17 AWS Security Tools, Software and Services for Cloud Security, Identity and Compliance
Will AWS security tools protect your cloud workloads? This guide highlights the use cases, features, pricing, benefits and downsides of 17 AWS security software tools.
AWS Security is a combination of practices and tools that ensure security of the cloud and in the cloud. AWS handles the physical security of the infrastructure as well as compute, networking, storage and database security. The customer, on the other hand, handles the security of their operations and workloads. This is where AWS security tools come into play.
With AWS Macie for machine learning-driven data protection, AWS IAM for access management and AWS Artifact for compliance documentation, AWS security tools can be quite comprehensive with proper implementation.
AWS security tools include AWS Identity and Access Management (IAM), Amazon GuardDuty, AWS Inspector, Amazon Cognito, IAM Analyzer, AWS CloudTrail, AWS CloudWatch, AWS Config, Amazon Detective, Amazon GuardDuty, AWS Elastic Disaster Recovery, Amazon Macie, AWS Secrets Manager, AWS Shield, AWS Web Application Firewall, AWS Artifact, AWS Audit Manager and AWS Security Hub. These tools and others are described below.
- Amazon Cognito: Amazon Cognito is a secure customer identity and access management service that developers can add to their applications.
- AWS Identity and Access Management (IAM): AWS IAM is a service for controlling access privilege.
- AWS IAM Analyzer: IAM Analyzer is an AWS security solution that monitors and reviews IAM policies.
- AWS CloudTrail: AWS CloudTrail is a security monitoring tool used to track API usage, audit operations and improve compliance.
- AWS CloudWatch: AWS CloudWatch monitors applications and resources, and then responds to performance changes.
- Amazon Inspector: Amazon Inspector conducts a nonstop scan of AWS resources, looking out for various cloud vulnerabilities and network exposure.
- AWS Config: AWS Config focuses on configuration assessment, auditing and evaluation in an AWS environment.
- Amazon Detective: Amazon Detective is security software primarily used for identifying the cause of system vulnerabilities and suspicious activity.
- Amazon GuardDuty: Amazon GuardDuty is an easy-to-configure, machine learning-driven threat detection service.
- AWS Security Hub: AWS Security Hub is a security tool that primarily collects, compiles and classifies security alerts.
- AWS Elastic Disaster Recovery: AWS Elastic Disaster Recovery helps recover applications and networks quickly when they fail.
- Amazon Macie: Amazon Macie is a machine learning security tool used to scan sensitive data in AWS workloads.
- AWS Secrets Manager: AWS Secrets Manager handles sensitive information like passwords and API keys.
- AWS Shield: AWS Shield is a managed service that protects against DDoS attacks.
- AWS Web Application Firewall: AWS Web Application Firewall is a security service tailored to protect web applications against exploits like SQL injection and malicious bots.
- AWS Artifact: AWS Artifact is one of the primary AWS compliance tools, it provides access to AWS and third-party security and compliance reports.
- AWS Audit Manager: AWS Audit Manager conducts a nonstop review of an account’s AWS usage, assessing risk and compliance. It’s one of two AWS cloud security solutions focused mainly on compliance.
1. AWS Identity and Access Management (IAM)
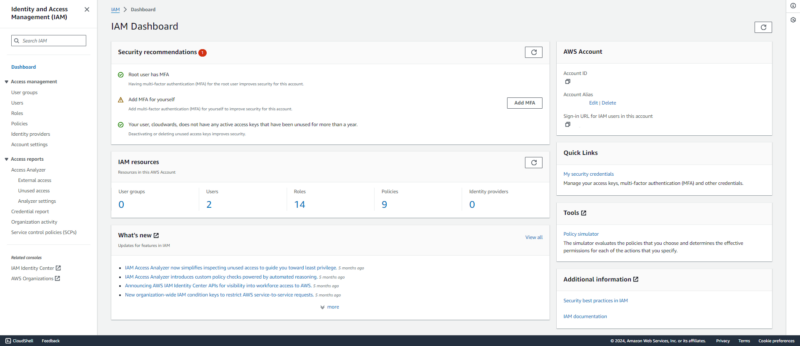
access management, access analysis and IAM documentation.
AWS Identity and Access Management (IAM) is an AWS security service that helps control access to services and resources in an AWS account or organization. AWS IAM controls who can access what — in other words, it’s a gatekeeper. Unsurprisingly, AWS IAM falls under the security category of identity access and management.
System administrators, cloud engineers, cybersecurity teams and business owners, among others, are the main IAM users. It comes at no extra charge.
2. Amazon GuardDuty
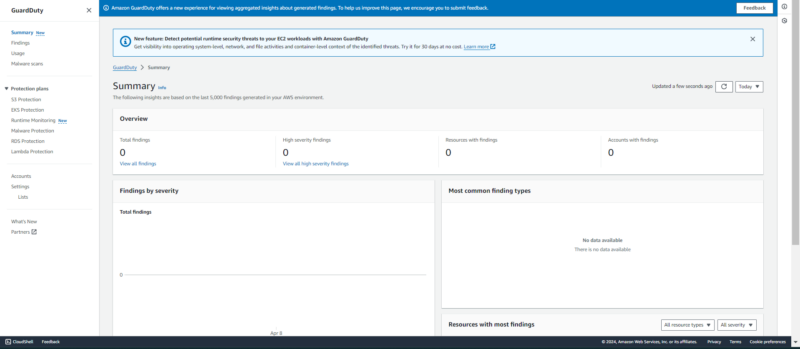
findings and available protection plans for AWS resources.
Amazon GuardDuty is a threat detection and response service. It continuously monitors events across AWS resources for malicious activity and calls attention to potential security risks. In other words, it is a security guard on a round-the-clock shift.
This service combines the power of machine learning algorithms and cybersecurity intel from various sources for threat detection. It’s a handy service for pretty much anyone using AWS, particularly security teams and businesses. The pricing depends on the volume of events.
3. Amazon Macie
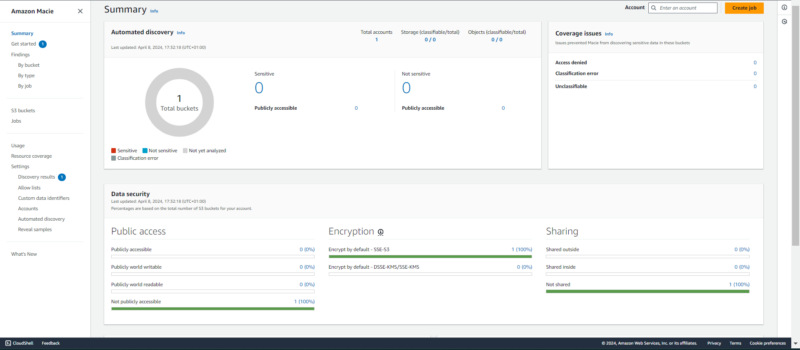
into the security of sensitive data in S3 buckets.
Amazon Macie is a data discovery and protection service. Using machine learning and pattern matching, it primarily monitors and evaluates Amazon S3 buckets for sensitive data and configuration vulnerabilities. It then shares its findings with remediation tools to automate resolutions.
This service is useful for organizations with large volumes of data that require compliance and extra security in S3 buckets. The pricing is based on the number of S3 buckets, the volume of data inspected and the number of objects monitored.
4. AWS Config
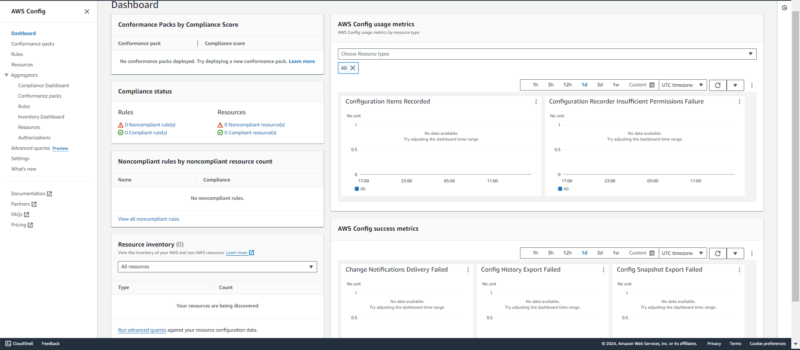
inventory and compliance status of resources.
AWS Config is a configuration monitoring and management tool and serves as a core part of the platform’s threat detection and response. It conducts an ongoing evaluation of the configuration of resources in an AWS environment, simplifying troubleshooting.
Security or compliance teams and organizations with complex AWS environments will benefit immensely from AWS Config. Config’s pricing is based on the number of configuration items, conformance pack evaluations and active rule evaluations required.
5. AWS CloudTrail
how the service works, as well as its features and benefits.
AWS CloudTrail compiles logs and records of API calls made to AWS, hybrid and multi-cloud environments. The captured records are immutable, ensuring compliance and auditability. The insight from analyzed records helps improve security as well as threat detection and response.
Compliance and security professionals, system administrators and software developers will find AWS CloudTrail highly beneficial. AWS CloudTrail is largely pay-per-use and pay-as-you-go, depending on the feature.
6. AWS Security Hub
the asset risk level and a regional summary of findings.
AWS Security Hub is a cloud posture management service that offers threat detection and response. It continuously monitors AWS resources, checking that they meet the preferred security standards. Then it collects records of its findings, investigates them, and starts remediation where necessary.
Security teams and ops teams in particular will find this AWS security tool valuable to their work. AWS Security Hub pricing is based on the number of checks, automation rule evaluations and ingestion events.
7. Amazon Inspector
environment’s posture, including findings, remediation and coverage.
Amazon Inspector is an automated vulnerability management service. It basically scans for security weaknesses in workloads such AWS Lambda functions and ECR container images. It also checks for unintentional network exposure.
Amazon Inspector is a detection and response tool that is great for sysadmins, security professionals and even developers. It comes with a 15-day free trial, and the paid version is primarily pay per use.
8. AWS Shield
activity, features and tier comparison on its “getting started” page.
AWS Shield is a managed DDoS protection service. It protects applications running on AWS from artificial traffic that can leave them inaccessible to legitimate users.
This service is a great solution for businesses and organizations of all sizes. AWS Shield is available in Standard and Advanced plans. Standard comes at no cost. Advanced is available for a monthly fee and a fee based on outgoing data transfer, and requires a one-year commitment.
9. AWS Web Application Firewall
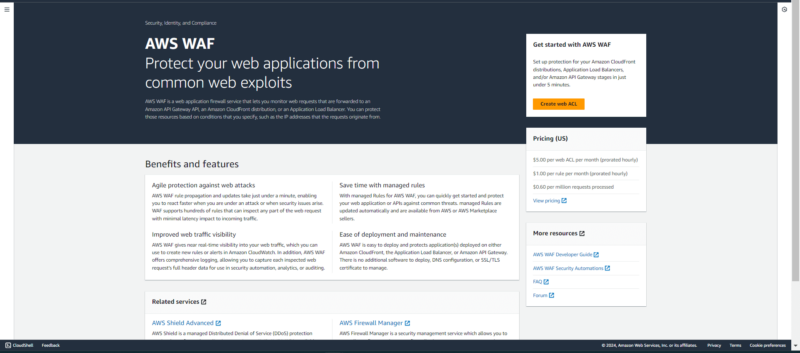
a summary of what to expect when using the service.
AWS Web Application Firewall (WAF) is a firewall service. It offers network protection by monitoring and controlling the traffic between a web application and the internet, blocking out potentially dangerous ingress.
This service is for anyone with a web application on AWS. It is particularly useful for security engineers, sysadmins and developers. AWS WAF pricing is based on the number of incoming requests, web access control lists (ACLs) and web ACL rules.
10. AWS Secrets Manager
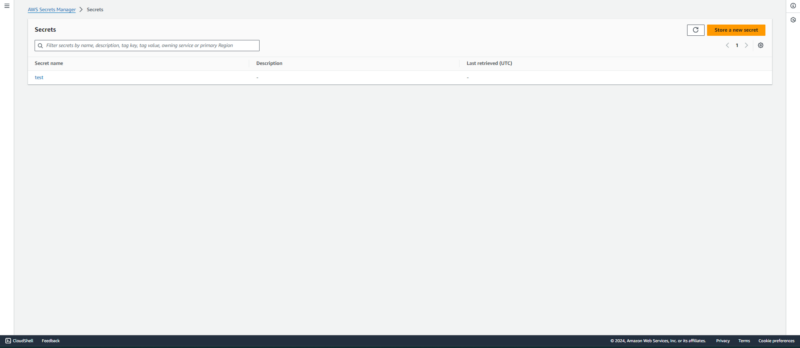
as well as a description and information about the last retrieval.
AWS Secrets Manager is a credential management service. It stores, retrieves and encrypts credentials, including passwords, API keys and tokens, thereby providing data protection. Beyond that, it can rotate credentials based on a defined schedule.
Secrets Manager will come in handy for ops teams, security teams and development teams. However, virtually anyone who uses AWS will find it useful. As with most security tools in AWS, Secrets Manager charges based on usage — in this case, the number of API calls and the monthly volume of secrets.
11. AWS CloudWatch
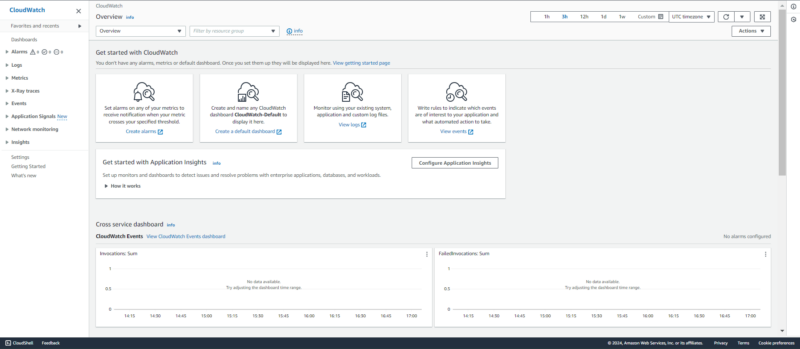
summaries of alarms, dashboards, events, logs and metrics.
AWS CloudWatch is an application performance monitoring tool. Like many other AWS security monitoring tools, it evaluates resources. More specifically, it collects, analyzes and visualizes data on application performance, network performance and resource usage. This allows for improved detection and response to potential issues.
Devops engineers, security engineers, sysadmins and developers will find a variety of uses for CloudWatch. It is a pay-per-use service; the total cost is determined by the volume/number of logs, metrics, events and dashboard, among others. However, there is a free tier.
12. AWS IAM Analyzer
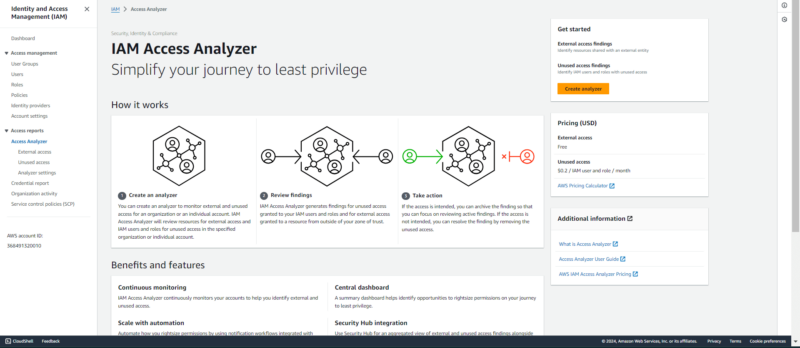
AWS IAM Analyzer is an AWS security product that evaluates and refines identity and access management (IAM) policies. Its goal is to ensure that IAM policies meet the least-privilege requirements. In simpler terms, it is the IAM watchdog.
IAM Analyzer is for cloud engineers, security or IAM specialists, and sysadmins. For the “unused access analyzer” feature, pricing depends on the number of IAM roles and users analyzed per month. The pricing for the “custom policy checks” feature is based on the number of API calls.
13. Amazon Cognito
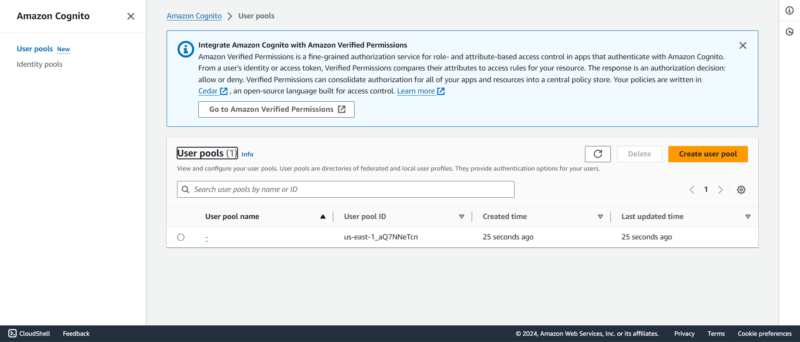
the ID, creation time and time of last update.
Amazon Cognito is a customer identity and access management service. Unlike AWS IAM, which manages identity access for users, groups and resources within an AWS organization or account, Cognito manages customer access to a product.
Cognito is perfect for software developers who want to integrate signups and logins, social logins or intricate access control. The user pool primarily determines the cost of AWS Cognito. Higher requests based on second quotas and Cognito Sync are also priced differently.
14. AWS Artifact
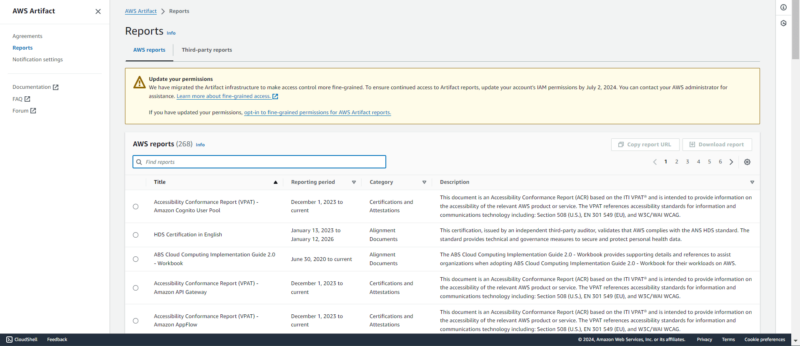
with the reporting period, a description and the category.
AWS Artifact is one of the two primary AWS compliance tools. It is a repository that streamlines access to compliance reports from AWS and third parties.
This is for security and compliance professionals, auditors and developers, among others. It is included in the AWS free tier.
15. Amazon Detective
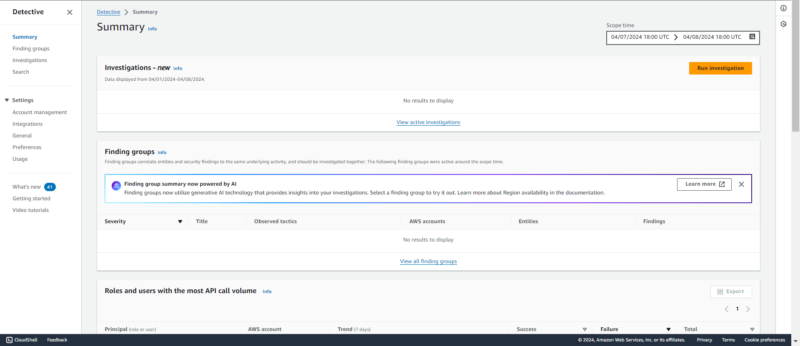
investigations, finding groups, API usage and more.
Amazon Detective is an investigation and visualization tool. It analyzes security data and provides visual insight into the analyzed data for quicker interpretation.
Cybersecurity experts and cloud engineers will find Amazon Detective useful. The tool comes with a 30-day free trial. The paid version is charged based on the volume of data ingested per account per region per month.
16. AWS Audit Manager
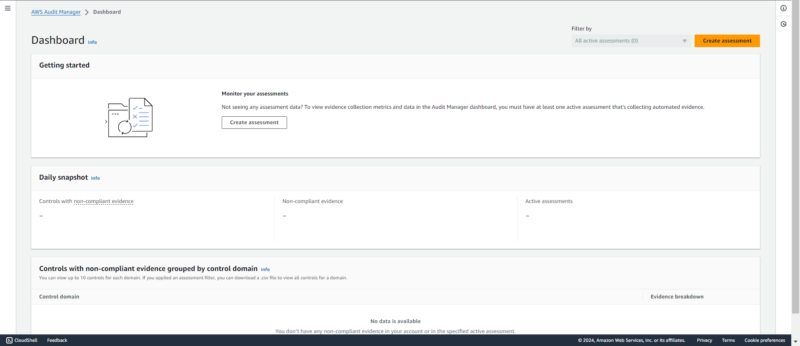
as it highlights assessments and evidence of non-compliance.
AWS Audit Manager is the second of the two primary AWS Compliance services. It carries out an ongoing assessment of AWS account usage, ensuring conformity with industry specifications.
Audit Manager is a great tool for auditors. However, security engineers and business managers will also find it valuable. The paid version of Audit Manager is charged based on the number of resource assessments per month.
17. AWS Elastic Disaster Recovery
quick walkthrough of the service’s features and usage.
AWS Elastic Disaster Recovery is a cloud disaster recovery service. It is the cavalry you send in when AWS-based applications fail, as it replicates and replaces them if they malfunction. When all the other detection and response tools fail, AWS Elastic Disaster Recovery performs damage control.
Elastic Disaster Recovery is a cost-effective disaster recovery tool for companies. It is also a great option for companies that cannot create their own disaster recovery systems. The pricing is based on the number of servers actively being replicated per hour.
What Are Some Third-Party AWS Security Tools?
Independent software vendors build third-party AWS security tools for use on AWS. However, unlike the typical AWS native tools, these third-party tools are usually also compatible with other cloud platforms.
Besides having a broader scope, third-party security tools are often more versatile. They sometimes offer more features than AWS native tools. However, they may fall short when it comes to ease of integration with AWS.
Some third-party security tools include:
- Prowler: An open-source auditing tool that helps improve cloud compliance.
- Astra Security: This is a platform from Astra IT Inc. that offers cybersecurity services such as penetration testing, vulnerability scanning and assisted remediation.
- Sumo Logic: A tool focused on analyzing logs and similar data to provide security insights.
- Trend Micro Cloud One: This tool from Trend Micro Inc. offers a suite of cloud security features, including identity and access management, and cloud account management.
What Is the Difference Between AWS Native Security and Third-Party Security Tools?
The primary difference between AWS native security and third-party security tools is their compatibility. AWS native security tools are built for easy integration with the AWS ecosystem. Outside AWS environments, integration may be almost impossible.
On the other hand, third-party security tools, which are built by independent software vendors, are compatible with various cloud platforms. Compared to AWS native security tools, they may not integrate as easily or deeply with AWS resources. However, integrating them shouldn’t be too difficult.
What Are the Factors to Consider Before Using AWS Security Tools?
Before using security tools on Amazon Web Services, assessing your current security posture and desired outcomes is essential. In other words, you have to know which tools you need to help reach your security goals.
Two crucial factors to consider before using AWS security tools are budget and expertise. The team needs someone skilled enough to use the tools. Of course, regulations are also vital to the decision to use a security service.
The existing infrastructure is also key when choosing an AWS security tool. You must consider compatibility and ease of use with the existing system.
Final Thoughts
Cloud security is an ongoing process, as security threats are always evolving. Though these AWS security tools strengthen security posture, staying informed about emerging threats and ensuring continuous evaluation is crucial to maintaining security.
Were you hoping to read about any AWS security tools and services that aren’t on this list? Will you be trying any of these tools soon? Let us know in the comments section. Thanks for reading.
FAQ: Security Tools and Services for AWS
AWS has an extensive set of security services across various categories, including AWS IAM, Amazon Macie, AWS Security Hub and Amazon Inspector.
A cloud security tool is an application or a service that helps prevent, detect, protect and respond to security threats in the cloud.
AWS currently has more than 200 tools.

