What Is Social Engineering? Human Hacking in 2025
Social engineering is an odd term, but one that pops up more and more in the media. Oddly enough, it perfectly describes what it does: namely, manipulating people into giving up sensitive information. Let’s go over how it works.
Key Takeaways: Social Engineering
- Social engineering is pervasive and can be found in all kinds of forms. The more you try to define it, the harder it becomes to pin down. Think of it as a way to get information without anybody knowing about it and you’re probably well on your way to understanding what it is.
- Social engineering can affect both individuals or businesses, though the forms they’ll encounter will differ greatly.
- There’s no foolproof way to protect against social engineering: all you can do is remain alert and vigilant to minimize the chances of falling victim.
Social engineering is the new buzzword, it seems. Articles keep popping up about its dangers and how you need to keep yourself safe from the people behind it. Look again, though, and you’ll quickly realize that for one, it’s nothing all that new; for another, protection against it is a matter of common sense.
In this article, we’ll go over what social engineering is, its most common forms and how you can best protect yourself against it.
We’ll try and do so without being too sensationalist, though at the same time we want to make one thing clear: Social engineering is a real thing that could, if used by the wrong people, cause real damage to you and your business.
-
10/23/2023
Updated the article to include information about Surfshark’s social engineering cybersecurity course.
What Is Social Engineering?
Social engineering, also known as human hacking, is all about getting information. Human hackers use a burglar’s skills without stealing anything, they play confidence games without talking you out of your money, and they use computer hacking tools without attacking systems.
In short, social engineering is all about manipulation. The people who are good at it will talk their ways past a reception desk, pick the lock of an office when nobody is looking, and plant a keylogger on a computer to get their hands on a set of passwords.
The primary goal for most social engineers is to get information: login credentials, a credit card number, confidential files, the layout of an industrial plant, you name it.
The secondary goal is, of course, to make money, either by selling that information or — in the case of a bank account password or credit card information — using it themselves.
The other way they make money is by selling their social engineering skills as security consultants, testing the defenses of companies to make sure that they can stand up to a dedicated team of human hackers. We recommend this video of an interview with Jenny Radcliffe, who goes over some of the scenarios she has been a part of.
What Does Social Engineering Look Like?
Social engineering may not look like anything at all, the attacker can sometimes collect the data they need simply from watching your social media and other online activities. It could also involve fake emails and text messages that look real or even someone physically looking at your screen as you enter sensitive information.
The goal of social engineers is to gain access to sensitive or confidential information, and for that to happen they usually need to get into systems. Rather than attack them outright, though, they go after the weakest link, which is…well, it’s us. Humans can very easily be tricked into giving away what they shouldn’t.
Examples of Social Engineering
Real-world examples abound: People fall for phishing emails every day, even after we’ve known about this threat for over a decade. Another trick is to call an executive’s secretary and pretend to be an IT guy who needs the boss’ login info.
It doesn’t always work, but when it does, you got what you needed for the price of one phone call or a few emails. Not bad for a day’s work.
We have compiled some cybersecurity statistics if you’d like to know more about how often attacks happen and how bad they can get.
Aside from sweet talk, another example of social engineering is to guess at things. For example, back in 2005, the whole world knew Paris Hilton’s dog was named Tinkerbell. One enterprising hacker tried to access an online account of hers, likely gave the dog’s name as answer to a security question and presto, they were in.
Another example is the News of the World scandal, when “journalists” from one of Rupert Murdoch’s nasty little tabloids hacked into the voicemail systems of celebrities and other people in the news.
They were able to do this because pretty much nobody changes their default voicemail password when they get a new mobile phone. All they needed to do was try their luck and that was that.
Types of Social Engineering Techniques
Just looking at a few examples like the above, and you can probably guess that there is no real comprehensive overview of social engineering techniques. Even if there was, it would be outdated by the time this article goes to print. The only limit to ways to con people is the inventiveness of the con artist.
Phishing Attacks
The one you’ll most likely encounter as an individual — though it’s used often enough against companies — is some form of electronic social engineering, usually through the internet. The most common example, and one probably everybody has run into at some point, is phishing.
We have written up a full guide on what phishing is, but, in short, the aim is to impersonate somebody over email or text to get you to give up personal information or click on links to malicious websites.
The most effective form is called spear phishing, which is when hackers pretend to be a bank or another organization that you could reasonably accept would contact you, as it’s very targeted.
That said, there are plenty of other forms of phishing, most of which are hilariously amateurish — these are usually called spam phishing as they revolve around sending messages in bulk.

Though it may seem like something that’s easy to avoid, plenty of people still fall for it. This is indicated by the cost of phishing, which is enormous. Estimates vary, but number in the multiple millions, especially for companies. Read our online scams guide to learn how to dodge hackers’ attempts.
Account Access
Phishing isn’t the only way to get you to give up personal information — there are plenty of other ways to hack computer systems without actually hacking them. One example is the insipid and useless security questions some services still make you answer, but thankfully this stupid “precaution” is dying out.
We use quotes because security questions are nothing more than another way for the ill-intentioned to gain access to a personal account.
Since most security questions are broadly all the same (mother’s maiden name, high school, first pet, etc.), all a human hacker needs to do is visit their intended target’s social networking sites, where exactly this kind of personal data is advertised, and take it from there.
If you want an alternative way to secure your online accounts, you’re much better off using a password manager than relying on account retrieval through security questions.
Physical Breaches
Of course, what gives social engineering its glamor is what human hackers get up to away from their computers. Stories abound of the daring acts some “social engineers” pull off, no matter if they’re security consultants or actually have something malicious in mind.
Common social engineering tactics come in all kinds of flavors. There are basics like “shoulder surfing,” which is just looking over somebody’s shoulder when they’re at their computer or an ATM. There are also complicated operations straight out of a Hollywood blockbuster, involving fake decals on vans and a crew in disguise.
The goal, though, is always the same: access. It’s important to note that violence is not in the repertoire of most human hackers. The name of the game is stealth, getting what they need and getting out — even air-gapped computers aren’t immune to sophisticated social engineering attacks.
The most important tool, though, is human nature. Whether it is the fear of authority or an innate willingness to trust people, that’s what a good con artist can exploit. Add to that some basic rules of human behavior — like the fact that the likelihood of being stopped and asked who you are is a lot smaller if you walk with purpose — and their jobs are almost done for them.
How to Protect Yourself Against Social Engineering
Of course, the question isn’t only what social engineering is, it’s also about what you can do to protect yourself. The answer to that is both difficult and simple at the same time.
What makes it difficult is that human hacking can take any form, so there’s no single defense. What makes it simple is that it’s all about teaching yourself some new basic habits.
Don’t Be Too Quick to Trust
One of the common threads in all the above examples is that people were too quick to trust. Sure, there’s a chance that the guy on the phone is the new guy in IT, but maybe he’s not. That email could be from your bank, but when’s the last time they sent you one for this reason?
All it takes to thwart social engineering is some basic security awareness. That said, we don’t recommend you become some sort of paranoid maniac who distrusts everything; there’s plenty of them already on Facebook.
Instead, focus on things that are out of the ordinary. Did you know there was a new guy in IT? Are there always weird links in your bank’s emails?
By questioning things that don’t seem right, you can avoid a lot of unpleasantness, and it’s something many social engineers remark on. If people asked more questions, their jobs would be a lot harder. Social engineering relies on your acceptance of things at face value; if you don’t go along with that, that’s half the battle.
Place Your Faith in Security Measures
Another important thing to remember is that security protocols are there for a reason, and you should follow them. Call the main office to find out if plumbers are really needed in building four, wonder aloud why somebody isn’t wearing a security badge in the back office.
This is even more important when it comes to cybersecurity. There’s a reason that email went into the spam folder, nor should you ever continue after Google warns you about a site’s security.
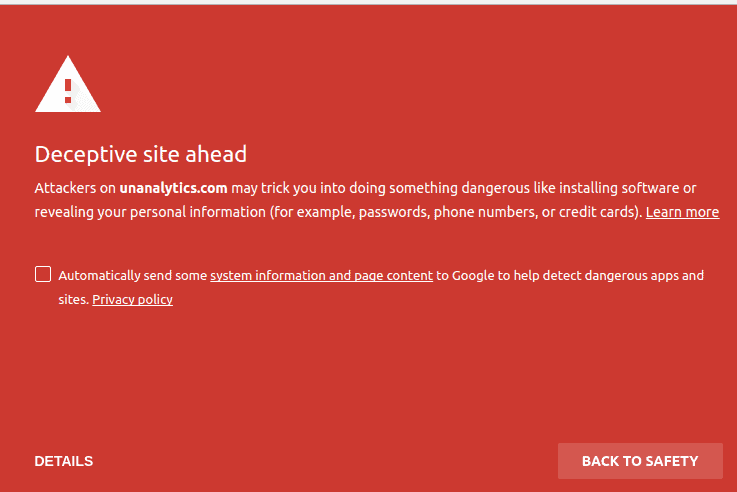
There are plenty of security measures in place to help you stay safe, so try not to be the smartest person in the room and simply follow procedure. It’s not much fun, but in cases like this it can really help you.
Think Twice
Our last tip is to use common sense and think twice before clicking links or sending anybody your personal or financial information — we have some other examples in our guide to staying safe on the web. Sure, maybe it is your son sending a cry for help via a new number, or maybe it’s a scammer; best to call his old number and find out what’s up.
When’s the last time your bank sent a text to warn you of a breach, and why are they asking you to click on a link? That doesn’t ring true, does it? The same goes for other coincidences, like most scenarios in heist movies: a boiler explodes and the plumbers are there straight away? That should make you suspicious, at the least.
Though it may seem like we’re blaming the victim a little with our above tips, the fact is that if you’re a nice, kind person, it becomes very easy for con artists or human hackers to take advantage of you. Instead, try to temper a willingness to help with some healthy skepticism, and you should be able to be a good person yet also remain safe.
Take a Course on Social Engineering
There are some security suites that take initiative in educating users in strong online safety etiquette. Surfshark is a great example — in 2023, it started offering a free social engineering cybersecurity course to help users spot and avoid scams.
Final Thoughts
Social engineering is just another way to take advantage of people. While it’s impossible to defend against it completely, some healthy skepticism and a hesitation to take things at face value should protect you from the worst of it.
Have you had experiences with social engineering? How was it? Do you have any other tips to help protect ourselves? Let us know in the comments below and, as always, thank you for reading.

