer configuration options than OpenVPN
WireGuard is another open-source protocol that has gained significant traction thanks to its exceptional speed and kernel-level access. With a lean codebase and cutting-edge cryptography, this secure VPN protocol provides excellent security while minimizing overhead. Its streamlined design makes it easier to audit and less susceptible to attacks than the complex OpenVPN.
WireGuard works on all major operating systems, even integrating into the Windows, Linux and Android kernels for increased performance. Mac and iPhone users might see less of a speed difference compared to OpenVPN.
IKEv2/IPsec — Best Protocol for Mobile Devices & Seamless Reconnection
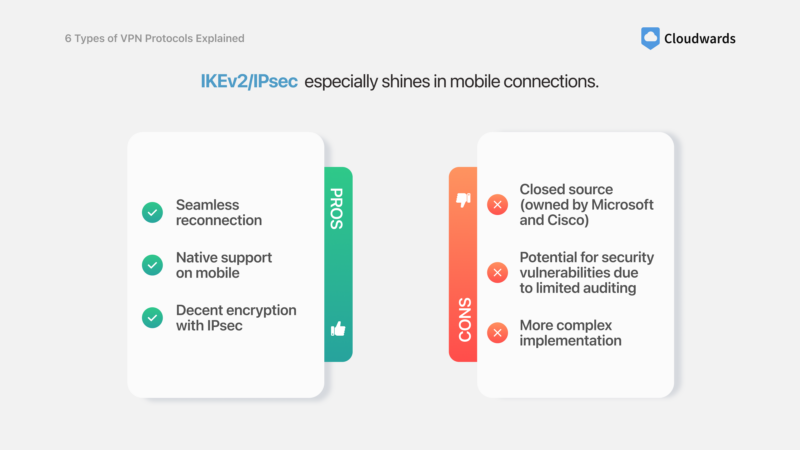
Pros:
- Seamless reconnection
- Native support on mobile
- Decent encryption with IPsec
Cons:
- Closed source (owned by Microsoft and Cisco)
- Potential for security vulnerabilities due to limited auditing
- More complex implementation
IKEv2/IPsec is a VPN tunneling protocol that uses the Internet Protocol Security (IPsec) encryption cipher combined with the fast reconnection abilities of IKEv2 (Internet Key Exchange Version Two). It’s a very stable protocol that can switch seamlessly between different networks — a great advantage for mobile devices that frequently swap between WiFi and mobile data.
L2TP/IPsec — Best VPN Protocol for Compatibility With Older Systems
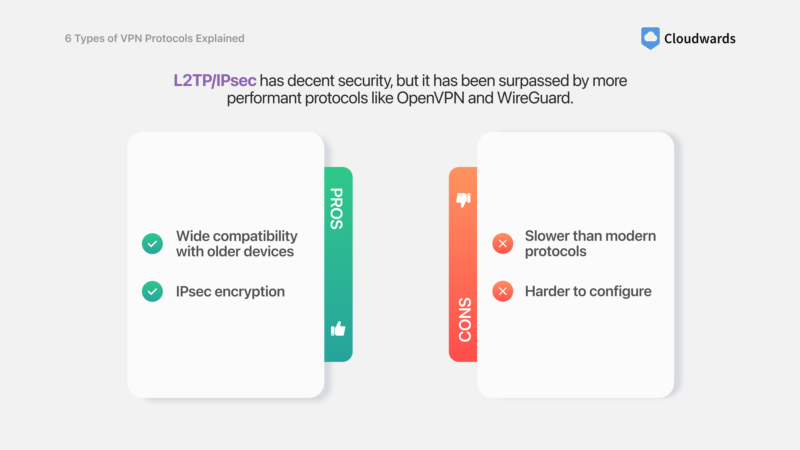
Pros
- Wide compatibility with older devices
- IPsec encryption
Cons
- Slower than modern protocols
- Harder to configure
Layer 2 Tunneling Protocol (L2TP) is an older VPN protocol that — when combined with the IPsec suite for encryption — presents a secure and widely compatible VPN solution. While it may not offer the same level of performance as more modern alternatives, L2TP is still a secure protocol thanks to the IPsec component.
One of the main advantages of the L2TP/IPsec protocol is its broad compatibility with older devices that may not support newer protocols. However, the protocol’s performance is often worse than other protocols, and you have to configure L2TP and IPsec separately (a flaw shared with IKEv2/IPsec).
PPTP — Use in Legacy Systems Only (Not Recommended for Security)
Pros:
- Compatible with older systems
Cons:
- Security is essentially nonexistent
The Point-to-Point Tunneling Protocol (PPTP) was the first widely available VPN protocol, initially released on Windows 95. This protocol was developed by Microsoft, and Harvard lecturer Bruce Schneier found that it was susceptible to all kinds of attacks — it’s now considered defunct. We dive deeper into PPTP’s security failures in our article comparing it to OpenVPN.
Though it still comes preinstalled on all major desktop and mobile operating systems, nowadays it’s mostly used in legacy systems that rely on older software. Most VPNs don’t support PPTP, but if you come across one that does, we suggest avoiding it if another protocol is available.
SSTP — Best Used for Niche Applications
Pros:
- Good at bypassing censorship
- Native Windows support
Cons:
- Limited compatibility with other OSes
- Closed source
- Owned by Microsoft
The Secure Socket Tunneling Protocol (SSTP) is another protocol that Microsoft developed as an “upgrade” from PPTP and L2TP/IPsec. As a closed-source protocol, SSTP isn’t auditable by the public at large, which means it could harbor flaws that we aren’t aware of yet.
It’s natively supported on Windows, which can be advantageous for bypassing network restrictions or censorship. However, its compatibility is also limited to these systems, making it an unpopular choice for commercial VPN applications when compared to better alternatives like OpenVPN, IKEv2 and WireGuard.
What About Proprietary Protocols?
We generally advise our readers to avoid proprietary protocols because they are often closed source, like Hotspot Shield’s Catapult Hydra protocol. Closed-source protocols lack transparency, so it’s hard to verify their security claims or assess potential vulnerabilities.
Having no opportunity for community reviews can raise concerns about undisclosed weaknesses or possible security backdoors. That’s why it’s crucial to thoroughly research the provider’s reputation, transparency practices and any independent third-party security audits.
That said, some proprietary protocols are just as good — if not better than — other popular VPN protocols. A solid example is ExpressVPN’s Lightway protocol, which is completely open source and a top performer in our VPN speed test. Another example is NordVPN’s NordLynx protocol. While this is a branded product with a proprietary solution, it’s only a slight modification of the WireGuard base.
What Is the Best VPN Protocol?
Although people will often designate OpenVPN or WireGuard as the best VPN protocol, the reality is that there is no universal “best” VPN protocol. The ideal VPN protocol often depends on your specific needs and priorities. Here are some important factors to consider when selecting a VPN protocol:
- Security: The chosen VPN protocol must be airtight, use modern encryption and ideally be open source.
- Speed & performance: All VPN protocols reduce your internet speed, but some are lighter than others.
- Operating system & device compatibility: Some VPN protocols only work on certain devices or work better on operating systems where they have a greater degree of kernel access.
- Content unblocking ability: VPN protocols operating on the same ports as regular HTTPS traffic will make your activity look like regular online traffic, so it will be harder for geoblocking systems and firewalls to detect. Obfuscation helps with internet access in restrictive countries like China.
The Most Secure VPN Protocols
- OpenVPN (TCP)
- WireGuard
When it comes to security, both OpenVPN and WireGuard are considered highly secure options, leveraging robust encryption algorithms and authentication methods that are practically unbreakable with today’s computing power.
OpenVPN’s use of AES-256, combined with its support for various authentication mechanisms, provides a multi-layered security approach. However, its large codebase increases the potential attack surface compared to the dainty WireGuard.
On the other hand, WireGuard employs ChaCha20 encryption and Curve25519 for key exchange, both of which are modern and highly secure cryptographic algorithms. However, this simplicity can also limit where it can be applied, as WireGuard lacks the configurability of OpenVPN.
In practical terms, OpenVPN and WireGuard are both highly secure when properly implemented and maintained, making it difficult to definitively declare one as the most secure VPN protocol.
The Fastest VPN Protocol for Gaming
- WireGuard
- IKEv2
Gaming with a VPN is really only recommended on the fastest possible protocols, as high speeds and low latency are crucial factors. Here, we can easily declare WireGuard and IKEv2 as the two fastest VPN protocols, at least on paper.
Both protocols are slim and streamlined, which contributes to their fast speeds. WireGuard even has kernel access on Windows, Linux and Android, which means it performs even more efficiently on those operating systems.
But gaming requires more than just speed. The best VPN protocol for gaming must be able to reconnect fast enough in case of a network drop — both of these protocols excel in that area as well.
We’d be hard-pressed to recommend just one protocol, but the kernel-level WireGuard should technically perform better for gaming applications, despite having no kernel access on Mac and iOS (though honestly, who games on a Mac?).
The Best VPN Protocol for Streaming
- OpenVPN (UDP)
- WireGuard
- IKEv2
Like gaming, streaming relies on speed, but it also requires content unblocking capabilities. This is because most streaming services lock their content based on your country or geographic region (this is called geoblocking or geofencing), as we mention in our guide on the best VPN for Netflix.
OpenVPN over UDP is faster than its default TCP counterpart, making it a good option for high-quality streaming. Additionally, its ability to run on ports that aren’t typical for VPN connections lets it pass geofencing systems undetected.
WireGuard and IKEv2 are also excellent choices for streaming due to their high-speed performance and efficient encryption processes. Plus, their ability to quickly reestablish a secure connection makes them the best choice for streaming on the go.
However, it’s worth noting that while the protocol choice does play a part, the ability to unblock content will depend on the streaming service being accessed, as well as the VPN provider’s own obfuscation techniques. Some VPNs use rotating IP addresses and specialized streaming servers to enhance their unblocking ability beyond what the protocol could achieve on its own.
The Best VPN Protocol for Android and iPhone
- IKEv2
- WireGuard
Mobile VPN protocols require a different set of features than desktop ones. For one, the protocol must support Android and iOS, which not all of them do. Furthermore, it needs to be fast enough to not impede performance on high-speed 5G networks, and it must be able to switch networks seamlessly, which mobile VPN users often have to do.
All of these criteria narrow the choices down to IKEv2 and WireGuard as the top picks for mobile. We’ll point out that WireGuard is likely the best VPN protocol for Android, since it accesses the Android kernel directly, but the title of the best VPN protocol for iPhone could go either way.
The 3 Types of VPNs
There are three types of VPNs depending on their uses:
- Remote access VPN: This type of VPN allows individual users to securely connect to a private network from a remote location over the internet. Remote access VPNs are commonly used by employees who work from home or travel, providing them with secure access to company resources while away from the office.
- Site-to-site VPN: A site-to-site VPN is used to connect two or more separate networks — like branch offices, collaborators, clients or data centers — via the internet. This type of VPN creates a secure tunnel between the different sites, allowing all connected networks to share the same resources.
- VPN apps: VPN applications are designed for individual users who want to secure their internet connection and protect their online privacy. These VPNs typically provide remote access to their own VPN server network, which is in turn connected to the internet. They act as a middleman between the VPN user and the internet at large.
Final Thoughts
Choosing the right VPN protocol is crucial for ensuring the security and performance of your VPN connection. While OpenVPN and WireGuard are widely viewed as the most secure and efficient options, your ideal choice will depend on your specific use case, needs and priorities.
It’s important to remember that even the most secure protocols can fail if not properly implemented or maintained. Always choose a reputable VPN provider that regularly updates its software and has a proven track record.
What are your thoughts on VPN protocols? Do you have a strong preference for one over the rest, or do you simply let the VPN app choose for you? Please let us know in the comments below, and as always, thank you for reading.
FAQ: Best VPN Protocols
The three VPN protocols you’ll run into most often are IKEv2, WireGuard and OpenVPN.
Yes, several VPN protocols are obsolete and only used for legacy applications due to security concerns or poor performance. Some examples of defunct protocols are PPTP, which has poor encryption, as well as L2TP/IPsec, which is still secure but is simply outperformed by more modern protocols.
The three types of VPN are remote access VPNs (connecting users to a remote server), site-to-site VPNs (connecting remote networks to each other) and commercial VPN apps (connecting a user to a network of VPN servers).
The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) are transport layer protocols that define how data is transmitted over a network. TCP guarantees reliable data delivery at the cost of speed, while UDP tolerates the loss of some data packets for the sake of providing a faster encrypted connection.


