Cryptomator Will Provide Quantum-Resistant Encryption Protection to Any Cloud Provider
Cryptomator, an open-source encryption software, will expand its client-side encryption services to include quantum-resistant cloud protection.
Skymatic GmbH, the developer of Cryptomator, announced today its plan to incorporate post-quantum cryptography into Cryptomator’s encryption protection so that it can secure data against both quantum and classical computers.
Security experts have increasingly voiced concerns about the threat quantum computing poses to widely used encryption algorithms, such as RSA and Elliptic Curve Diffie-Hellman (ECDH). Quantum computers can solve complex problems much faster than classical computers because they use quantum bits or qubits, rather than binary bits.
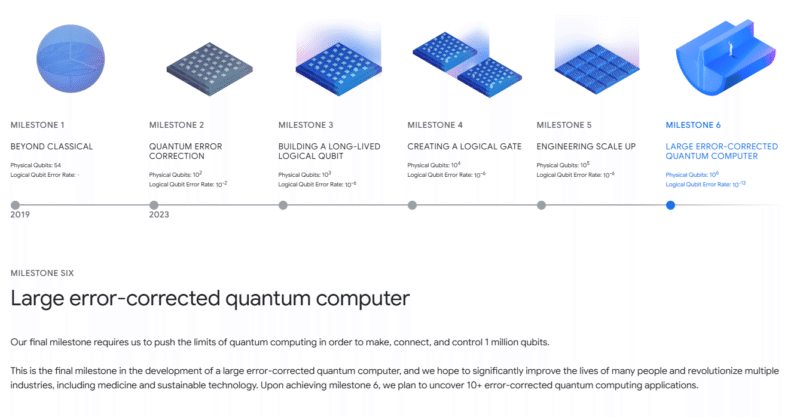
In May 2025, Google’s research team announced that it found “2048-bit RSA encryption could theoretically be broken by a quantum computer with 1 million noisy qubits running for one week” — a 20-fold decrease in qubits from the previous 2019 estimate.
Although the most advanced current quantum computers range between 100 and 1000 qubits, this number has rapidly increased in recent years, with Google itself aiming for a million-qubit quantum computer by 2030.
Algorithms that are particularly vulnerable to quantum computing are RSA and ECDH, which are used for encryption in transit (messaging, HTTPS) and digital signatures (software authenticity, website identity), according to Google’s research. Symmetric encryption, like AES, is less affected.
Even though quantum computers capable to breaking encryption are likely years away, it still poses an immediate threat. The security threat implications are that cybercriminals could use a “store now, decrypt later” strategy, where they collect encrypted data and store it until they have the means to decrypt it in the future with quantum computing.
“Although quantum computers are not yet capable of cracking the key lengths used today, the time to act is now,” said Sebastian Stenzel, CTO of Skymatic, in a statement. “‘There is no glory in prevention’ also applies to IT security.”
Cryptomator created its quantum-computing protection by integrating its existing client-side encryption with cryptographic algorithms, including both the NIST standards (ML-KEM and ML-DSA) and X-Wing, a combination of classical and post-quantum-secure algorithms. In 2025, these new cryptographic features will be integrated into the Cryptomator Hub, a service for teams and businesses.
With the goal of ensuring “maximum compatibility and cryptographic agility,” according to Skymatic, the “Cryptomator team is also working on integrating the HPKE (Hybrid Public Key Encryption) standard based on X-Wing, and on adapting the JWE (JSON Web Encryption) format used to transmit encrypted user data.” The Cryptomator code will remain open-source.
How Cryptomator’s protection would work is that users would download the Cryptomator Hub and set up a Cryptomator “vault” folder within their existing cloud storage service, like Dropbox and Google Drive. Saving files into the Cryptomator vault will add the quantum-resistant client-side encryption.
Very few cloud storage services currently implement quantum-resistant cryptography into their client-side encryption, with Proton Drive and Internxt being two we can recommend; read our Proton Drive review and Internxt review for more information.

