Best VPN for Hackers: The Ethical Hacker’s Guide
Ethical hacking pros often go about their business in anonymity and bring their activity to light only when they find a vulnerability. As a student of the game, it might be difficult to remain completely anonymous, but the best VPN for hackers can help. Read on to find the best hacker VPN.
Ethical hackers mimic malicious hackers to test the security of an organization’s system or application. However, doing this without approval can get you into trouble; you could even end up in jail. It’s better to stay anonymous until you achieve your goal, and the best VPN for hackers can help you in that regard.
Even if you have hacking approval, you’re not immune from online dangers. Malicious hackers could penetrate your device if you access the internet directly. A VPN provides the security and privacy you need to keep online threats at bay. This guide will reveal the five top VPN services for hackers.
-
11/02/2023
Updated the article to reflect ExpressVPN’s expansion of server presence from 94 to 105 countries.
-
10/01/2024 Facts checked
We updated the VPN list to incorporate the latest user feedback and expert evaluations.
-
03/12/2025 Facts checked
We updated this article with more details on NordVPN as well as what to look for in a VPN for hackers.
-
06/05/2025 Facts checked
This article was updated with more information about Surfshark’s features and ethical hackers’ use of VPNs.
-
09/04/2025 Facts checked
We expanded our coverage of ExpressVPN and added more details about features to look for in a VPN for ethical hacking.
-
11/27/2025 Facts checked
We added more information our CyberGhost coverage and restructured the section on what to look for in a VPN for ethical hacking.
Top Hacking VPNs
- 1
- : PayPal, Credit card, Google Pay, JCB, UnionPay, Bitcoin, Ethereum, X-Coin
- : 10
- :
- :
- :
- :
Average speedDownload Speed289 MbpsUpload Speed48 MbpsLatency6 ms - 2
- : PayPal, Credit card, Google Pay, Amazon Pay
- : Unlimited
- :
- :
- :
- :
Average speedDownload Speed289 MbpsUpload Speed48 MbpsLatency5 ms - 3
- : PayPal, Credit card, Bitcoin, UnionPay, iDeal, Sofort, Giropay, Pixpay, Sepa Direct Debit
- : 14
- :
- :
- :
- :
Average speedDownload Speed289 MbpsUpload Speed48 MbpsLatency7 ms - 4
- : PayPal, Credit card, bitcoin, Amazon Pay
- : 7
- :
- :
- :
- :
Average speed - 5
- : PayPal, Credit card, Amazon, Paygarden, Apple Pay, Google Pay
- : Unlimited
- :
- :
- :
- :
Average speedDownload Speed263 MbpsUpload Speed46 MbpsLatency8 ms
Do Hackers Use a VPN?
Yes, hackers use VPNs to keep their identities hidden and bypass firewalls. If you’re engaging in ethical hacking without proper approval, the organization you’re looking to help could misinterpret your intentions if they catch you in the act.
A good virtual private network should hide your real identity and prevent anyone from tracing any activity back to you. Security-conscious hackers should prioritize VPNs with no-logs policies that have been independently verified through third-party audits, providing assurance that their activities truly aren’t being recorded.
Protect Your Privacy. Get Our Free VPN Guide Now!

- Comprehend the essential role a VPN plays in safeguarding your digital life
- Gain a deep understanding of how VPNs function under the hood
- Develop the ability to distinguish fact from fiction in VPN promotions
However, ethical hackers should also consider VPN providers based outside the Five Eyes, Nine Eyes and 14 Eyes intelligence alliances, as these jurisdictions have agreements to share surveillance data, potentially compromising anonymity.
For ethical hackers operating in restrictive environments, VPNs provide essential internet censorship circumvention capabilities, allowing access to security resources and tools that might otherwise be blocked.
Security researchers accessing vulnerability databases like MITRE’s CVE repository from restricted regions often require VPNs that can bypass geolocation barriers while maintaining consistent access credentials for contributing discoveries.
In addition, during open-source intelligence (OSINT) gathering phases, ethical hackers require VPNs that support browser fingerprint randomization to prevent target systems from correlating reconnaissance activities across multiple information sources.
Ethical hackers participating in threat intelligence-sharing communities also use VPNs to securely submit indicators of compromise without revealing their organization’s security infrastructure or potentially exposing their networks to retaliatory attacks.
When following responsible disclosure protocols after discovering vulnerabilities, ethical hackers rely on VPNs with consistent jurisdiction policies to protect their identities during the sometimes contentious period between initial reporting and public acknowledgment.
In addition, some ethical hackers conduct security assessments on healthcare systems, which means they must maintain HIPAA compliance during testing. Thus, a VPN with detailed audit logs and role-based access controls is essential for documenting the scope and methods used.
Some also conduct security assessments on systems containing EU citizen data, so they must adhere to GDPR requirements. Any VPN they use must comply with strict data minimization capabilities and processing records to demonstrate compliance with Article 32 security measures.
Government contractors performing authorized security testing on classified systems must select VPNs that meet specific security clearance requirements, including FIPS 140-2 validation and adherence to Committee on National Security Systems (CNSS) directives.
Ethical hackers also benefit from VPNs offering split DNS configuration that allows simultaneous access to internal target network resources while maintaining secure lookups for external command and control tooling.
For automation-focused security testing, some VPNs offer API access that enables ethical hackers to programmatically control VPN connections, enabling integration with custom security-testing frameworks and dynamic IP rotation during extended scanning operations.
Some ethical hackers prefer command-line tools. Certain VPNs offer command-line interface (CLI) options alongside their graphical user interface (GUI) applications. This allows for VPN integration into custom scripts and automated testing workflows, enabling security professionals to incorporate VPN protection into their broader security assessment toolchains without manual intervention.
Advanced ethical hackers increasingly leverage containerized VPN deployments using Docker to create isolated, disposable testing environments that prevent cross-contamination between different security assessment projects. This approach allows for greater flexibility in testing various security scenarios while maintaining isolation from your main system, reducing the risk of unintended consequences during penetration testing.
Ethical hackers must also be vigilant about connecting to public networks, as malicious WiFi hotspots (known as evil twins) could be specifically targeting security professionals. A reliable VPN encrypts your data before it leaves your device, protecting your sensitive assessment data and tools even if you inadvertently connect to a rogue network controlled by an adversary.
For maximum security, ethical hackers should choose VPNs using AES-256-GCM encryption, which provides both data encryption and authentication, making it more secure than older AES-CBC implementations.
Read on to learn more about what to look for in a VPN for hacking.
What Makes the Best VPN for Hacking?
Security
You need one of the most secure VPNs with solid VPN protocol and encryption standards to send your traffic via an encrypted tunnel for a more anonymous experience. Learn more in our guide, “Does a VPN Protect You From Hackers?“
The VPN should also offer a kill switch and complete protection against WebRTC, IP and DNS leaks. This prevents accidental leaks that could reveal your identity and location. WebRTC leaks pose a significant risk to ethical hackers because this browser-based communication protocol can bypass VPN tunnels and expose your real IP address to websites you’re analyzing.
Advanced VPNs offer different kill switch modes — some block the internet only while the VPN is active but disconnects, whereas others completely prevent connections unless the VPN is running, providing stronger protection for ethical hackers. The latter “always-on” approach is valuable during extended penetration testing sessions where maintaining anonymity is mission-critical and even momentary connection leaks could compromise an assessment.
The VPN should also come with a robust network of servers — ideally including multi-hop servers — to help you mask your real IP address and make it difficult for anyone to know your true location.
Other vulnerabilities exist for ethical hackers, including DNS poisoning. In these attacks, threat actors can redirect your DNS requests to malicious sites. VPNs with custom DNS settings enable ethical hackers to use privacy-focused DNS resolvers or their own DNS servers for additional security during security assessments.
Quality VPNs encrypt your DNS requests and often handle them through their own secure DNS servers, preventing attackers from hijacking your connections or monitoring your reconnaissance activities.
Leading VPNs for ethical hackers also integrate custom DNS leak-testing tools that continuously monitor your connection for subtle DNS leaks specific to different operating systems and network configurations, identifying vulnerabilities that generic testing websites miss.
Operational Needs
Ethical hackers often utilize dedicated penetration testing labs like Hack The Box or TryHackMe, requiring secure connections when practicing techniques that mimic real-world attack scenarios without exposing their actual IP addresses.
Top VPN providers often maintain bug bounty programs, encouraging security researchers to identify and report vulnerabilities, which indicate a provider’s commitment to continuous security improvement. Ethical hackers participating in these programs must carefully select VPNs that comply with platform-specific requirements, as some programs explicitly prohibit certain VPN providers or require disclosure of VPN usage before testing begins.
When participating in bug bounty programs on platforms like HackerOne or Bugcrowd, ethical hackers require VPNs that support consistent IP addresses for program admission and accurate vulnerability reporting to prevent attribution conflicts.
For security assessments of critical infrastructure, ethical hackers often require VPNs capable of functioning within air-gapped testing environments where standard internet connections are deliberately unavailable and specialized configuration options become essential.
In addition, when assessing air-gapped networks, security professionals need VPNs that can rapidly switch between segmented network environments without credential reuse or authentication leakage that could compromise test isolation.
Advanced ethical hackers also leverage VPNs with specialized testing environments that simulate adversarial network conditions, allowing them to evaluate how security implementations perform under packet loss, latency spikes and intermittent connectivity that mimics real-world attack scenarios.
Advanced Features
When working in environments with unstable network connections, ethical hackers should consider VPNs that offer dynamic MTU (maximum transmission unit) adjustment capabilities.
This feature, found in protocols like ExpressVPN’s Lightway, automatically optimizes packet sizes based on network conditions, helping maintain stable connections during security assessments even on unreliable networks, which is crucial when working with remote systems in challenging network environments.
Some enterprise-focused VPNs now offer Trusted Platform Module (TPM) integration, securing encryption keys at the hardware level and providing ethical hackers with additional protection against key extraction attacks when operating from potentially compromised systems.
Others offer Hardware Security Module (HSM) integration, which stores cryptographic keys in specialized tamper-resistant hardware and provides assurance that even if the VPN server is compromised, the keys remain protected.
For ethical hackers working across multiple operating systems, unified cross-platform key management ensures consistent encryption implementation across Windows, Linux, macOS and mobile testing environments, preventing potential security degradation when switching devices.
Ethical hackers should select VPNs with strong protection against traffic correlation attacks as well, where adversaries analyze traffic patterns at both entry and exit points of a VPN connection to potentially deanonymize users, particularly when conducting security assessments against sophisticated targets.
Advanced ethical hackers should also prioritize VPNs implementing certificate pinning, which prevents sophisticated man-in-the-middle attacks by validating server certificates against pre-stored certificate authorities rather than relying solely on the device’s trusted CA store.
Several top VPNs for ethical hackers now implement hardened elliptic curve cryptography with custom parameters that resist the specific weaknesses identified in standard NIST curves potentially compromised by intelligence agencies.
Some VPNs also support port forwarding, which can be useful for ethical hackers who need to create incoming connections to their device while maintaining VPN protection, though this feature should be used carefully, as it can reduce anonymity.
When conducting authorized penetration tests that require receiving inbound connections, such as when setting up honeypots or testing client-server applications, a VPN with configurable port forwarding capabilities provides the necessary flexibility while maintaining core privacy protections.
Stealth or obfuscated protocols are also useful, as they disguise VPN traffic as regular HTTPS traffic. This helps ethical hackers bypass deep packet inspection and VPN blocks that organizations deploy during security assessments. When conducting authorized penetration tests against networks with advanced security monitoring, obfuscation capabilities ensure your testing activities aren’t prematurely detected by perimeter security tools, allowing for more thorough security evaluations.
Dynamic obfuscation rotation is another useful feature, automatically cycling through different obfuscation methods every few minutes, preventing pattern recognition systems from identifying and blocking VPN traffic during extended penetration testing sessions.
For ethical hackers using virtualized cyber ranges for training, certain VPNs offer specialized integrations that maintain security while allowing controlled traffic manipulation necessary for simulating complex attack scenarios.
Look for VPNs designed for penetration testing that implement multi-protocol tunneling fallbacks that automatically switch between OpenVPN, WireGuard and proprietary protocols when connections are actively being disrupted or filtered.
In addition, the ability to manually switch between TCP and UDP protocol implementations gives ethical hackers tactical advantages — TCP for reliable connections through restrictive firewalls and UDP for speed-critical testing scenarios where packet loss is acceptable.
Manual TCP packet fragmentation controls allow ethical hackers to optimize their connections when performing bandwidth-intensive security testing against intrusion prevention systems that analyze traffic at the packet level.
Privacy
Privacy tools such as RAM-only servers (diskless servers) come in handy, as they ensure your browsing history is wiped from the servers to obscure your digital footprints. They offer superior security by leaving no persistent data for potential attackers or authorities to recover.
Beyond basic RAM-only servers, advanced VPNs now implement RAM-disk forensic resistance that specifically prevents cold-boot attacks, where attackers physically freeze RAM chips to preserve data after power loss.
Ethical hackers should also consider services that offer additional privacy tools to minimize their digital footprint. Some providers include features that help remove your personal information from data broker archives, which can be crucial for maintaining anonymity during security assessments and preventing social engineering attacks based on your personal data.
A strict no-logs policy is important as well, as it means the VPN provider has no data or user logs to share even when coerced by government agencies.
In addition, look for VPN services that maintain a warrant canary — a statement that is regularly updated to indirectly inform users if the provider has been served with a government subpoena or warrant for user data.
When evaluating a VPN’s warrant canary system, ethical hackers should verify the digital signatures using PGP and monitor update frequency, as irregular or missed updates could indicate government interference without explicit notification.
Beyond basic warrant canaries, advanced ethical hacking VPNs implement cryptographically verifiable canary warrant systems that provide mathematical proof of when the statement was generated, making it impossible for authorities to backdate compliance notices.
Trustworthy VPN providers also publish regular transparency reports detailing government requests for user information and how they’ve responded, offering ethical hackers insight into the provider’s commitment to protecting user privacy.
As a final note, for ethical hackers, securing the VPN account itself is as important as the protection it provides. Look for VPN providers that offer two-factor authentication (2FA) for your account login, preferably using authenticator apps rather than SMS, to prevent unauthorized access to your VPN credentials during security assessments.
The 5 Best VPNs for Hackers
We selected the best VPNs for penetration testers and vulnerability assessors. The VPN providers have the features you need to enhance your anonymity online but offer different bells and whistles to sweeten the deal. We’ll discuss these details and pricing, starting with our best hacking VPN, NordVPN.
1. NordVPN – Best VPN for Hacking
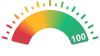
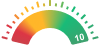

Very Fast
NordVPN is the best VPN for hackers, with a large server network comprising more than 5,000 RAM-only servers in 60 countries. Its fleet of servers includes obfuscated servers, which hide the fact that you’re using a VPN, allowing you to use the service in restrictive countries.
Moreover, its double VPN servers send your traffic through two servers, making it even more difficult for anyone to track you — and if one of the servers fails or becomes compromised, the other one will still protect your anonymity.
NordVPN also offers advanced split tunneling customization, allowing ethical hackers to route specific tools and applications through the VPN while maintaining direct connections for other traffic.
NordVPN provides experimental support for Multipath TCP as well, which enables users to simultaneously utilize multiple network paths (such as WiFi and cellular). This creates resilient connections that maintain stability during security assessments even when individual network interfaces experience disruptions.
What’s more, NordVPN uses a custom implementation of the WireGuard VPN protocol (called NordLynx) with ChaCha20 encryption, plus a more typical combination of OpenVPN with AES-256.
The provider also recently introduced the NordWhisper protocol, which is specifically designed to bypass VPN restrictions. Unlike traditional VPN protocols, NordWhisper doesn’t have distinct traffic signatures that reveal it as a VPN connection, making it valuable for ethical hackers working in restrictive environments.
This VPN has an array of security features, from solid encryption and VPN protocols to kill switch and DNS leak protection. It has streamlined its custom DNS feature, giving ethical hackers more control over their DNS resolution. This allows for more precise configuration when conducting domain-related tests or when specific DNS settings are required for particular assessment environments.
NordVPN’s Onion over VPN feature provides ethical hackers with enhanced operational security when conducting legitimate threat intelligence gathering on dark web forums by routing traffic through the Tor network. The additional encryption layer prevents Tor entry nodes from seeing your actual IP address.
The VPN also includes a “dark web monitor,” a tool that alerts ethical hackers if their credentials appear in data breaches — an important security layer for those accessing sensitive systems.
In addition, the Threat Protection Pro feature now includes vulnerability detection that regularly checks your installed applications against a database of known vulnerabilities. This proactive security feature alerts ethical hackers to potential weaknesses in their toolset before malicious actors can exploit them.
The “local network discovery” setting lets ethical hackers maintain access to their local network devices while connected to the VPN. The option to keep devices invisible prevents potential VPN traffic leaks caused by operating system limitations. This allows penetration testers to utilize local tools and devices during assessment activities without compromising their identity protection.
Last but not least, NordVPN offers post-quantum encryption capability, strengthening protection against future threats from quantum computing. This forward-thinking security measure ensures ethical hackers’ connections remain secure even as computational technologies advance.
NordVPN’s implementation of quantum-resistant tunnels goes beyond basic post-quantum cryptography by combining multiple candidate algorithms from the NIST Post-Quantum Cryptography standardization process, creating a hybrid approach that remains secure even if individual algorithms are broken.
NordVPN’s only red mark is that the VPN updated its privacy policy in early 2022 to comply with legal requests from foreign law enforcement agencies. That said, with RAM-based servers and a no-logging policy, there’s not much it can reveal about its users.
Stop Malware Attacks With Threat Protection
As we mentioned earlier, being an ethical hacker doesn’t make you immune to other online dangers. NordVPN’s threat protection feature blocks malicious sites and web trackers, which could thwart schemes hackers could unleash on your network or device — from social engineering to DDoS attacks.
Ethical hackers can leverage NordVPN’s enhanced Meshnet feature to securely share files of any size directly between devices through encrypted connections. Unlike cloud services, files transfer directly between endpoints with no server storage, maintaining maximum privacy when sharing sensitive findings or tools.
NordVPN’s monthly plan is a bit expensive, but the two-year plan is the best deal. In fact, we think that NordVPN is the best cheap VPN. Like ExpressVPN, it supports anonymous payment via cryptocurrencies, as well as a 30-day money-back guarantee. You can read more about it in our NordVPN review.
- **VAT may apply
- Unlimited GB
- 10
- Yes
- *The prices are charged in the first billing cycle only. Renewal prices vary.
- Unlimited GB
- 10
- Yes
- *The prices are shown only apply for the first 12 months.
- Unlimited GB
- 10
- Yes
- **The prices are applicable only for the first 24 months. Secure, high-speed VPN Threat Protection Pro™: Anti-malware and advanced browsing protection Threat Protection Pro™: Ad and tracker blocker Password manager with Data Breach Scanner 1 TB of encrypted cloud storage Identity and SSN monitoring and alerts Credit monitoring services Up to $1M in identity theft insurance Up to $100K in cyber extortion insurance
- 10
2. Surfshark – Most Affordable VPN for Hackers




Very Fast
Like our first pick, Surfshark boasts a collection of robust security features — from VPN protocols and encryption to a kill switch and DNS leak protection. You also get more than 3,200 RAM-based servers in 95 countries, including specialty MultiHop servers (a version of double VPN).
Surfshark has upgraded its entire server network to 10 Gbps capacity, providing faster connections and enhanced stability. For ethical hackers performing bandwidth-intensive activities like large dataset transfers or running multiple concurrent penetration testing tools, this infrastructure upgrade ensures more consistent performance even on crowded servers.
Surfshark also offers custom DNS servers that enhance both privacy and connection speeds. Unlike typical DNS servers operated by ISPs that may log user activity, Surfshark’s DNS servers maintain a strict no-logs policy and support DNS request encryption to prevent DNS leaks.
The provider has also significantly expanded its “dedicated IP” service to 20 locations globally, including specialized servers in technology hubs like Las Vegas, New York, Singapore and Istanbul.
For ethical hackers requiring consistent access to specific targets without triggering security alerts from changing IPs, this expanded network provides more geographically diverse options for maintaining persistent, legitimate-appearing connections.
In addition, “alternative number” is now available as an upgrade to the “alternative ID” feature, allowing users to maintain a separate phone number for verification processes and online communications.
For ethical hackers conducting social engineering assessments or needing to register accounts without exposing their personal information, this provides an additional layer of operational security when phone verification is required.
Surfshark also uses obfuscation technology (“camouflage mode”), though it works only with the OpenVPN protocol. Surfshark’s IP rotator feature has also been enhanced to provide more frequent and seamless IP address changes during a single VPN session.
The “bypasser” (split tunneling) feature is now available across all major platforms, including macOS. This allows users to route specific websites or applications outside the VPN tunnel while maintaining encryption for sensitive traffic, and is particularly useful when certain pentesting tools require direct connections while maintaining anonymity for other operations.
What’s more, Surfshark offers a malware and ad blocker called CleanWeb to keep you protected from other hackers. Surfshark encrypts your traffic using the industry standard AES-256 cipher, and it uses only the most secure protocols available: OpenVPN, WireGuard and IKEv2.
Surfshark has also implemented ephemeral key generation, which creates unique session keys for each connection. This ensures that even if one testing session is compromised, the encryption keys from previous or future security assessment sessions remain protected.
The provider has introduced “web protection” as well, which proactively alerts users when attempting to access potentially malicious websites. This feature provides ethical hackers with an additional security layer when researching potential threats or analyzing suspicious domains, helping to prevent accidental infection of systems used for security assessments.
A free data leak checker is also now available, powered by the Alert system, which allows users to verify whether their credentials have been compromised in data breaches or malware attacks.
This tool enables ethical hackers to quickly assess whether target organizations have experienced security incidents that may have exposed employee credentials, potentially providing legitimate entry points for authorized penetration testing.
For security researchers operating in restrictive environments, Surfshark offers an “emergency VPN” program that provides free VPN access to journalists, NGO workers and activists facing internet censorship.
This initiative distributed more than 300 accounts to those in need during the past year, demonstrating Surfshark’s commitment to internet freedom and potentially benefiting ethical hackers working on projects with humanitarian impact.
Hack Anonymously From Anywhere
If you’re in a restrictive country, you might be interested in Surfshark’s NoBorders mode. The feature, which is enabled by default, detects network restrictions and gives you a list of servers configured to bypass them. This way, not even China’s Great Firewall will be able to stop you.
Surfshark is affordable on extended plans, with the two-year plan offering the best value for the money. Each plan offers a 30-day money-back guarantee and supports unlimited simultaneous connections. Read our comprehensive Surfshark review to learn more.
- Unlimited GB bandwidth, Unlimited devices, Secure VPN, Ad blocker, Cookie pop-up blocker. Pricing for the annual and biennial plans only apply for the first payment. Renewal fees vary.
- Unlimited GB
- Unlimited
- Yes
- Everything in Starter, plus Antivirus protection, Identity protection, Email Breach and Credit Card Alerts, Online Alias Pricing for the annual and biennial plans only apply for the first payment. Renewal fees vary.
- Unlimited GB
- Unlimited
- Everything in One, plus Data removal Pricing for the annual and biennial plans only apply for the first payment. Renewal fees vary.
- Unlimited GB
- Unlimited
3. ExpressVPN – Easy-to-Use VPN for Hacking




Very Fast
ExpressVPN is another great VPN for ethical hackers. With more than 3,200 high-speed servers in 160 locations across 105 countries, it’s easy to find a nearby server to mask your IP address that still offers fast speeds. All the servers are obfuscated, which means it looks like you’re not even using a VPN.
In addition to having a strict no-logs policy, the VPN’s servers are RAM-based, meaning they wipe your browsing history after every reboot, leaving no trace of your online activities.
ExpressVPN boasts secure protocols: the industry-standard OpenVPN and its proprietary Lightway protocol. The protocols work in unison with AES 256-bit encryption to ensure your traffic passes through an impregnable encrypted tunnel.
The VPN has implemented DTLS 1.3 support for Lightway, delivering faster and more secure connection experiences. A “dynamic MTU” feature is also available, which automatically adapts to the connection’s path MTU. This ensures seamless connectivity over varied network environments.
ExpressVPN has also added post-quantum cryptography in the form of Kyber to support Lightway, providing enhanced protection against future quantum computer attacks. This forward-looking security measure ensures connections remain secure even as computational technologies advance.
ExpressVPN now offers enhanced split tunneling with advanced customization options, allowing users to route specific tools and applications through the VPN while maintaining direct connections for other traffic.
What’s more, ExpressVPN offers WebRTC, IP and DNS leak protection to prevent catastrophic leaks that could blow your cover. The kill switch stops internet traffic when the VPN connection drops to keep your veil intact.
ExpressVPN’s Android app now supports adaptive icons, allowing the app icon to adapt to your device, theme or launcher. This improved integration with Android’s UI makes the VPN less conspicuous when conducting security assessments on mobile devices. Dark mode is now available across all mobile applications as well.
A command line interface (CLI) is now available for Windows, allowing users to control the VPN through the Windows Command Prompt. This provides greater flexibility for automation and scripting.
ExpressVPN also provides a full graphical user interface for Linux, with built-in split tunneling support. This allows route-specific apps or traffic to tunnel through the VPN while others remain on the regular internet. It supports IPv4, IPv6 and subnet-based rules, which is especially valuable for Linux-based security testing.
The Security Benefits of Perfect Forward Secrecy
If an organization notices a hacking infiltration and decides to read your internet traffic to trace the intruder, perfect forward secrecy (PFS) will be your first line of defense.
With PFS, your data encryption keys change regularly, meaning that even if the organization gets one key, they can’t decrypt the entirety of the web traffic to reveal your IP address or identity.
Perfect forward secrecy is an essential security feature for ethical hackers that ensures encryption keys change regularly during sessions. This means that even if one encryption key is compromised during a security assessment, the attacker can’t decrypt your entire traffic history to reveal your methodologies, tools or findings from previous sessions.
connection by an insignificant degree.
The only downside with this VPN is that ExpressVPN is quite expensive, though you can buy the two-year plan to get a discount, and you can test it out with its 30-day money-back guarantee. ExpressVPN even lets you pay with Bitcoin for additional online anonymity. Read our full ExpressVPN review to learn more.
- Pricing for the annual and biennial plans applies only on the first year.
- Unlimited GB
- 10
- Yes
- Advanced Protection, ExpressVPN Keys, 3 days unlimited eSIM data, Identity Monitoring, IDP Insurance, Credit Monitoring, 25-50% off on Aircove Router Pricing for the annual and biennial plans applies only on the first year.
- Unlimited GB
- 12
- Everything on the Advanced Plan, Credit Monthly Report, Data Removal, 50-75% off on Aircove Router Pricing for the annual and biennial plans applies only on the first year.
- Unlimited GB
- 14
4. CyberGhost – Hacking VPN With the Best Server Network
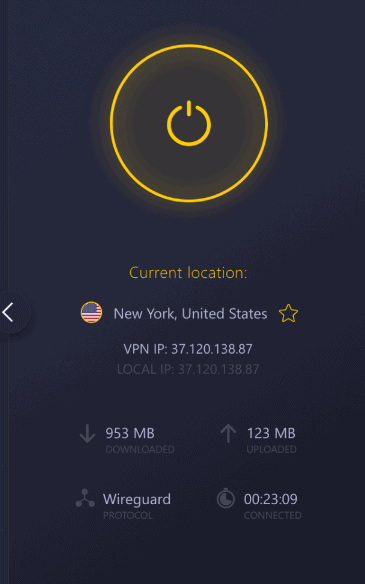



CyberGhost is an easy-to-use privacy juggernaut that’s up there with the best hacking VPNs. It has the biggest VPN server network on this list, with more than 8,000 servers in 91 countries.
The fleet includes NoSpy servers, which are privacy-centric VPN servers based in Romania (CyberGhost’s headquarters) that prevent government seizure or access by unauthorized individuals.
CyberGhost blocks DNS domains that are known to be malicious or used for advertising to protect you from falling prey to other hackers. Beyond that, CyberGhost uses safe VPN protocols, including WireGuard and OpenVPN in tandem with AES-256 encryption for the highest level of security. Plus, the WinTUN driver is used for all OpenVPN connections on Windows, delivering improved performance and stability.
CyberGhost has implemented certificate pinning for its domain as well, significantly enhancing security by preventing man-in-the-middle attacks that could compromise encrypted connections. This feature is crucial for ethical hackers who need to ensure their testing traffic remains private and secure.
In its latest updates, CyberGhost has implemented post-quantum cryptographic measures, preparing for a future where quantum computing could threaten traditional encryption. This security approach ensures ethical hackers’ communications remain protected against even the most advanced theoretical decryption capabilities.
The VPN has also implemented and continuously improved its Meta Proxy API technology, which helps users in restrictive countries bypass VPN blocks. This feature is particularly valuable for ethical hackers working in environments with sophisticated censorship systems.
The provider now offers a dedicated leak protection feature accessible through the settings menu. This enhancement provides ethical hackers with additional safeguards against IP, DNS and WebRTC leaks that could expose their true identity during security assessments.
The dedicated IP service is significantly enhanced as well, implementing features to inform users when users’ IP changes and improving connection reliability.
CyberGhost has also strengthened its security posture by disabling JavaScript in WebViews where it’s not needed, reducing the potential attack surface. For ethical hackers, this means enhanced protection against JavaScript-based exploits while using the application. Redirects in WebViews are now blocked as well, significantly reducing potential risks from malicious websites.
Always-On Protection With Smart Rules
The “smart rules” feature allows you to configure the VPN to establish a connection every time you open the apps you use during ethical hacking. Doing so ensures you always enjoy the best possible anonymity, and it comes in handy should you forget to switch on the VPN.
CyberGhost is affordable. Although the monthly plan is more pricey, it allows a 14-day money-back guarantee. You can get the best deals with its longer plans, which offer a 45-day money-back guarantee. Read our full CyberGhost review to learn more.
5. Private Internet Access – Best VPN Option for Linux-Using Hackers



Very Fast
Private Internet Access is a great VPN for hackers, and we recommend it if you use a Linux device. The Linux app comes with a graphical user interface, which makes it easy to set up and use PIA on all Linux distros.
Beyond that, the PIA virtual private network has the usual basic security features, including a kill switch that will cut off your internet connection if the VPN isn’t running.
PIA uses OpenVPN and WireGuard with AES-128 encryption, though you can increase the key size to 256 bits. PIA’s password security tooling goes beyond basic protection by actively checking if your credentials have appeared in known data breaches.
Additionally, it offers more than 30,000 VPN servers across 84 countries, which dwarfs the other VPNs on this list. There are no specialty servers, but all servers are RAM-based, meaning they expunge your browsing history to leave no trace of your online activity.
Block Malicious Websites With PIA MACE
PIA MACE blocks malicious websites and cross-site trackers, which could foil hackers’ attempts to infiltrate your device or network. MACE works in a way that’s faster than a normal ad blocker and it consumes less battery power on mobile.
hackers, but it gets the job done.
Private Internet Access VPN is affordable — especially the three-year plan. Each plan supports 10 simultaneous connections and offers a 30-day money-back guarantee. Read our Private Internet Access review to learn more.
Final Thoughts
The best VPNs for hackers mask your IP address, making it difficult for organizations to track your activity. Doing so helps you stay anonymous so you can go about your business with minimal chances of getting caught in the act. We recommend NordVPN, which you can try for yourself risk-free using the 30-day refund period.
However, there’s a major caveat: No VPN can make you 100% anonymous online. VPN services just bring you closer to total anonymity. If you intend to engage in ethical hacking without approval, we recommend using a VPN with Tor (see our best VPN for Tor guide).
Before trusting a VPN for sensitive ethical hacking activities, consider verifying its security claims using automated packet inspection tools like Wireshark. This allows you to confirm that the VPN properly encrypts all traffic and doesn’t leak your real IP address or DNS requests during critical security testing operations.
When selecting a VPN for ethical hacking, prioritize providers that subject themselves to regular independent security audits from reputable firms like Deloitte, KPMG or specialized cybersecurity auditors. These third-party verifications provide concrete evidence that the VPN’s security infrastructure and no-logs policies can be trusted for sensitive security testing work.
Have you used a VPN when performing a vulnerability assessment or penetration testing? Which VPN service did you use? What are the principal benefits of using a VPN during ethical hacking? As always, thanks for reading.
FAQ
Yes, ethical hackers use NordVPN for extra anonymity and protection online.
We don’t vouch for free VPN providers for hacking purposes, particularly when it comes to safeguarding user privacy and anonymity online. However, there are exceptions, such as Windscribe, which is a great option for hackers on a tight budget.


