Is NordVPN Safe To Use in 2025? VPN Provider Security
NordVPN’s 2018 server breach dented its reputation as a security juggernaut and put the provider under increased scrutiny. If you aren’t sure about NordVPN’s security, keep reading as we tackle the question: Is NordVPN safe?
NordVPN has some advanced security features that rank it among the best VPN providers. However, we’ve learned from experience that having all the security features doesn’t always make a VPN provider secure. To answer the question “is NordVPN safe,” we dissected the provider’s security infrastructure and technologies, and we compiled our findings in this guide.
We’ll walk you through NordVPN’s basic and advanced privacy and security features. We performed a series of DNS and IP leak tests to confirm that the features work as they say on the tin. Keep reading to learn how NordVPN fared and whether it has the seal of approval from third-party audits. If you like what you see, you can give NordVPN a spin risk-free using its 30-day money-back guarantee.
-
02/27/2024 Facts checked
Article rewritten with up-to-date information and features.
NordVPN Security Overview: Is NordVPN Safe?
The short answer is that NordVPN is safe. Over the years, NordVPN has perennially ranked as one of the most secure VPN services, thanks to its secure protocols, encryption standards and strict no-logs policy.
To help you better understand NordVPN’s security, we’ll analyze the following aspects of the provider’s infrastructure:
- VPN apps (certificates along with security and privacy features)
- Underlying technology (via third-party audits)
- Server infrastructure
We have rigorously analyzed the NordVPN app, and this guide is based on its performance during our testing and analysis. We’ll also bring NordVPN’s independent audits into the picture so that you can understand the provider’s security from the perspectives of reputable third-party security firms.
1. NordVPN Security Analysis
NordVPN offers basic and advanced security features, but do they function well enough to guarantee user privacy and security online? Let’s find out.
VPN & Encryption Protocols Used
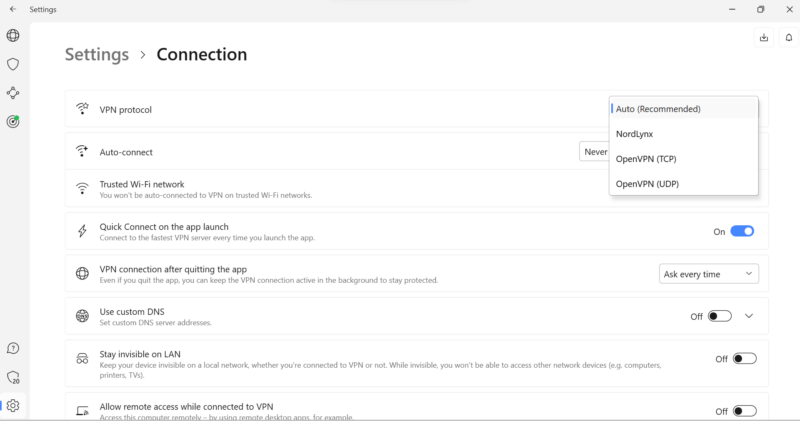
NordVPN offers the following protocol-encryption combinations:
| Protocol | Encryption | Devices |
|---|---|---|
| OpenVPN | AES 256-bit | Windows Android Mac iOS Linux |
| NordLynx | ChaCha20 | Windows Android Mac iOS Linux |
| IKEv2 | AES 256-bit | Windows Android Mac iOS Linux* |
A VPN protocol creates a tunnel that establishes a secure connection between networks. The encryption cipher turns internet traffic into ciphertext, making it difficult for internet service providers (ISPs), snoopers, hackers and other bad actors to monitor it. Protocols differ in terms of security and speed.
OpenVPN and AES 256-Bit Encryption
Open Virtual Private Network (OpenVPN) is arguably the most secure VPN protocol. It has stood the test of time and has been patched up to withstand nearly all (if not all) known cyberattacks.
NordVPN supports OpenVPN TCP, which offers better speeds, and OpenVPN UDP, which prioritizes security.
OpenVPN uses the Advanced Encryption Standard (AES) 256-bit cryptographic algorithm. AES is the gold standard in encryption, with no known ways to decrypt the plaintext or data it encapsulates.
NordLynx and ChaCha20 Encryption
NordLynx is NordVPN’s proprietary protocol built around the WireGuard protocol. The newer, lightweight protocol is very secure but isn’t as tried and tested as OpenVPN. NordLynx uses ChaCha20, which is reliable because its algorithm generates a 256-bit key combination.
IKEv2 and IPsec Encryption
IKEv2 is no longer available on NordVPN’s apps, but you can set it up manually on any device. The secure protocol works with various cryptographic algorithms, including IPsec and AES 256-bit. Its stability and excellent compatibility with networks make it ideal for mobile users.
Advanced Security Features
Beyond the protocols and encryption, NordVPN offers advanced security features to enhance your security:
- Kill Switch: NordVPN has an internet kill switch that disables your internet connection when the VPN connection drops, ensuring no accidental traffic leaks expose your identity or IP address. There’s also an app kill switch that quits selected apps to prevent them from making unprotected connections.
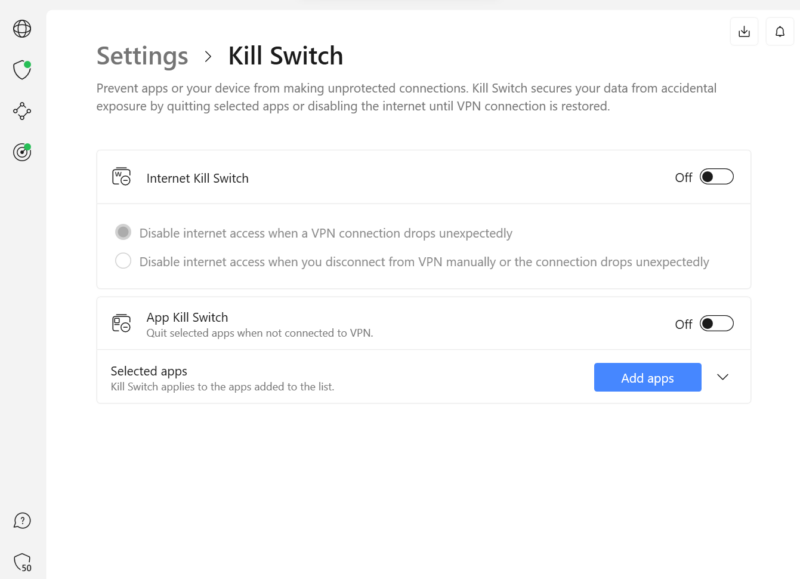
- Perfect Forward Secrecy (PFS): With perfect forward secrecy, the NordVPN app randomly generates encryption keys for each session. Even if hackers get hold of one key (which is still highly unlikely), they will only decrypt one session rather than your entire browsing history or communications.
- Double VPN: The double VPN routes your traffic through two servers in different locations, each encrypting it separately. The extra layer of protection makes it hard for even the most skilled hackers to know your real IP address and identity. Even the government’s most advanced deep packet inspection system wouldn’t be able to trace any online activity back to you.
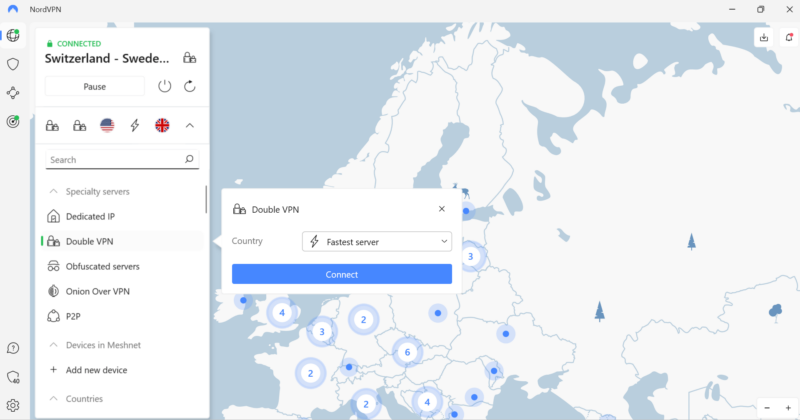
- Obfuscated Servers: These servers scramble the VPN metadata from your encrypted traffic, making it look like regular web traffic. As a result, you can use a VPN in countries where the software is banned, and the authorities won’t know about it.
- Dark Web Monitor: This tool scours dark web marketplaces for data linked to your email address and alerts you when it finds a hit.
- Threat Protection: This feature protects you against ads, trackers and malware. You can configure it to notify you when it detects a vulnerable file or application on your device.
DNS, IP and WebRTC Leak Tests
A DNS leak test helps determine whether NordVPN’s security features work as intended. During our testing, we selected a NordVPN server in each continent, and they all came out clean. While seven servers out of NordVPN’s total of over 6,000 servers isn’t an ideal sample size, the results prove that the provider’s security features work.
| NordVPN Server: | DNS Leaks? |
|---|---|
| 🇺🇸 U.S. | |
| 🇺🇲 U.K. | |
| 🇧🇷 Brazil | |
| 🇦🇺 Australia | |
| 🇸🇬 Singapore | |
| 🇮🇱 Israel | |
| 🇿🇦 South Africa |
Security Audit Results
The security firm Cure53 examined NordVPN’s underlying technologies, servers and desktop apps in 2022. A statement in the report says, “The components under scrutiny have garnered a relatively strong impression.” Simply put, the components passed Cure53’s penetration tests and can be relied upon to deliver top-notch online security.
2. NordVPN Privacy Analysis
In this section, we’ll discuss NordVPN’s no-logs policy claim. As we have seen, NordVPN protects your personal information and data from external threats: hackers, ISPs and other malicious actors. But does it protect your data from internal actors, including the VPN itself?
Remember that the VPN provider can peek at certain aspects of your internet activity if it feels so inclined. This is why it’s crucial to read NordVPN’s logging policy and understand how it handles user data.
NordVPN No-Logs Policy
According to NordVPN’s privacy policy, the provider adheres to a strict no-logs policy. It doesn’t collect, store or share your browsing history, logs, IP addresses or traffic information.
However, NordVPN collects metadata such as device information, device identifiers, interaction data and timestamps of your last session status when you use the website and apps. Luckily, this data doesn’t reveal any identifying information.
Under the “request for data” section, NordVPN claims to carefully review every request for user data. It may honor data requests that satisfy the laws applicable to Panama, where it is based, along with those of the requesting party’s country of origin and relevant international laws. Even so, NordVPN would have no identifying information to share since it keeps no user logs.
used to single out specific VPN users.
NordVPN’s Jurisdiction
NordVPN is based in Panama, a privacy haven with no mandatory data retention laws. No laws compel the VPN to store logs of users’ online activities. Even better, the country isn’t part of any surveillance alliance, meaning NordVPN isn’t obliged by any binding agreement to share user data across the border.
Privacy Audit Results
In 2023, NordVPN sought the help of Deloitte to audit its no-logs statement. The independent auditors scrutinized NordVPN’s server configuration, infrastructure and technical logs. In its report, Deloitte confirmed that NordVPN doesn’t keep user logs, validating the no-logs claim.
NordVPN Security Breach
In 2018, NordVPN suffered a security breach caused by a vulnerability in one of its third-party data centers in Finland. The fact that the server breach happened in the first place is a strike against NordVPN’s security record.
The silver lining is that the perpetrators of the server breach didn’t find any data on the server. The incident proved that NordVPN abides by its no-logs policy.
NordVPN’s Server Technology
In the aftermath of the server breach, NordVPN started upgrading its VPN server technology from hard disk to diskless servers (also known as RAM-based servers).
The new technology centralized NordVPN’s server infrastructure. As a result, the servers’ operating systems and other necessary software are hosted in a secure central infrastructure. This put NordVPN in charge of its entire server infrastructure, including those operated by third-party providers.
The diskless server technology also renders the servers as empty pieces of hardware. Even if a hacker or government agency infiltrates or seizes a server, they will find no data or configuration files.
3. ioXt Certified Apps
Another reason to trust NordVPN is that its apps are ioXt certified. ioXt measures software through eight principles geared towards validating the level of security. Apps must meet the minimum requirements and follow ioXt security regulations to earn the certification.
NordVPN’s Android app is ioXt certified, which means it offers excellent levels of security. The good thing is that the certification is renewed annually, so there’s no room for security laxity on the vendor’s end.
Login Credential Protection
Beyond the ioXt security guarantee, NordVPN uses the SHA-512 hash function for password verification. The SHA-12 cryptographic hash converts and stores a plaintext password into a unique hash digest.
Since password hashing is one-way and irreversible, a plaintext password will always generate the same hash. As a result, a person with a different password can’t log into your account, no matter how close the fake password is to the real one.
NordVPN’s choice to use SHA-512 over SHA-256, the VPN industry standard, is probably fueled by the need to maximize user security. SHA-256 strikes a nice balance between security and speed, whereas SHA-512 goes all in on security.
NordVPN for Torrenting: Is It Safe?
Yes, NordVPN is safe for torrenting. The provider offers peer-to-peer (P2P) servers dedicated to P2P file sharing, like torrenting. Thanks to its solid security, it masks your real IP address, hiding it from other peers in a torrent swarm. Learn more in our NordVPN torrenting guide.
The servers also hide your torrenting activity from internet service providers, thwarting ISP throttling — where the ISP slows down your connection when you engage in bandwidth-heavy activities. Threat Protection prevents malicious files and vulnerable software served by peers from harming your device.
Final Thoughts: How Safe Is NordVPN?
Taking all things into consideration, it’s fair to say NordVPN is safe to use. The 2018 server breach blemished its reputation. Thankfully, the provider learned valuable lessons from it and devised new technologies to strengthen its security.
When you connect to a NordVPN server, the basic and advanced features spring to action to protect you online. Its solid encryption and protocols prevent hackers, ISPs and government agencies from peeking at your internet activity.
With Threat Protection, you can relax knowing that ads, trackers and malware won’t find a way into your device. Besides adhering to its no-logs policy, it has implemented diskless servers to prevent user data from getting exposed in case of a server breach or seizure. Learn about other NordVPN features in our full NordVPN review.
To get a first-hand feel for NordVPN’s security capabilities, try the two-year plan, which costs $3.01 per month. You won’t get a more secure VPN service for that price. There’s a 30-day money-back guarantee in case you change your mind.
FAQ: Is NordVPN Safe?
Yes, NordVPN is trustworthy, thanks to its robust protocols, encryption standards and strict no-logs policy.
Yes, your data is safe with NordVPN. Deloitte has audited NordVPN’s no-logs policy and verified that the VPN company doesn’t collect, store or share user logs.
It’s difficult to be tracked when using NordVPN. The VPN provider uses secure protocols and encryption ciphers, making it virtually impossible for anyone to see your real identity or what you do online.


