What is a Botnet? Networks Gone Bad
In our series on cybercrime, we’ve covered online threats such as ransomware, phishing and browser hijackers. This time, we’re going to look at one of the most potent threats online: botnets.
While you can’t get a botnet, you can be part of one. Botnets are networks of slave computers used to carry out a variety of tasks. They’re especially dangerous, too, as their goal is to live on your machine undetected for as long as possible.
We’re going to look into what botnets are, the ways they commit cybercrimes, their structures and how you can keep yourself protected. As with most cybercrime, staying vigilant while using the internet will take you a long way, but adding protection, such as a secure antivirus, will ensure you have all your bases covered.
What Is a Botnet?
A botnet is a system of computers that have been infected with malware. The term is short for “robot network,” the same way malware is short for “malicious software.” Botnets, then, are simply a collection of bots.
Bots allow the attacker to carry out many actions from the infected machine. In the ideal scenario, the infected user wouldn’t recognize the performance degradation and would go on assuming everything was normal. The goal of a botnet is to live undetected for as long as possible.
Larger botnets are more powerful, too. Usually, botnets suck system resources to do tasks that require many computers, which we’ll talk about in the next section. As the botnet grows, the share of resources each system has to use becomes smaller, making the bot more difficult to detect.
Because of that, botnets are less of a business concern. Attackers aren’t concerned with who they’re infecting, as long as the machine has a vulnerability that allows it to be infected. Once the desired number of machines is part of the botnet, the money-making engine begins.
Botnets can be very profitable, as large ones can operate for years without any hiccups. As with a browser hijacker, it’s easy for those unfamiliar with the scheme to fall victim to it. The bot can fly under the radar on your machine for a while.
Since they do their dirty work in the background, some people may not be worried about removing a bot from their machine. The malware poses serious threats, though, to your machine and others.
Dangers of a Botnet
Your machine will slow down, sometimes significantly. The tasks that botnets usually perform require lots of CPU power, which can make even basic web browsing feel sluggish. Botnet attacks can use basically any system resource, too, meaning you’re sharing your performance with a criminal.
As with most malware, botnets typically don’t come alone. They’re often delivered using a trojan, malware that looks like one thing, but contains something else.
There may be multiple malicious threats in the trojan, such as a keylogger that captures your login data or a RAT to spy on your webcam. You can read our best password manager guide to avoid that malware, though.
The goal isn’t to harm you, but that’s often a consequence. Instead, it’s to use you to harm others. Botnets can perform any task that can be scripted, but we’re going to go over the most common ones.
Botnet Attacks
Distributed Denial-of-Service Attacks
Botnets are perhaps most infamous for distributed denial-of-service attacks. The goal is to deny service from a web server. For example, a botnet could perform a DDoS attack against a popular website to crash it, denying users its service.
Attackers carry out DDoS attacks by sending a massive amount of traffic to the web servers, overloading their resources. When the servers can’t keep up, they crash. Attackers can keep the pressure on for a while, too, making it difficult for the server to get back online.
Botnets aren’t the only way a denial-of-service attack can be done, but they are the most effective. The “distributed” part refers to the botnet. Bots are coming from a large network of computers, making the traffic produced distributed.
DoS attacks can use spoof IP addresses and simulated traffic, but firewalls can usually catch and block them. Only the most insecure websites will be the target of this type of DoS attack.
Since botnets are on real machines, and have real IP addresses, it’s much more difficult for a firewall to detect that a DDoS attack is happening. The controller of the botnet sends commands to the network, forcing it to send traffic to the destination and crash the server.
Ad Fraud
Though it’s not as well known, botnets are used for ad fraud more often than DDoS attacks. The botmaster will send a small amount of the user’s data to an advertisement, faking the traffic that the ad is receiving.
The result is massive amounts of fraudulent ad revenue. Unlike a DDoS attack, which makes a single push, the goal of ad fraud is to last as long as possible. The botmaster only uses a small amount of resources across many computers, so users may never know their machine is being controlled.
Bots don’t take complete control of the browser like browser hijackers do, rather they take a small portion. That makes the bots less likely to be detected by the user and allows the botnet to keep going indefinitely.
Cryptocurrency Mining
Botmasters can also use their slave machine’s resources for cryptocurrency mining. Mining needs computing resources to solve hashes — small mathematical equations — and rewards those solving them with a small amount of cryptocurrency.
Similar to ad fraud, the goal is to gather a large network of computers and use a small amount of their resources to mine cryptocurrency. In most large botnets, the slave machines perform ad fraud and cryptocurrency mining.
One of the largest botnets is the ZeroAccess botnet, a P2P configuration (more on that later) that gathered 1.9 million computers. Symantec, the company behind Norton (read our Norton Security review) studied the botnet in 2013 to measure its impact.

From cryptocurrency mining alone, the botnet made over $2,000 per day. Symantec estimated it collected just shy of $800,000 in a year.
On top of mining, ZeroAccess performed ad fraud, which generated tens of millions of dollars in revenue. Symantec estimated that it used 488 TB of data per day for the ad fraud.
Users that were part of the ZeroAccess botnet had to pay, too. The electricity costs per user were around $110 extra per year. Across the entire botnet, an estimated $204 million was spent in electricity annually.
Botnet Ecosystem
Botnets are often gathered and sold on the dark web, too. Smaller botnets can perform actions such as social media blasts, while larger networks can be used to distribute malware to other machines.
The majority of botnet revenue comes from selling them. Those interested in carrying out a DDoS attack, for example, are unlikely to create the botnet themselves. They’ll just buy one.
The botnet ecosystem is scary because they can be used for just about anything. Tasks that benefit from a large network of computers are prime targets for cybercriminals. Using the computing power to send fraudulent messages on social media isn’t bad, but using a network to distribute ransomware is awful.
Botnet Structures
Botnets are mainly operated in two ways. The botnet grows through users downloading malware on their computer, but the structure the botmaster uses to deploy messages can differ depending on the botnet’s purpose.
Client-Server
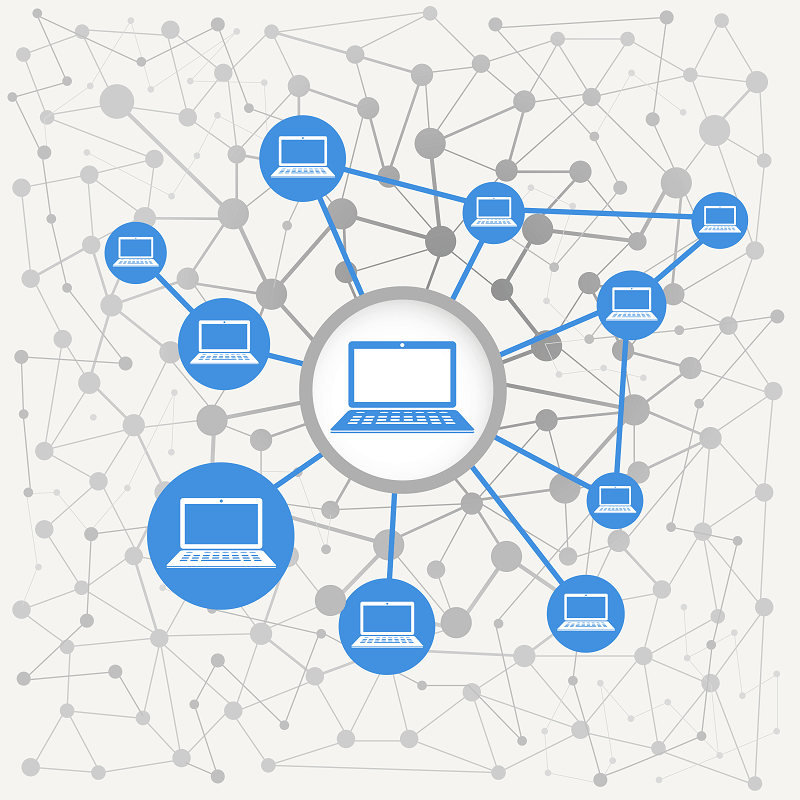
The client-server model puts the botmaster in the center of the botnet. They act like a server and the machines in the botnet act as the clients. The botmaster uses command and control software to transmit messages to each of the clients.
There’s an issue with the client-server model, though. It’s easier to set up, but it’s much easier to trace the botnet’s location. Simply draw a line back from one of the clients and you’ll find the server. Law enforcement can readily do so and destroy the botnet.
Even so, client-server models are used for lesser tasks such as social media blasts and small-scale ad fraud. It’s a simple model that enables botnets to be sold at lower prices or acquired more easily through distributed malware.
Peer-to-Peer
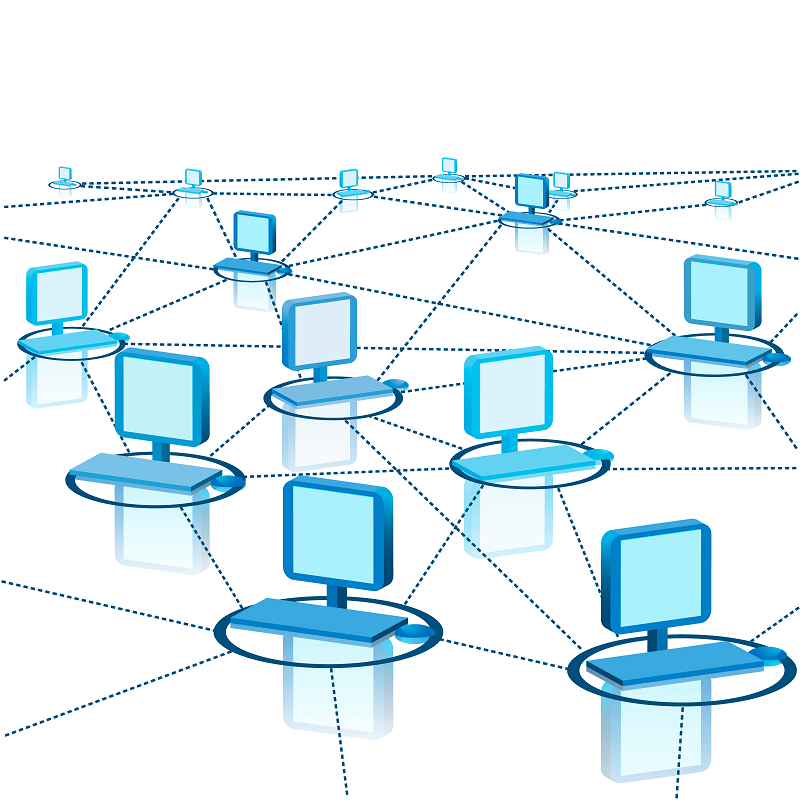
Newer, more sophisticated botnets rely on a peer-to-peer model. The client-server model establishes a centralized server, with all other machines acting as clients. A P2P structure, on the other hand, sets each machine in the botnet as a client and server, making it next to impossible to infiltrate.
You can’t just destroy the head of the beast, either. P2P botnets aren’t concerned with the individual. All that matters is the collective. Because of that, a few machines going offline won’t change the operations of the botnet.
What results is a massive web of interconnected machines. The botmaster, who maintains just one of the machines, can send instructions to any of the others in the network. Since they act as client and server, they can receive the message and pass it to the other machines in the network.
How to Protect Against Botnets
Botnets are, thankfully, easy to protect against and remove if you’ve already been caught in one. The most difficult part is figuring out you have one in the first place.
There are signs, though. If you’re noticing slower performance than normal or strange active processes, that is a sign your machine may be part of a botnet. A good way to verify there’s an issue is to regularly check Windows task manager to see what your resource usage ought to be.
Even then, you may not sniff out a botnet, especially a large one. Large botnets need so little from individual machines in the network that you won’t notice a performance change. That’s why running regular scans with the best antivirus software is so important.
Using an Antivirus
Our first pick is Bitdefender, not only for its excellent protection scores, but also for its simple-to-use interface and slew of features. Bitdefender can run deep scans on your machine that will find malware and remove it. You can learn more in our full Bitdefender review.
Since botnets require a network, a strong firewall is in order. Firewalls monitor network traffic and use a set of rules to determine what traffic is safe and what isn’t. Bitdefender has an excellent firewall, but we like Webroot’s, too (read our Webroot SecureAnywhere review).
Avast has a network analyzer, which can be helpful for identifying if you’re part of a botnet. While a full scan can usually find and eliminate the problem, it’s nice to visualize your connections for a sanity check. You can learn more in our Avast Pro review.
Any antivirus will help with prevention, as long as it has real-time monitoring. Many free ones don’t monitor what you’re doing, which can leave you vulnerable. As long as yours watches browser behaviors, applications, etc., you should be protected from most threats.
That doesn’t substitute for common sense, though. Avoid sketchy downloads, strange links in emails and clear attempts to steal your information or install malware on your machine. Botnets flourish on P2P and file-sharing networks, too, so try to avoid that as much as possible. You can check out our best VPN for torrenting to keep you safe there, though.
Thankfully, there aren’t many cases where you’ll need to wipe your machine and reinstall your operating system. Botnets thrive on size, so one machine won’t kill it. As long as you have a strong antivirus and are vigilant when using the internet, you should be fine.
Final Thoughts
Botnets are a threat because they can accomplish a diverse set of tasks. There are single use cases, such as depleting all system resources for a DDoS attack, as well as subtle examples, where small bits of bandwidth are used to commit ad fraud.
To keep your machine running smoothly and not take part in cybercrime, make sure you’re protected with an antivirus. We like Bitdefender, but you can choose another option from our antivirus reviews.
What are you doing to stay safe? Let us know in the comments and, as always, thanks for reading.


