What Is Quantum-Resistant Cryptography? Explained for 2026
Quantum-resistant cryptography is a new algorithm built to withstand the power of quantum computers. This is essential, as current encryption is becoming increasingly vulnerable. We explain how this new cryptography works and how it’s being implemented to secure our data.
Quantum-resistant cryptography — also known as post-quantum cryptography — is a new kind of encryption built to protect data from the power of quantum computing. Traditional encryption methods rely on math problems that existing systems struggle with, but quantum computers will have no issue solving these problems.
Without post-quantum cryptography, today’s encrypted data could be stolen and decrypted in the future. Governments, tech companies and security services like NordVPN and Internxt are developing and implementing algorithms to resist quantum attacks. In this article, we’ll break down what quantum-resistant cryptography is, why it matters and how it will protect our data.
The Privacy Dangers of Quantum Computers
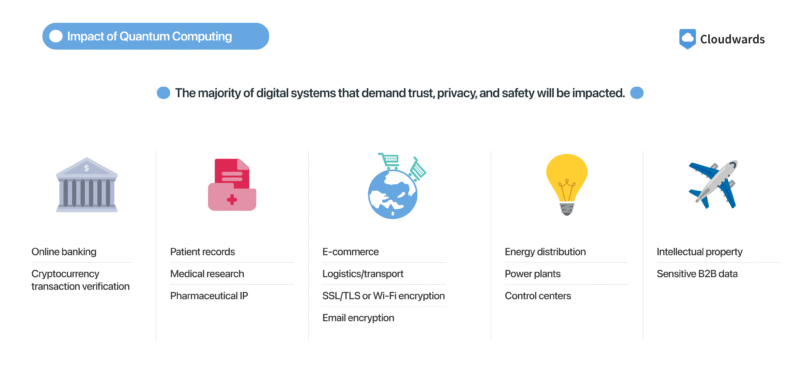
and the data those standards protect.
Quantum computers will not only be faster than the machines we have now but will also be capable of solving problems that are currently impossible, including breaking the encryption that protects our data and online privacy today. This means everything that’s currently protected — bank details, emails, even government secrets — is at risk.
The biggest danger is that quantum attacks can happen retroactively. Hackers can steal your encrypted data today and simply wait until quantum technology catches up. Then, they can unlock information you thought was secure. This is why experts are pushing for post-quantum cryptography now, before quantum computing becomes mainstream.
What Is Q-Day & When Will It Come?
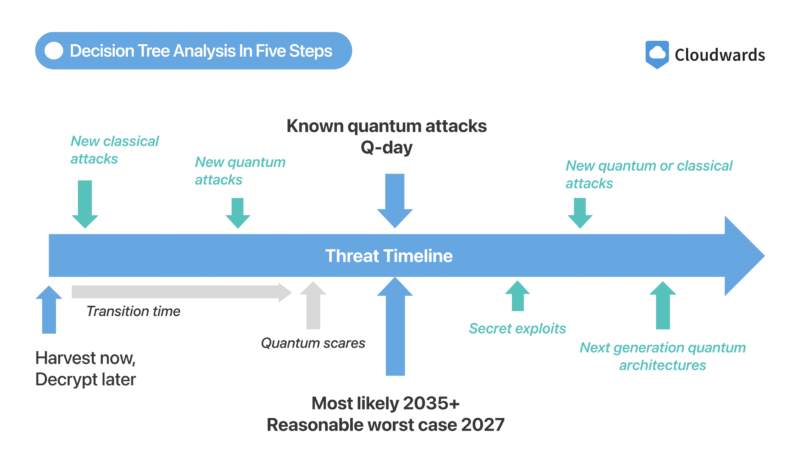
Q-Day is the name given to the moment quantum computers become powerful enough to break modern encryption. No one can say exactly when it will happen — some experts suggest within the next 10 to 20 years, but it could be even sooner if there’s a breakthrough.
The uncertainty around Q-Day’s arrival is what makes it so dangerous — there’s a chance it could happen before we expect it, and by that time it’ll be too late to make any meaningful change. Many organizations, like IBM and the NIST (the National Institute of Standards and Technology), are already preparing for a post-quantum computing world. 1
In 2024, NIST selected three official post-quantum cryptography standards. These are CRYSTALS-Kyber for encryption and key exchange, CRYSTALS-Dilithium for digital signatures and SPHINCS+, a hash-based alternative.
These algorithms are designed to replace the weak points in today’s cryptographic systems, ones that quantum computing will be able to exploit. By developing and implementing them today, we gain a crucial head start before Q-Day becomes a reality.
PQC Meaning: What Is Quantum-Resistant Cryptography?
Quantum-resistant cryptography, also known as post-quantum cryptography (PQC), refers to encryption algorithms designed to withstand the threat of quantum computers. PQC uses mathematical problems that are hard for computers to solve, unlike traditional encryption, which quantum algorithms like Shor’s algorithm can break.
The key to PQC is that it doesn’t use quantum technology itself. Rather, it’s a new kind of encryption built to resist quantum attacks. The goal is for PQC to replace the systems we use today, which classical computers can break. Organizations like the NIST are already working on making PQC the new standard for secure communications. 2
What Is the Purpose of Post-Quantum Cryptography (PQC)?
The main purpose of PQC is to keep data secure in a world where quantum computers exist and are fully functional. The encryption methods we use today are built on mathematical problems that regular computers struggle with. Quantum computers will be able to tackle these problems easily, though, meaning sensitive data is at risk of exposure.
Post-quantum cryptography stands up to quantum attacks, preserving the security of everything we protect today — online banking, government records, private records, health data and other information we keep secure. By switching to PQC now, we can avoid a future quantum era in which encrypted data can be exposed.
PQC & PKI (Public Key Infrastructure)
Public key infrastructure (PKI) is the framework that secures digital communications with encryption keys and digital certificates. This lets users exchange data over the internet safely, relying on algorithms like RSA (Rivest-Shamir-Adleman) and ECC (elliptic curve cryptography) that will become vulnerable to quantum attacks.
Post-quantum cryptography (PQC) doesn’t replace PKI. Instead, it addresses the weak points in the framework. It introduces quantum-resistant public key algorithms that plug into existing PKI systems without needing an overhaul. PKI and PQC can then work together — PKI handles trust and key distribution, while PQC strengthens the encryption keys.
Quantum-Resistant Algorithms
Quantum-resistant cryptographic algorithms are new algorithms designed to stay secure when quantum computing becomes powerful enough to break today’s encryption. These algorithms are being tested and adopted in sectors like government, finance, online security and cloud storage services. Let’s take a look at some of the top cryptography types.
Lattice-Based Cryptography
Lattice-based cryptography is a promising approach to quantum-resistant encryption. It uses complex geometric structures that are incredibly hard to solve, even for quantum computing, providing security against both classical and quantum attacks. These algorithms are ideal for tasks like key exchange, where it’s critical to securely transmit encryption keys.
One example is ML-KEM. This algorithm uses the structure of lattice problems to create mathematical “noise” that hides the original data. It’s extremely difficult to reverse without the correct key, even for quantum computers. This algorithm is already seeing real-world testing — ExpressVPN has recently integrated ML-KEM into its Lightway protocol.
Hash-Based Cryptography
Hash-based cryptography uses hash functions, which are mathematical tools that convert data into strings of characters. These are one-way functions — easy to compute but extremely difficult to reverse — so it’s hard for quantum computers to learn the input from the output.
This type of cryptography is useful for verifying the authenticity of messages or software updates. Hash functions like SPHINCS+ are a solid option for situations where long-term data integrity is important, such as verifying firmware updates or securing documents that need to remain protected for the foreseeable future.
Other Solutions
Other quantum-resistant methods include code-based cryptography, which uses error-correcting codes to create secure encryption, and multivariate cryptography, which relies on solving complex equations with multiple variables. These cryptographic systems are less widely used but play a valuable role in creating a diverse set of encryption tools.
By implementing a varied approach, researchers and developers gain greater flexibility to build resilient cryptographic systems. Some of these alternatives may prove especially useful as backup options or for specialized tools within post-quantum public key algorithms.
For example, Classic McEliece (a code-based scheme) has a strong security track record but also has large key sizes, making it less efficient for day-to-day encryption. However, it proves valuable in systems where performance is less critical but long-term data security is essential.
Final Thoughts
Quantum computers aren’t mainstream just yet, but the threat they pose to our current encryption standards is real and growing ever closer. Post-quantum cryptography offers a solution, replacing vulnerabilities in existing systems with quantum-resistant algorithms that strengthen security.
This shift is already happening — researchers, companies and government bodies like the National Institute of Standards and Technology (NIST) are working to develop cryptographic security systems that protect us from future quantum threats.
Do you think post-quantum algorithms will eventually replace classical ones completely? Are you concerned that Q-day will arrive sooner than experts predict? Has this article made post-quantum cryptography algorithms feel less mysterious? Let us know in the comments, and thank you for reading.
FAQ: Quantum-Safe Cryptography
“Harvest now, decrypt later” refers to hackers collecting encrypted data now with the intention of decrypting it with powerful quantum computers at a later date. Even if data is currently safe, it could be exposed once quantum decryption becomes possible.
AES (Advanced Encryption Standard) is more resistant to quantum attacks than other kinds of encryption, but it’s not completely safe from quantum computing. Larger key sizes like AES-256 offer stronger protection and are a better option to maintain security in a post-quantum world.
Quantum cryptography utilizes the laws of quantum mechanics to protect data. If someone tries to intercept messages, the algorithm changes in a way that reveals the attempted eavesdropping. This makes the system extremely secure.



