VeraCrypt Review
Probably one of the best known examples of open-source encryption software, VeraCrypt is a powerful program with more features than you can shake a stick at. That said, you need to know what you're doing when using it, as you can read in this full VeraCrypt review.
VeraCrypt is a free, open-source encryption application built by a team of two people: Mounir Idrassi, the main developer, and a volunteer developer. Although small in terms of scope — VeraCrypt is focused mainly on protecting local files — it’s surprisingly robust in terms of features. In this VeraCrypt review, we’re going to determine if it’s the right service for you.
The foundation of VeraCrypt is from TrueCrypt, another free, open-source encryption software utility that was discontinued in 2014. Idrassi used TrueCrypt’s source code, improving some aspects of security, to create VeraCrypt. In fact, it’s our top pick for the best TrueCrypt alternative services.
Although VeraCrypt isn’t the right product for most consumers, it’s still among the best encryption software choices. The options are second to none, allowing you to encrypt and store your files in any way you see fit. Additionally, VeraCrypt comes with a number of unique features we’ve never seen before. Read on to learn more about them.
Strengths and Weaknesses
Strengths:
- Whole-disk encryption
- Operating system encryption
- Multiple algorithm options
- Free
- Open-source
- Hidden volumes & operating systems
Weaknesses:
- Can be difficult to use
- Few support options
- No cloud storage integration
- No sharing options
Features
VeraCrypt has a lot of features, many of which may not be relevant to you. As we’ll see in the “ease of use” section below, VeraCrypt is all about options, allowing you to customize and secure your files in a number of different ways. There are also some security features that go beyond standard encryption.
Starting off, VeraCrypt works by creating volumes on your machine, which will show up as separate disks. You can create new volumes and drag files in, or you can encrypt existing partitions. One of the great things that separates VeraCrypt from its paid counterparts is its ability to encrypt entire disks, even where the OS is installed.
If you create a new volume, you’ll need to specify the size. That’s important to note, as the encrypted file won’t show the size of what’s on it. For example, if you create a 500GB volume but only have 200GB of data on it, the VeraCrypt file will still show 500GB of size when it’s unmounted.
Whole-system encryption adds an additional layer of security before your OS even loads. All of this happens locally, too, meaning you don’t need to have an internet connection or connect to VeraCrypt to authenticate.
VeraCrypt Rescue Disk
Unfortunately, system encryption could cause some issues. If there’s anything awry with the launcher, your machine won’t boot and you’ll be locked out completely. Thankfully, VeraCrypt has a failsafe in place.
When setting up a system partition or drive for encryption, you can create a rescue disk, which you can store on a CD/DVD or USB drive. For whatever reason, if the VeraCrypt Boot Loader is damaged or data relating to decryption is missing, your rescue disk can repair those issues and regain access.
You should create a rescue disk, but there are a number of disclaimers that come along with it. Make sure to read VeraCrypt’s writeup on the feature to ensure you’re protected.
VeraCrypt Hidden Volume and Operating System
VeraCrypt has a couple of features that relate to plausible deniability. For instance, if you have sensitive documents and you’re the victim of extortion, you may be forced to hand over your volume password, which would render the encryption useless. VeraCrypt has a couple of tricks for that exact scenario.
When creating a volume, you can specify a hidden volume. As mentioned, VeraCrypt will fill up any space in a volume that you’re not using with random data so it appears to be the size you specify. A hidden volume works in that free space. Essentially, you’ll create a volume within a volume.
The general process works like this: You create a standard volume and place some sensitive-looking information inside, which you don’t mind if someone finds. Behind that, you place the information you want to protect. You’ll set a password for each, and when mounting the volume, the entered password will determine which set of data is unlocked.
You can do the same thing with operating systems. The VeraCrypt Boot Loader can separate two OS installations into separate volumes. Once again, you’ll set a different password for each, and the password you enter will determine which OS is loaded.
VeraCrypt Features Overview
| Features | |
|---|---|
| Devices | Unlimited |
| File size limit | Unlimited |
| File extension restrictions | |
| Sharing | |
| Zero-knowledge | |
| Cloud storage integration | |
| Payment methods | Crypto, PayPal, wire transfer |
| Refund policy | |
| Knowledgebase | |
| User forum | |
| Live chat | |
| Phone support | |
| Email support | |
| 24/7 support | |
| Encryption | AES, Camellia, Kuznyechik, Serpent, Twofish |
| Sharing encryption | |
| Master password hashing | RIPEMD-160, SHA-256, SHA-512, Whirlpool, Streebog |
Pricing
As mentioned, VeraCrypt is a free, open-source project. There isn’t a paid plan available or any pestering to donate. You can download the application to Windows, macOS and Linux without paying a dime. Although that’s great, going free does pose some issues in other areas.
Namely, VeraCrypt doesn’t have the cloud storage integrations, which is one of its best potential uses. That said, VeraCrypt doesn’t seem to be aimed at those who are looking to sync encrypted files across cloud storage services. Rather, it’s much more focused on local encryption, scrambling the entire file system rather than just file data.
If you use VeraCrypt and decide you like it, you can always donate to the project. IDRIX, the team behind VeraCrypt, accepts donations via PayPal, bank transfer, bitcoin and other cryptocurrencies.
Security
VeraCrypt’s security is actually fairly simple. You don’t have to authenticate with a server to use your account, which gets rid of a huge hurdle most encryption software services face. Furthermore, there’s no direct sharing capability, so using key pairs to match up authorized users isn’t a concern.
The software is all local. By default, VeraCrypt uses AES-256 to encrypt the file system (read our description of encryption to learn more about that). That includes data, filenames and anything else related to the data you’re encrypting. Although AES is the default and recommended by VeraCrypt, there are other algorithms available, too.
Notable algorithms are Camellia, which was developed by Mitsubishi and NTT of Japan, and Kuznyechik, which was developed by the Russian Federation. Regardless, each algorithm has a 256-bit key size and 128-bit block size. You can also combine multiple algorithms. For example, VeraCrypt supports a AES-Twofish-Serpent mode.
When you create a password, VeraCrypt uses one of five hashing algorithms, generating pseudo-random keys based on a number of factors, including your mouse movements and keystrokes. A master key, secondary key and salt are generated from this process, which allows you to decrypt your data with a master password you recognize.
All of this happens fairly quickly, especially if you have an Intel CPU. VeraCrypt supports hardware-accelerated AES encryption, using the Intel AES-NI instructions. Although the speed difference hardly matters on modern, multicore processors, it can speed up the process on older machines.
Ease of Use
VeraCrypt’s website is about what you’d expect from open-source encryption software service, meaning it looks like it was developed by cryptography experts rather than website designers. The dated look isn’t easy on the eyes, but it’s still functional if you can differentiate the download versions. If you can’t, VeraCrypt probably isn’t for you.
There’s no account to create or information to enter. All you need to do is head to the “downloads” page, select the installer for your OS and get to encryptin’. You can also download the source code and SHA256/SHA512 checksums if you’re so inclined.
VeraCrypt Portable
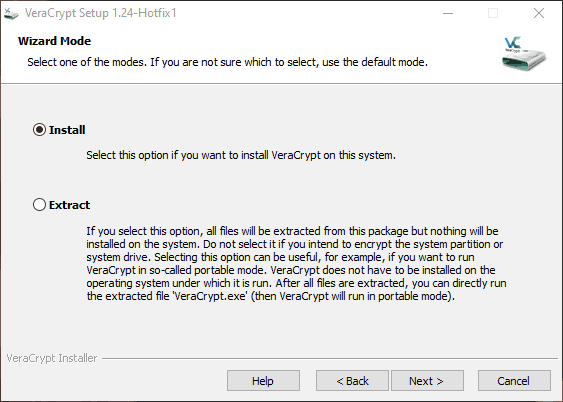
The installer is fairly basic, though it asks if you want to install or extract the files. For most people, installation is fine, but extracting can be useful for a portable configuration. If you extract the files, you can run VeraCrypt without actually installing it on the system. All you need to do is run the extracted executable.
Once the installer finishes, VeraCrypt will ask if you want to open the beginner’s tutorial, which we recommend. For a point of reference, creating a VeraCrypt container takes 19 steps, according to the beginner’s guide. None of the steps are hard, mind you, but the plethora of options can make finding where you need to go difficult.
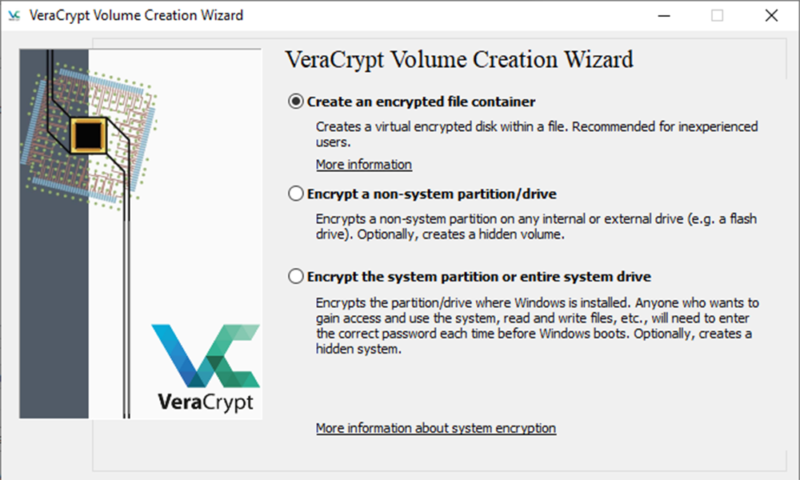
Although there are a lot of steps, the general process is simple, especially if you’ve created hard drive partitions. You can create new drive volumes, deciding to either create an encrypted file container, encrypt a system partition or encrypt a non-system partition, such as a secondary hard drive or flash drive.
For most people, creating a container is the best choice. VeraCrypt has a lot of options, but the volume creation wizard walks you through the steps with instructions along the way. Once you have your container created, VeraCrypt will ask you what encryption algorithm you want to use. On this page, you can also benchmark your CPU.
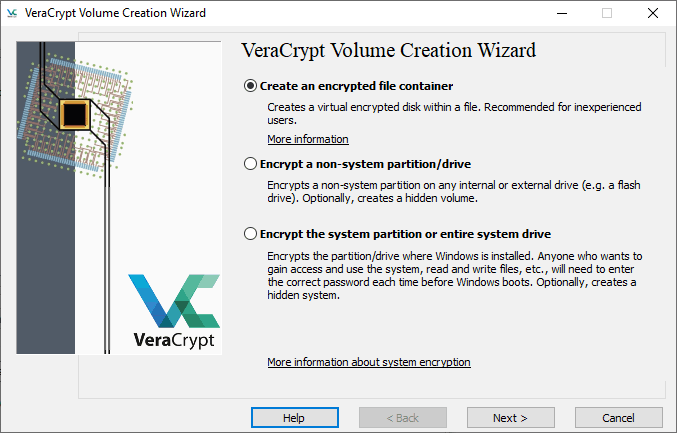
Finally, you’ll need to specify the volume size — either in kilobytes, megabytes, gigabytes or terabytes — and set a password. VeraCrypt will start generating the encryption keys based on your mouse movement, so make sure to keep it in motion.
VeraCrypt Volume Mounting and Encryption
With the volume created, you’re now ready to encrypt your files. The main window shows a list of available drive letters. You’ll have to right-click one and mount the volume you created to add files to the encrypted container. Once mounted, the volume will show up with the chosen drive letter in Windows Explorer.
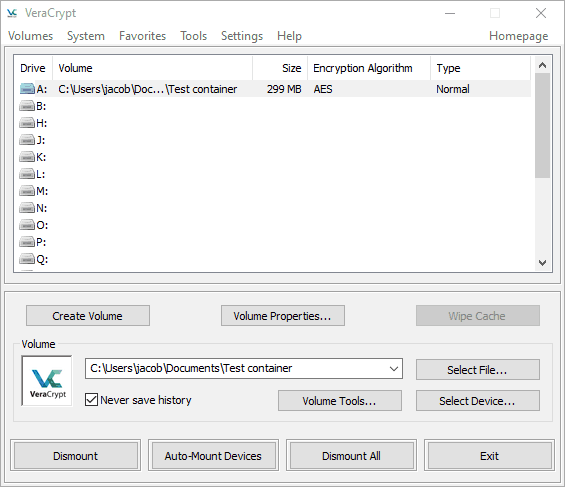
From there, it’s just a matter of dragging your files into the drive and dismounting it. Your files are always encrypted, but they’re decrypted in system memory as you’re using them, so you can edit any encrypted files without decrypting the entire volume.
VeraCrypt isn’t inherently difficult to use. In fact, the setup process is thoroughly explained, and dragging and dropping files into a mounted volume is a breeze. The options, from a usability standpoint, are the problem.
The interface can get confusing fast for those who don’t know what they’re doing, making more user-friendly options, such as NordLocker, more attractive for beginners (read our NordLocker review).
File Sharing & Storage
VeraCrypt misses out big in this section. It doesn’t have sharing features or cloud storage integrations. It’s a tool built for encrypting files locally, nothing more. If you have a cloud storage service, you could easily drop the volume there and sync it with collaborators, but there’s no direct integration.
Although VeraCrypt is a free service — and a good one, at that — the limited scope of it shows through here. Compared to a service like AxCrypt, which costs money, VeraCrypt falls short in the sharing department (read our AxCrypt review). The focus is in a different area.
It depends on your needs, but it’s undeniable that VeraCrypt is lacking when it comes to sharing. That said, if all you’re concerned with is encrypting locally or encrypting your entire OS, it’s still a fine choice.
Support
As is the case with most open-source software tools, you’re at the mercy of the community when it comes to support. The VeraCrypt team provides extensive — and we do mean extensive — documentation on the application, including a wonderfully written beginner’s guide. However, much of the other documentation is very technical.
If you’re a cryptography newbie, most of the articles will go over your head. The VeraCrypt team has no problem getting into the weeds, which is great from a tech standpoint but bad from a usability one. Like the local application, the documentation is all about giving you the resources and asking you to make sense of them.
There’s also a forum that serves as the only direct form of support. Thankfully, the community is active, and the VeraCrypt developers reply and create threads often. Looking through the recent threads, we were surprised at how helpful most of the community is. There are, of course, some bad eggs, but most threads had thoughtful and helpful discussion.
As far as support goes for an open-source project, VeraCrypt has a solid community. That said, it can’t stand up to the full support systems offered by paid software tools. If you need some handholding throughout the encryption process, VeraCrypt isn’t for you. However, if you’re competent in tech in the slightest, the community can probably help you along.
The Verdict
VeraCrypt isn’t a particularly marketable encryption service, but that’s not really its aim. Although lacking in support and file sharing capabilities, compared to its commercial counterparts, the service still shines when it comes to local encryption. If you don’t mind getting in the tech weeds and you fancy free, open-source software, VeraCrypt is for you.
Do you plan on downloading it? Let us know about your experience in the comments below and, as always, thanks for reading.
VeraCrypt FAQ
- VeraCrypt is a free, open-source encryption software tool. It’s focused on local encryption as a fork of the popular TrueCrypt software. With it, you can encrypt local files and folders, as well as entire hard drives.
- VeraCrypt has multiple encryption and hashing algorithms, allowing you to customize your protection. Because it’s a local-focused solution, there’s less risk with VeraCrypt than there is with a cloud-based encryption service.
- You can download VeraCrypt from veracrypt.fr. From there, install the program, create a new volume, mount that volume and drag the files and folders you want to protect.